SMB( Server Message Block protocol) is a client-server communication protocol that is used for sharing access to files, devices, serial ports, and other resources on a network. SMB enumeration is a multipart process in which we enumerate the host or target system for different information like Hostnames, List shares, null sessions, checking for vulnerabilities, etc.
SMB Enumeration Stages:
- Hostname enumeration
- List Share
- Checking Null session
- List users
- Vulnerability Scanning
- Overall Scanning
SMB Enumeration for Hostname
There are plenty of tools that can enumerate Hostname, here to demonstrate we are using nmblookup and nbtscan. Nmblookup tool makes use of queries of the NetBIOS names and maps them to their related IP addresses in a network.
1. Nmblookup:
$ nmblookup -A <Target IP>
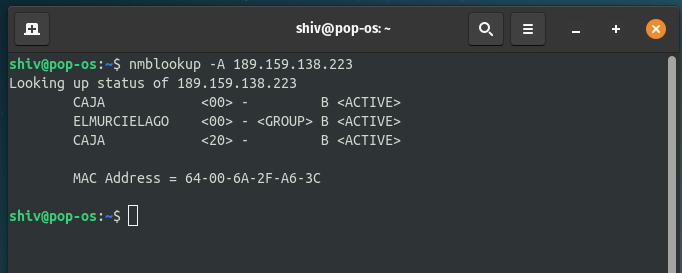
Here, you can see that we have enumerated the hostname to CAJA.
2. Nbtscan:
$ nbtscan <target IP>
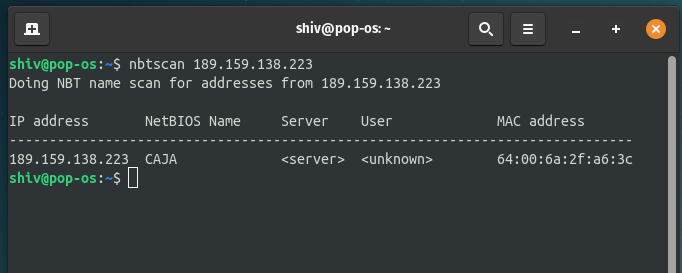
Here, you can see that we have enumerated the hostname to CAJA as the same as the above scan through nmblookup.
SMB Enumeration for Share and Null Session:
In this part, we are going to enumerate shares of the host or target system. We can perform this enumeration with many tools, for this article we are going to use smbmap, smbclient, Nmap, and Metasploit for different ways of performing this share enumeration.
1. Smbmap: Smbmap allows the attacker to enumerate samba share drives on the IP address. It also lists drive permissions and upload/download functionality.
$ smbmap -H <target IP>
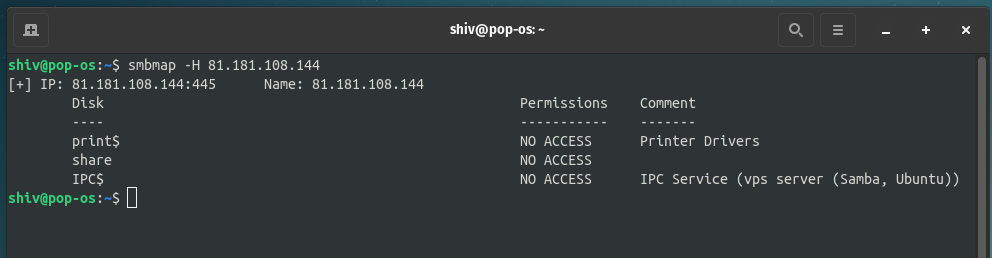
Also, you can scan for specific user shares using the credentials by using the below command
$ smbmap -H <target IP> -u username -p password
2. smbclient: It is a samba-client, and it is useful to test connectivity to windows shares.
$ smbclient -L <target IP>
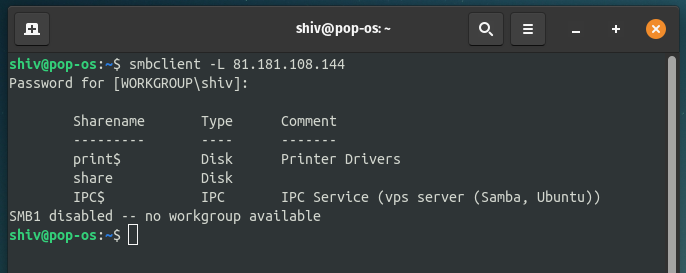
3. Nmap: Nmap provides smb-enum-shares NSE script which can be used to enumerate the shares.
$ nmap --script smb-enum-shares -p 139,445 <Target IP>
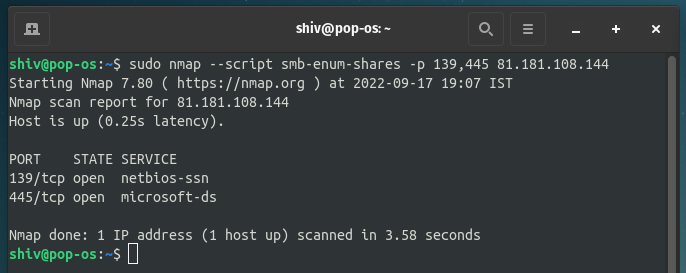
Here is the result as you can see that we didn’t find any SMB share detail.
4. Metasploit: In Metasploit, we are going to the smb_enumshares module that will enumerate any SMB share if present on the server.
msf6> use auxiliary/scanner/smb/smb_enumshares msf6> auxiliary(scanner/smb/smb_enumshares) > set rhosts <target IP> msf6> auxiliary(scanner/smb/smb_enumshares) > set smbuser <username> msf6> auxiliary(scanner/smb/smb_enumshares) > set smbpass <password> msf6> auxiliary(scanner/smb/smb_enumshares) > exploit
SMB Enumeration for Vulnerability Scanning:
In this stage, we use Nmap’s script for scanning for vulnerabilities that could possibly be found on the server. We can use various tools for this stage but here we are going to look at Nmap’s NSE script.
Nmap’s smb-vuln NSE Script:
Nmap has a wide range of scripts for different purposes, here as an example we are going to look at smb-check-vulns. This script can scan targets for a wide range of vulnerabilities, for example:
- a -3103
- regsv-dos
- ms06 -025
$ sudo nmap --script smb-vuln* -p 139,445 <Target IP>
Example:
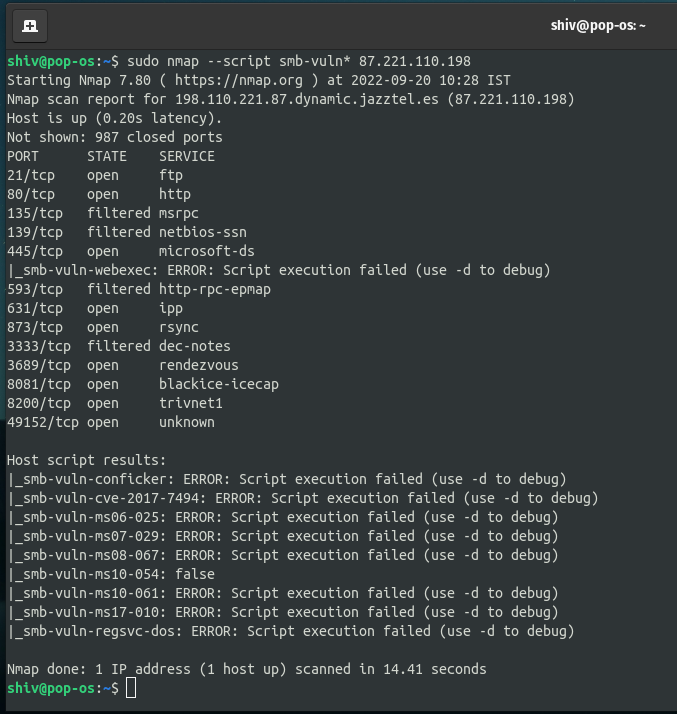
Result here we scanned the target for the specific script, and we didn’t find any vulnerability as we can see in the scan.
SMB Enumeration by Enum4Linux:
Enum4linux is a powerful tool that can detect and fetch data from both windows and Linux OS, also SMB hosts on the network.
$ enum4linux -U <target IP>
Example:
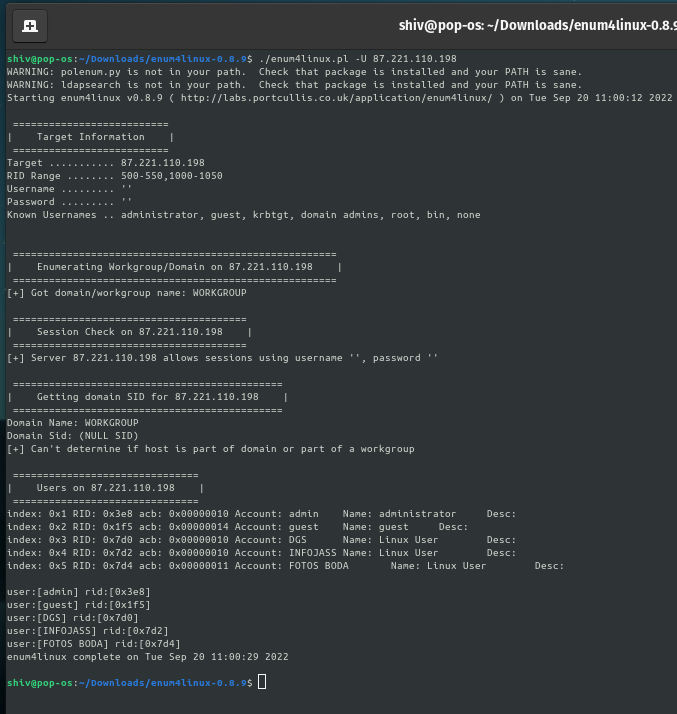
Result:
As we can see that it has enumerated all the user information that is present on the network.




