UDS Packet is a low-level transport protocol used on LAN‘s and WAN‘s to send packets between two endpoints. UDP Session Hijacking is an attack where the attacker tricks the victim into using their computer as part of a botnet, typically by sending them unsolicited requests disguised as coming from legitimate sources. This illegitimate traffic can then be used to exploit vulnerable systems or steal data. UDP session hijacking is a method of compromising a computer session by manipulating the session’s Transmission Control Protocol (TCP) traffic. The attacker manipulates the data sent over the network, which can then be used to hijack the session or steal information.
There are a number of risks involved with using UDP session hijacking in ethical hacking. Firstly, UDP packets are not encrypted and are therefore easier to capture and manipulate. This makes it easier for the attacker to steal data or hijack the session. Additionally, the attacker has control over the data being sent, which means they can tamper with it in a number of ways. This could allow them to steal information or modify it in order to exploit the system.
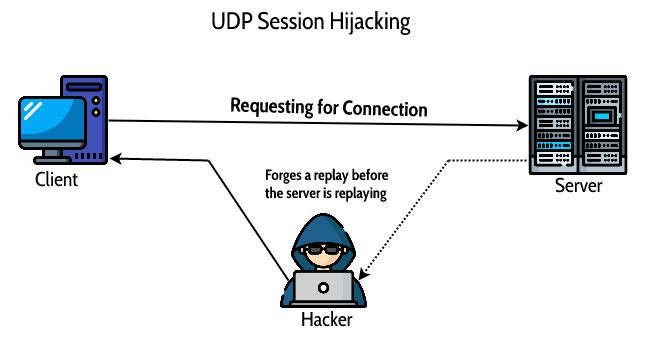
UDP Hijacking Attacks:
- One of the most powerful hackers will hijack a UDP broadcast. This allows them to steal data like passwords and credit cards.
- The attacker, who can be someone nearby or halfway around the world, accesses the information by sending out a false reply to the victim’s communications request to an application that uses UDP as its transport protocol.
- This is possible in Windows XP, Windows Vista, Windows 7, and Windows 8 operating systems.
- UDP packets are accepted by default on most versions of Microsoft operating system since XP. It is a default setting for anyone using an application on this operating system. Since these packets are not verified by the operating system, a hacker can send one reply to another legitimate user’s request.
- This allows the hacker to receive any useful data like passwords and credit cards from the unsuspecting user. This is dangerous because no one notices anything unless the session gets degraded or broken because of a lack of response from the server.
- If firewall protection is in place, it will notify the user and block any unauthorized incoming packets.
A Scenario of UDP Session Hijacking:
- In UDP session hijacking, an attacker doesn’t need features like Transmission control protocol, for example, sequence numbers and ACK mechanism to do session hijacking.
- These attacks took place in the wild back at the beginning of 1995. In this attack, an attacker is concerned about the connection between terminals.
Examples of UDP Session Hijacking:
We can use netcat on Kali-Linux to perform UDP Session Hijacking.
Step 1: Open terminal on Kali Linux
Step 2: Type the following command to communicate with UDP Server.
nc -z -v -u [Localhost Address] [ add UDP port]
Output:
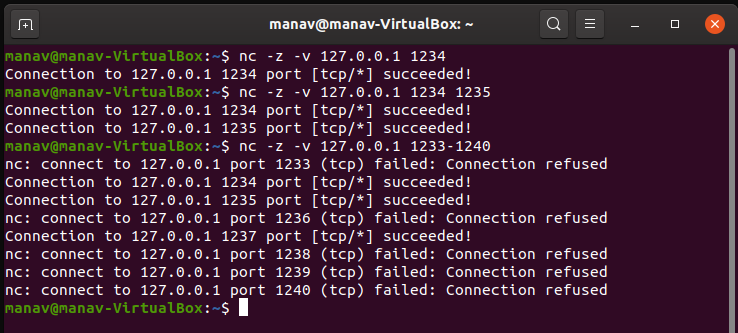
Basic Help Command:
Conclusion:
UDP hijacking is a new type of attack that can help malicious people steal valuable data from unsuspecting users. This is dangerous because it does not leave any trace or sign of the attack except for an unresponsive program. It is expected that this type of attack will become more known as the number of devices gets connected to the Internet and reach an expected 50 billion by 2020.




