Active Sniffing Attacks in Ethical Hacking can lead to using the intercepted data for malicious purposes. The most common use of sniffing is to steal passwords, credit card numbers, and other sensitive data. Sniffers are software programs that let you intercept network traffic in a convert way without the knowledge of the user or administrator. Web application sniffers such as Wireshark can be used to detect this type of attack in its infancy, so organizations can prevent losses from what could be a large impact on their bottom line.
Types of Sniffing Attacks:
- ARP Poisoning Attacks: ARP poisoning is used to redirect network traffic and is usually done to intercept sensitive information from the network. An attacker gains access to the data by sending false ARP messages across the LAN. The attacker will capture ARP request packets and replies for various IP addresses on a LAN. The attacker then sends these ARP reply packets with a spoofed IP address to the victim’s computer and its place in their cache. The victim’s computer now believes that the false addresses are real and authentic, hence it will send all its traffic intended for those IP addresses to the attacker’s computer rather than sending it to its actual destination. The traffic is sent in plain text because we are sniffing it before encryption or decryption.
- Man-in-the-Middle Attacks: In this attack, the attacker uses a sniffer to capture traffic and redirect them to a computer under his control before they reach its original destination.
- Switch Spoofing Attack: Switches are used to distribute packets across a network. A switch is programmed with an ARP table containing the MAC address and IP address of each machine connected to it. The switch learns MAC addresses by sending out a flood of ARP messages every second until each machine responds with its MAC address. The attacker can use his laptop or PC with a sniffer installed on it to act as an intermediary between the source and the destination host. He then captures the packets on his own computer and alters them. He changes the MAC address of the packets and sends them through his switch to their original destination. Once they arrive at the destination, another router that has never seen these new MAC addresses will switch them onto its own network.
- DNS Poisoning: DNS poisoning is a malicious activity that can be used to interfere with a target system’s DNS configuration. The attacker will often use a web browser as part of their attack, by visiting a website hosting an exploit kit, loading a malicious application from an email message or file attachment, or even simply visiting an infected site or opening infected text documents (such as Microsoft Word).
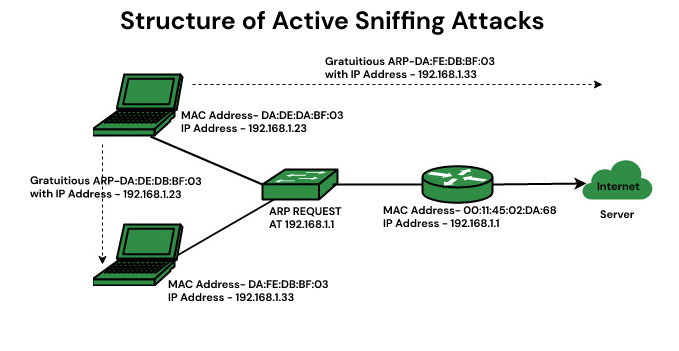
Scenario:
Most organizations are unwilling to implement any of the solutions like secure passwords or firewalls as it will add a large amount of cost and management overheads to the already under-funded IT department. This type of attack is so common that some believe attackers are actively working against these solutions by releasing compromised versions of web-based applications, but they do not stop there.
- Some sniffers actively defeat basic security mechanisms such as placing sniffers on networks in administrative areas and then redirecting users to phishing websites where they give up their saved credentials, thus spoofing login attempts and exacting a high toll on this type of attack.
- Sniffers are also used by many companies to uncover computer viruses and other attacks on their IT networks. Hackers and security analysts harvest packets in order to perform as much forensics as possible. They look for discrepancies in packets, attempt to match passwords in plaintext, or examine the data for what it might reveal about a person or organization.
- Other types of sniffers exist. These include protocol analyzers, which may be passive or active, or even intrusive. Intrusive analyzers are typically called network analyzers when software is used, though they may be physical devices (as with the AirPcap adapter).
Consequences:
- There is a range of consequences that may arise when sniffing an attack is in use. There are privacy concerns and security risks that come with the use of this attack. Prior to delving into them, it is necessary to understand what sniffing entails.
- Sniffing requires someone to use malicious tools called packet analyzers to capture data in transit across a network connection.
- They are then able to read and analyze the information without being detected, as they have not unlawfully accessed any system or account. This can lead to some sensitive details about personal connections being exposed for viewing on another device, as well as their passwords or other sensitive information.
- Its use has been described as a method of accessing the whole range of internet sites and services that rely on communication, such as email and social networks. This can be done through an unwitting victim’s connection. The potential for sniffing to cause harm is a logical consequence since information can be obtained about items that are entrusted from one party to another.
- Protection via the law enforcement and government agencies: Law enforcement has tools for capturing information in transit, which are used on a regular basis to investigate crimes and investigate illegal activities carried out by networks or individuals running the network.
Key Points:
- An attacker may be able to use the phone’s microphone to listen to a conversation.
- Interception may cause a significant loss of privacy. For example, criminals have used interception in a variety of ways.
- In telecommunications, wiretapping, or wiretaps, are techniques involving the use of specialized electronic equipment such as an antenna and receiver to intercept private communications by tapping into local telephone networks.
- Wiretapping is illegal in most jurisdictions in relation to private communications, including (with some exceptions) all forms of electronic communication such as email and Internet telephony, unless specifically permitted by law.
Countermeasures:
- Protect your communication from prying eyes. Trade secrets or copyrighted material should not be transmitted over the Internet. Encrypt all communications. Ensure physical security of the equipment.
- Install an intrusion detection system and firewall to prevent unauthorized access across the network boundary.
Mobile Phones can be used to intercept communications using software that enables monitoring of a GSM phone’s traffic and location without the user’s knowledge by exploiting security flaws in Signaling System 7 used by GSM networks, such as IMSI-catcher. - The GSM network itself is not incapacitated, as the victim’s phone continues to function.
- The stated purpose of this technology was to protect public safety officials from kidnapping victims in crime zones and missing persons, at a cost of around US$100 each for one device.
Conclusion:
Active sniffing attacks in Ethical Hacking are mostly used by attackers to gather information about the target organization but are not always for malicious purposes.




