Looking at the OSI model, it’s evident that more than a few security protocols are required to be fully protected. All potential access points and sites where hackers could obtain access to your network, data, and organization must be carefully considered.
Let’s look at the 7 levels in more detail, how they are vulnerable, and what we can do to secure them with different security strategies.
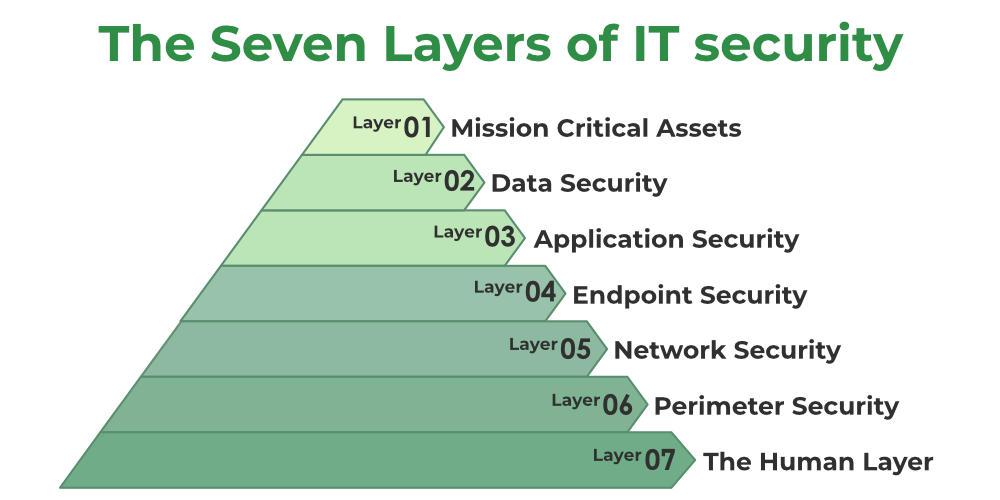
The Human Layer
Humans are the weakest link in any cyber security strategy, and they are alone responsible for 90% of data breaches. Mission-critical assets are protected from a variety of human threats, such as cybercriminals, malevolent insiders, and careless users, by human security controls including phishing simulations and access management rules.
Security Strategy: Education and training, which include instructions on how to recognize and deal with phishing attacks, strong password strategies, system hardening, and cyber security awareness, are the best ways to keep the human layer secure. Access controls are a smart notion for protecting the human layer since they can reduce the amount of harm that could result from a successful attack.
Perimeter Security
The physical and digital security techniques that safeguard the entire company are included in perimeter security controls. Here, we must first define our perimeter before determining the sort of data being transmitted across this layer, and then we must secure both the data and the device.
Security Strategy: This includes firewalls, data encryption, antivirus software, device management (which is crucial if your company has a bring-your-own-device and setting up a secure demilitarized zone for further security.
Network Security
Network security measures to safeguard a company’s network and guard against unwanted access. The key worry of the network layer is what users and devices can access once they are within your system.
Security Strategy: If no one person has access to everything, then any successful cyberattack only results in a small portion of the network being breached. The best practice for security at this layer is to only give employees and devices access to the parts of the network that are 100% necessary for them to do their jobs.
Endpoint Security
Endpoint security measures safeguard the network connection between devices.
Security Strategy: Endpoint encryption is required to make sure that the devices are operating in secure environments.
Application Security
Controls for application security guard against access to an application, access to your mission-critical assets by an application, and internal application security.
Security Strategy: The most basic thing you can do here is to keep your programs up to date. This guarantees that the application is as secure as possible and that any known security vulnerabilities are addressed.
Data Security
Data security measures protect the storage and movement of data, which is the target of cybercrime. The most care must be taken with this layer because it is the foundation of your company.
Security Strategy: At this level, keeping things secure entails file and disc encryption, frequent backups of all crucial data and procedures, two-factor authentication, enterprise rights management, and rules that make sure data is erased from devices that are no longer in use or that are being given to another employee.
Mission Critical Assets
This is the information you must safeguard.
Feeling lost in OS, DBMS, CN, SQL, and DSA chaos? Our Complete Interview Preparation Course is the ultimate guide to conquer placements. Trusted by over 100,000+ lazyroar, this course is your roadmap to interview triumph.
Ready to dive in? Explore our Free Demo Content and join our Complete Interview Preparation course.




