Prerequisite: What is scanning attacks?
Cyber-Attackers use various different methods to carry out the execution of Cyber-Attacks on the computer network, depending on the ease through which the computer network can be attacked on its vulnerability. Each type of Cyber-Attack is risky and harmful in nature. Awareness about cyber crimes is very important for today’s young generation to prevent cyber crimes from taking place and feel safe while using the internet / cyber technology.
Here, we will discuss one such very harmful Cyber-Attack Port Scanning Attack.
Port Scan attack:
- A Port Scan attack is a dangerous type of Cyber-Attack revolving around targeting open ports that are vulnerable to attack.
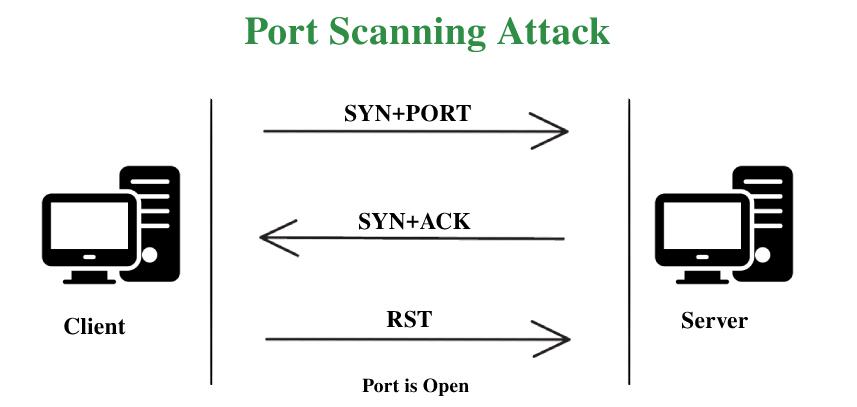
- A Port scan attack helps attackers to identify open points to enter into a cyber network and attack the user.
- Ports are really significant as they help in tracking the traffic that enters and leaves a computer network.
Packets and data that are transmitted over ports tell Cyber-Attackers if the specific port can be vulnerable to attack. - Port scanning attack helps identify of security mechanisms of the network, including active firewalls and anti-viruses.
- In this attack, Cyber-Attackers look for open ports in the network, which they then aim to capture to send and receive information.
- The detected open port is used by Cyber-Attackers to exploit computer system vulnerabilities.
- The identification of open ports gives Cyber-Attackers direct access to the target.
- Since the application listens to these ports, Cyber-Attackers take advantage of this for getting access/ manipulating/deleting confidential user information.
- Nmap, Netcat, and IP Scanning tools are used to scan ports for vulnerability checks.
Aim and Consequences:
- Port scan attack is being used by attackers based on the services and security of the cyber network.
- If proper security mechanisms including authentication methods are not properly implemented, then they become a target attack point for Cyber-Attackers.
- Cybercriminals make use of the vulnerable target security breaches and open port information to get into the user/ organization systems.
Prevention:
The preventive ways for Port Scan attack are listed as follows :
- Secured Firewalls:
- A firewall can be used to track the traffic of open ports, including both incoming and outgoing traffic from the network.
- Identification of an open port is that the target post involved here is bound to respond with packets, which shows that the target host listens on the port.
- Strong Security Mechanisms:
- Computer systems with strong security can protect open ports from being exploited.
- Security administrators should be well aware that any harmful attack should not be allowed access to computer open ports.




