A firewall is a hardware or software-based network security device that protects a network from unauthorized access by monitoring all incoming and outgoing traffic to accept, deny, or drop traffic according to predefined security rules. In Simple words, it is a barrier between a secure network and an untrusted network. Hacker use various methods to bypass firewalls. Below are some most popular methods which are used by hackers to bypass firewalls.
Encrypted Injection Attacks:
Encrypted injection attacks are commonly delivered via phishing emails. The email tricks users into clicking on a specific link that injects an encrypted code into their computer. This could be regular malware, fileless malware, or some kind of backdoor for data access. Phishing links can also ask users for their login credentials (or other sensitive information) and deliver encrypted payloads, a double hit against cyber criminals. Older software systems are not capable of properly inspecting and filtering encrypted traffic. His latest DPI-aware firewall is much more likely to deal with encrypted threats, but unidentified (“zero-day”) threats can still slip through the net. Fighting encrypted injection attacks is a great example of how cybersecurity training, modern firewall solutions, and strong antivirus protection work together.
IoT Attacks:
Software on IoT devices is often lightweight and poorly secured. For this reason, never connect your IoT device directly to the internet. No matter how small or harmless the device is. Always make sure you are securely “behind” firewalls, IPS, and other cybersecurity solutions you use.
SQL Injection Attacks:
SQL injection is a method by which hackers bypass a user’s system or database firewall by injecting malicious code (commands) of SQL. This is the most common method of web hacking used by hackers. Due to SQL injection attacks, hackers can retrieve all user data present in the database, for example, credit card information. Hackers can also change or delete data that exists in the database. Hackers design SQL statements to bypass databases or user system firewalls. Hackers inject and execute this malicious SQL statement when the web server communicates with the database server to transfer information.
For more details, Please refer to the article SQL Injection.
Application vulnerabilities:
Weaknesses or holes in the application which affect the security of the application are known as Application vulnerabilities. Hackers take advantage of this hole or weakness by bypassing the firewall. Once hackers discover a vulnerability in an application and how to access it, it is possible for hackers to exploit the vulnerability of the application to facilitate cybercrime. Therefore, it will be very important to manage and fix any bugs or vulnerabilities to protect the application from hackers.

Server Misconfiguration:
We all know that a server is a dedicated computer for a specific purpose and is designed to last longer than our regular desktop computers. Therefore, the server needs an up-to-date configuration file to protect the system from unauthorized access. Hackers always try to break into a misconfigured server because sometimes the server is left with default settings. This often leads to vulnerabilities that help hackers easily bypass server firewalls that provide a basic layer of security.
Social Engineering:
Social engineering takes advantage of human weaknesses and psychology to gain access to systems, data, personal information, and more. It is the art of manipulating people. No technical hacking techniques are used. Attackers typically use new social engineering techniques because it is easier to exploit the natural trustworthiness of their victims.
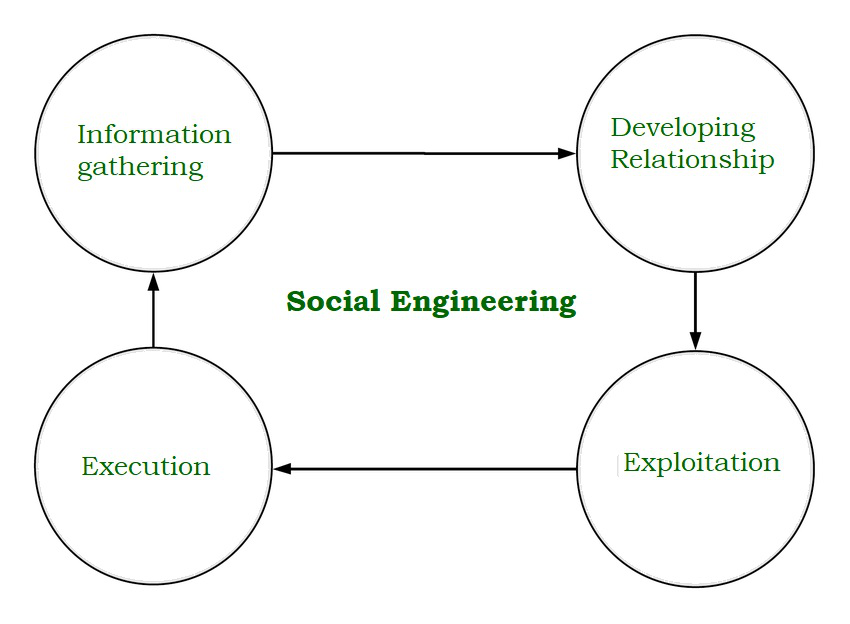
Phishing Attacks:
A firewall cannot protect against phishing attacks. Hacker uses phishing email to spread ransomware into the system, which bypasses network firewall security and infect the system.
- Hacker creates malicious ransomware file or link for getting access to the user system.
- The hacker emails a malicious file to the target.
- Ransomware automatically penetrates into the system when the target opens the attachment or clicks on the link.
- Once the ransomware encrypts the data and takes hold of the victim’s system, the hackers demand a ransom payment for the decryption key. Which is used to decrypt the encrypted system.
Preventive Measure:
- Back up your files regularly to reduce data loss.
- Always update your server configuration, software and operating system.
- Use up-to-date antivirus to secure your system and network from harmful viruses,.
- Never Click on attachments in emails from unknown senders.
- Avoid downloading different types of unknown files like archive files (.zip, .rar), etc., as attackers hide malicious programs in these file types.




