Parameter tampering is a form of web-based cyber attack where specific URL parameters are changed without the user’s knowledge. In some cases, data entered by a user into a form field on a webpage may be modified without the user’s permission. The browser may be directed to a link, page, or site that the user did not intend to visit.
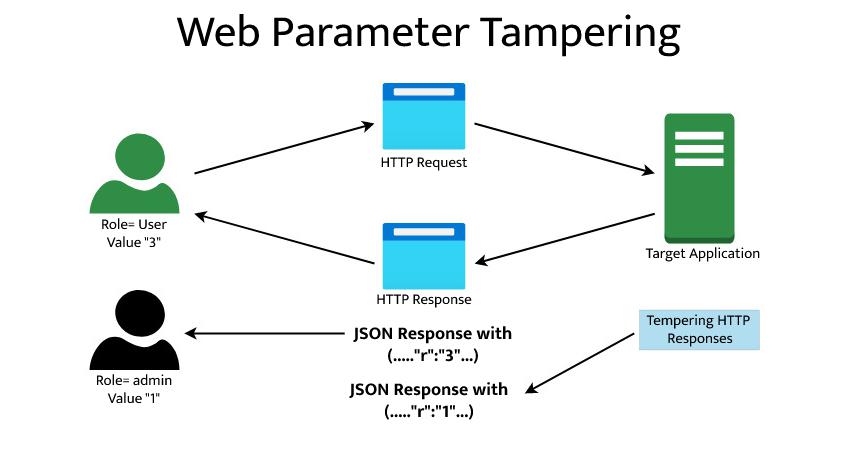
The Web Parameter Tampering attack is based on manipulating parameters exchanged between client and server in order to alter application data, such as user credentials and permissions, product price and quantity, and so on. This data is typically stored in cookies, concealed form fields, or URL Query Strings and is used to enhance application functionality and control.
This attack can be carried out by a malicious user looking to exploit the application for personal gain, or by an attacker looking to attack a third party using a Man-in-the-middle attack. Webscarab and Paros proxy are commonly used in both cases.
Impacts:
The effect of parameter tampering is determined by the type of parameter manipulated.
- The effect of modifying URL query strings: In web applications, query strings are generally used to pass data from the client to the server via parameters, add data calls to a hyperlink, and display that information on the linked page. Attackers may tamper with the URL query string in order to perform malicious actions such as data theft. They can access data from a database, recognize the architecture of a web application, and even execute commands on the web server by manipulating query strings.
- The effect of tampering with HTTP POST data: Many web applications use the POST method to pass data between pages because query strings are relatively simple. Because browsers do not display POST data, it is regarded as a secure method of retrieving information. Attackers can, however, still modify the data to gain access to private data.
- The Effects of Website Cookie Manipulation: A cookie is a small piece of information that is stored in the web browser. Cookies are created by the web server to store user preferences and other data, such as timestamps and session tokens. To gain access to a user’s account and view, manipulate, or exfiltrate sensitive data, an attacker can modify or poison a cookie.
- The effect of tampering with HTTP headers: HTTP requests and responses frequently use headers to convey messages about the HTTP message. The HTTP request header contains a referrer header. It includes the URL of the webpage from which the request was made and allows websites to determine the location of visitors. This information can be used to optimize caching, as well as for analytics and logging. Attackers can change the referrer header to make it appear to be from the original site. They can construct arbitrary HTTP responses and launch a variety of attacks by submitting a malicious string, such as cross-user defacement or web and browser cache poisoning.
Examples of Parameter Tampering:
- Web Parameter Tampering: Form field parameter modification is a common example of a Web Parameter Tampering attack. Consider a user on an application page who can select form field values (combo box, check box, etc.). When a user submits these values, an attacker may obtain and arbitrarily manipulate them.
- Tampering Hidden Fields: When a website stores status information in hidden fields, a malicious user can change the referred data by tampering with the values stored on their browser. For example, an e-commerce shopping site might use hidden fields to refer to its products, as shown below:
<input type=”hidden” id=”1008” name=”cost” value=”70.00”>
In this case, an attacker can change the “value” information of a specific item to reduce its cost.
Prevention:
When applications are developed without properly validating the characters that will be accepted by the web application, parameter tampering is especially common. Fortunately, such attacks can be avoided by using secure programming techniques to ensure that only expected data is accepted by the web application. Malicious actors will be unable to extract information from a database or execute arbitrary commands at the operating system level if the application cannot accept manipulated parameters.
- Using a whitelist format for both client-side and server-side inputs – Whitelisting is a standard process that allows requests or inputs only if they match the pre-defined and administratively approved criteria.
- A firewall – This is an excellent way to control both incoming and outgoing traffic and thus reduce security risks. Using a feature-rich cloud WAF adds a layer of protection because it can handle APIs or microservices from any ecosystem.
- Encryption – Using it for user session cookies is a simple way to limit the likelihood of tampering.
- No Explicit Passing – As mentioned above, any client-side cookie shouldn’t be a part of any key security choices. Parameters that aren’t a part of query strings are less prone to parameter tampering.
- Never store sensitive information in hidden parameters – Critical data, such as product prices and order numbers, should never be stored in hidden parameters or cookies because doing so poses a significant security risk and increases the likelihood of a parameter tampering attack.
- Extensive application testing – In addition to the best practices listed above, application testing is an important line of defense against parameter tampering. Developers and quality assurance testers must test the application from both the standpoint of a user and an attacker to determine if there are any flaws that must be addressed.
- Control Passing parameters – Parameters must be passed to a dynamic webpage in some applications. However, if a specific parameter is left out, the application should display an error message to the user. Furthermore, developers should not assume that a parameter is being passed before using it in the application.
The process of manipulation with URL parameters in order to retrieve information that would in other ways be unavailable to the user is known as parameter tampering. The risks of exploitation vary depending on the parameter being modified and how it is published to the web application server. Parameter manipulation attacks can be used to accomplish a variety of goals, including file disclosure above the web root, information extraction from a database, and execution of arbitrary operating-system level commands. Adopting secure programming strategies to ensure that only expected data is recognized by an application is one of the recommendations.




