TCP or Transmission Control Protocol is one of the most important protocols or standards for enabling communication possible amongst devices present over a particular network. It has algorithms that solve complex errors arising in packet communications, i.e. corrupted packets, invalid packets, duplicates, etc. Since it is used with IP(Internet Protocol), many times it is also referred to as TCP/IP. In order to start a communication, the TCP first establishes a connection using the three-way-handshake. TCP’s efficiency over other protocols lies in its error detecting and correction attribute. Not only this, it organizes packets and segments larger data into a number of packets without disrupting the integrity of the data.
So now we are a bit familiar with TCP, let’s look at how we can analyze TCP using Wireshark, which is the most widely used protocol analyzer in the world. In order to analyze TCP, you first need to launch Wireshark and follow the steps given below:
- From the menu bar, select capture -> options -> interfaces.
- In the interfaces, choose a particular Ethernet adapter and note down its IP, and click the start button of the selected adapter.
- Now we shall be capturing packets. Browse to a particular web address to generate traffic to capture packets from the communication for e.g. geeksforgeeks.org and return to Wireshark and stop the capture by selecting stop from the capture menu. You can have a look at it in the image below.
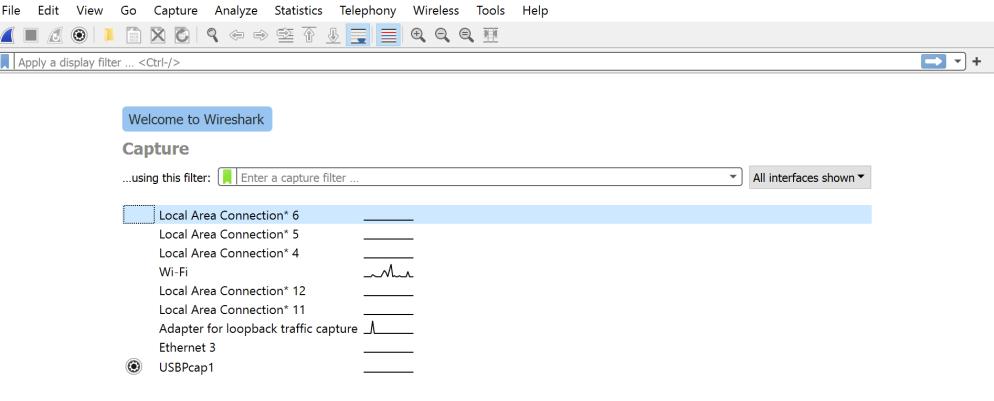
Now we have the captured packets and you will be having the captured packet list on the screen. Since we are concerned here with only TCP packets as we are doing TCP analysis, we shall be filtering out TCP packets from the packet pool. You can apply a filter in any of the following ways:
- In the display filter bar on the screen, enter TCP and apply the filter.
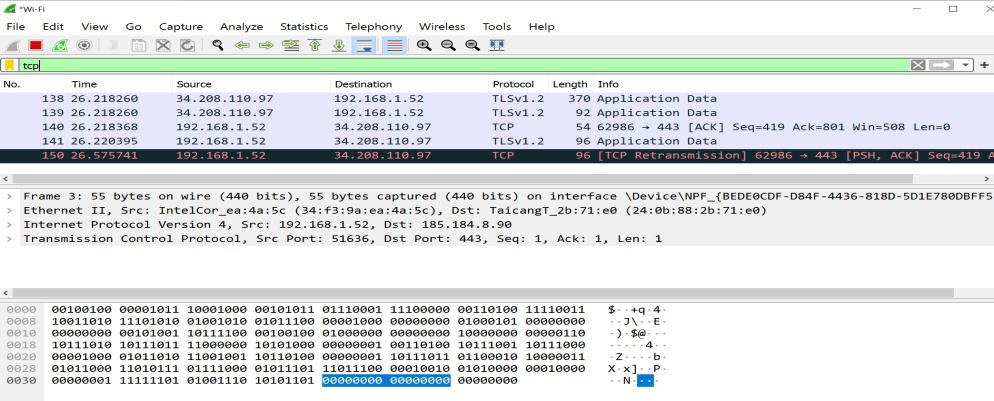
- From analyzing the menu in the menu bar select display filters or from capture select capture filters and then TCP only and ok.
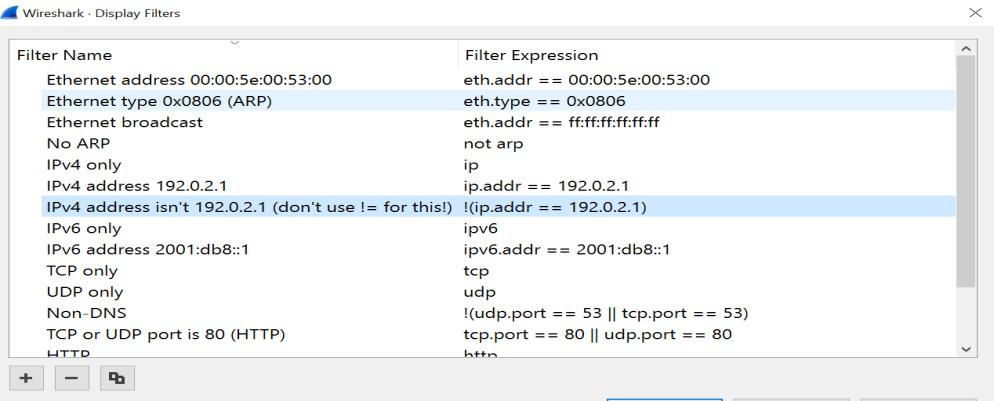
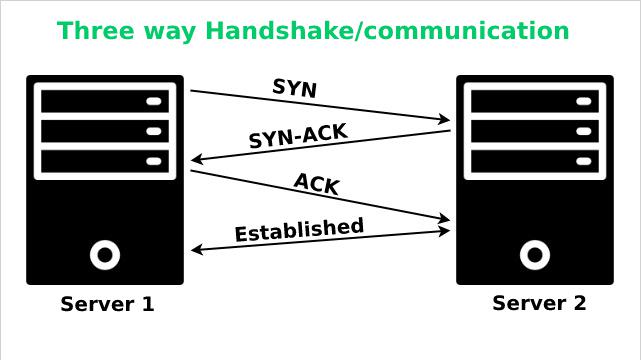
Here you will have the list of TCP packets. The first three packets of this list are part of the three-way handshake mechanism of TCP to establish a connection. Let’s get a basic knowledge of this mechanism which happens in the following 3 steps:
- A synchronization packet (SYN) is sent by your local host IP to the server it desires to connect to.
- The server reciprocates by sending an acknowledgment packet (ACK) to the local host signaling that it has received the SYN request of the host IP to connect and also sends a synchronization packet (SYN) to the local host to confirm the connection. So this one is basically an SYN+ACK packet.
- The host answers this request by sending the ACK on receiving the SYN of the server. You can understand it better by looking at the diagram below.
You can observe these three steps in the first three packets of the TCP list where each of the packet types i.e. ACK, SYN, SYN-ACK is listed on their respective side. Now to examine a packet closely we shall select a packet and in the expert view in the packet detail section just below the packet list we shall be having the TCP parameters as you can see in the below diagram. Let’s look at each one of them and their significance:
- Source port: This is the port of your host network used for communication.
- Destination port: This is the port of the destination server.
- TCP segment length: It represents the data length in the selected packet.
- Sequence number: It is a method used by Wireshark to give particular indexing to each packet for tracking packets with ease. This indexing starts from 0.
- Next sequence number: It is the sum of the sequence number and the segment length of the current packet.
- Acknowledgment number: It contains the byte length of data received.
- Header length: It is the length of the TCP header and can vary from 20 to 60.
A major section of this TCP packet analysis is the flag section of a packet which gives further in-depth information about the packet. The flag section has the following parameters which are enlisted with their respective significance.
- Congestion window reduced(CWR): It signals a decrease in transmission rate.
- ECN-Echo: It is set on receiving earlier congestion notifications.
- Urgent: It is set when the packet is to be considered a priority.
- Acknowledgment: It indicates whether the current packet contains an acknowledgment packet or not.
- Push: The data should be saved and removed from the communication channel.
- Reset: It indicates an error in the communication.
- Syn: It denotes whether the packet is synchronization or SYN packet or not.
- Fin: It indicates finalization i.e. end of the communication
Further, in the subsections we have:
- Window size value: This is the buffer size of the current host.
- Checksum: It is used to verify that the received packet is OK or has an error.
- Checksum status: The packet checksum is not verified by default, but one can enable it as per requirements.
Finally, after we have done the analysis it’s time to understand how the TCP connection is closed. It is commonly known as a TCP termination handshake. It further happens in the following steps:
- The closing side or the local host sends the FIN or finalization packet.
- The server sends an ACK signaling it has received the FIN packet and sends a FIN packet for confirmation on the closing side.
- Lastly, the closing side receives the FIN packet and reciprocates by sending the ACK packet thus confirming the connection termination. For a better understanding, you can have a look at the below diagram.




