Prerequisite: Wireshark – Packet Capturing and Analyzing
Wireshark is a network protocol analyzer that captures packets from a network connection. It is a software tool used to monitor network traffic through a network interface. Wireshark can limit packet capture by capturing only those packets that match a capture filter.
Packet Capture or PCAP (libcap) is an API to capture live network packet data in Wireshark. libpcap allows us to capture or send packets from a live network device or a file. These PCAP files can be used to view TCP/IP and UDP network packets. Wireshark creates a .pcap file to organize and register packet data from a network. The capture filters of Wireshark are written in libpcap filter language.
There is a “Filter” field present in Wireshark’s “Capture Options” dialogue box where we can manually enter the capture filter.
Some Capture Filters:
1. Wireshark’s capture filter for telnet for capturing traffic of a particular host :
tcp port 23 and host 10.0.10.12
2. Wireshark’s capture filter for telnet for capturing all traffic except traffic from 10.0.0.5
tcp port 23 and not src host 10.0.0.5
Important Primitives:-
[src|dst] host <host>
This primitive helps us to apply filters on a host IP address or name. But if we need the source address or destination address, then we must specify src|dst before the primitive.
ether [src|dst] host <ehost>
This primitive helps us to apply filters on Ethernet host addresses. But if we require the source address or destination address, then we must specify src|dst between the keywords ether and host.
gateway host <host>
This primitive helps us to apply filters on packets that used the host as a gateway.
[src|dst] net <net> [{mask <mask>}|{len <len>}]
This primitive helps us to apply filters on network numbers. But if we want the source network or the destination network, then we must specify src|dst before the primitive. If our network number is different, then we can manually select the netmask or the CIDR prefix for the network.
[tcp|udp] [src|dst] port <port>
This primitive helps us to apply filters on TCP and UDP port numbers. But if we want the source port or the destination port and TCP or UDP packets, then we must specify the keywords’ src|dst and tcp|udp before the primitive. But one thing is that tcp|udp must appear before src|dst.
less|greater <length>
This primitive helps us to apply a filter on packets whose length is less than or equal to the specified length, or greater than or equal to the specified length, respectively.
ip|ether proto <protocol>
This primitive helps us to apply filters on the specified protocol at either the Ethernet layer or the IP layer.
ether|ip broadcast|multicast
This primitive helps us to apply filters on either Ethernet or IP broadcasts or multicasts.
<expr> relop <expr>
This primitive helps us to select bytes or ranges of bytes in packets by creating complex filter expressions.
Steps for Filtering while Capturing:
- For filtering packets start the Wireshark by selecting the network we want to analyze.
- Now in the “Filter” field type the filter primitive you want to apply while displaying the packets.
For Example :
tcp.port == 443 && ip.src == 192.168.29.52
The above display filter expression will set a filter for a specific port number and also sets a station filter that we specify.
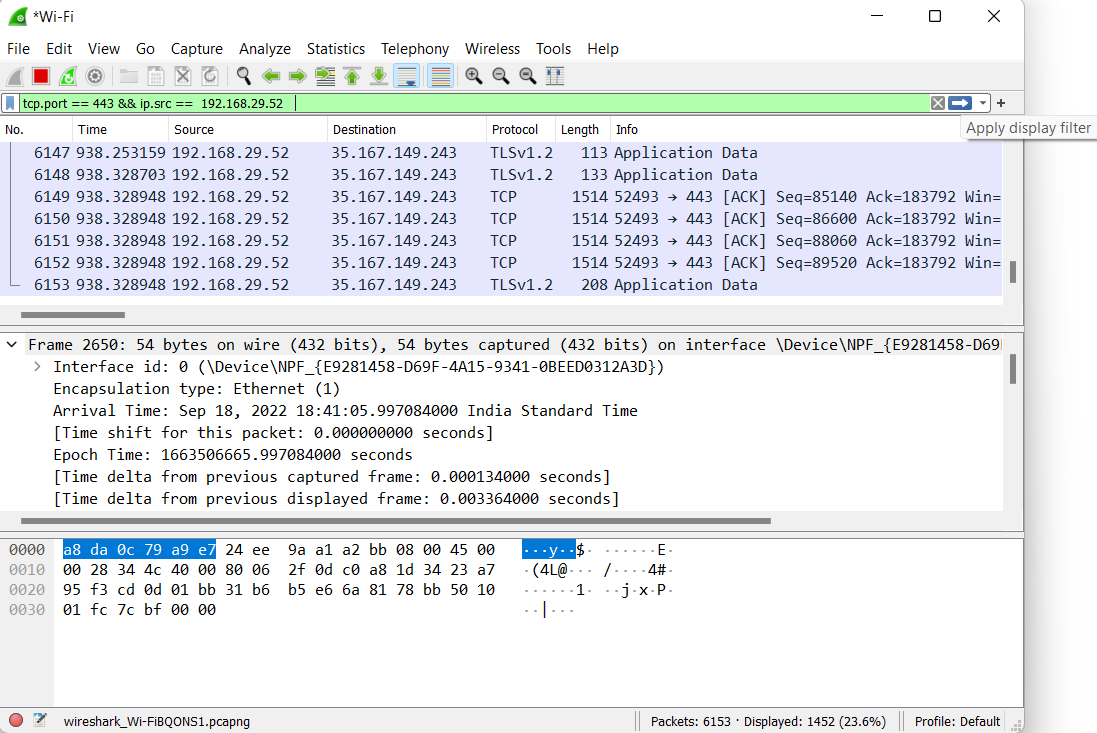
- Now click on the Blue colored arrow at the right corner of the “Filter” field to apply the filter.
Now we will notice that any time that when we get the syntax right then we will see that the background turns green. Now if we type something wrong then the background turns to be red. That tells us that Wireshark does not recognize that as an appropriate display filter syntax.




