Bandwidth attacks in ethical hacking target a network’s bandwidth, and by extension, its available computing resources. A hacker can overload a network by sending a high number of packets to the computer or server at once. The processing power and memory in the system is limited and once it reaches capacity, the computer will be rendered useless until all the extra data is removed from its memory. These attacks can be manually executed with software such as NetFlows, or automatically through botnets that are controlled by hackers with malicious intent.
Volumetric attack:
The first type of bandwidth attack is called volumetric attack. This method has been used for many decades and continues to be an effective tool for cyber criminals across the globe today. Volumetric Attack is the act of sending a large amount of data to an online system, while taking advantage of the fact that networks have a finite amount of space and resources.
The term “volumetric attack” arises from the idea that packets sent across the network may be large. The goal behind this type of attack is to use available resources for the purpose of obtaining unauthorized access to a computer system or server. By means of stealing existing credentials, or creating new ones in an effort to bypass security measures, and by using open ports in order to reach into a system through its various defenses, an attacker can send huge amounts of data across a network.
Volumetric attacks are also known as stream attacks. The term arises from the fact that many types of network traffic are voluminous and require bandwidth to be transported across the internet. If a computer is hit with a volumetric attack, it will not only come under a great deal of strain, but its resources will become exhausted fast.
Bandwidth flood attack:
The second type of bandwidth attack is called a “bandwidth flood attack” more commonly called fragmentation. The goal behind this type of attack is typically to saturate an organization’s network with numerous requests competing for space in its memory. Bandwidth attacks in ethical hacking are real threats to company information. The source of the attack can be traced almost immediately when bandwidth is significantly reduced, making it one of the most easily intercepted and therefore less likely to occur. In addition, there are relatively few opportunities for a hacker to take advantage of a business’s network if its available bandwidth is not filled.
Types of Bandwidth Attacks:
- DDoS
- PDoS
- APDoS
These attacks can be perpetrated by a single individual just as easily as an entire team of professional hackers. While their intent may be to test your security and see what you’re made of, they are much more common among malicious actors who want to take down your website or cause damage to your company.
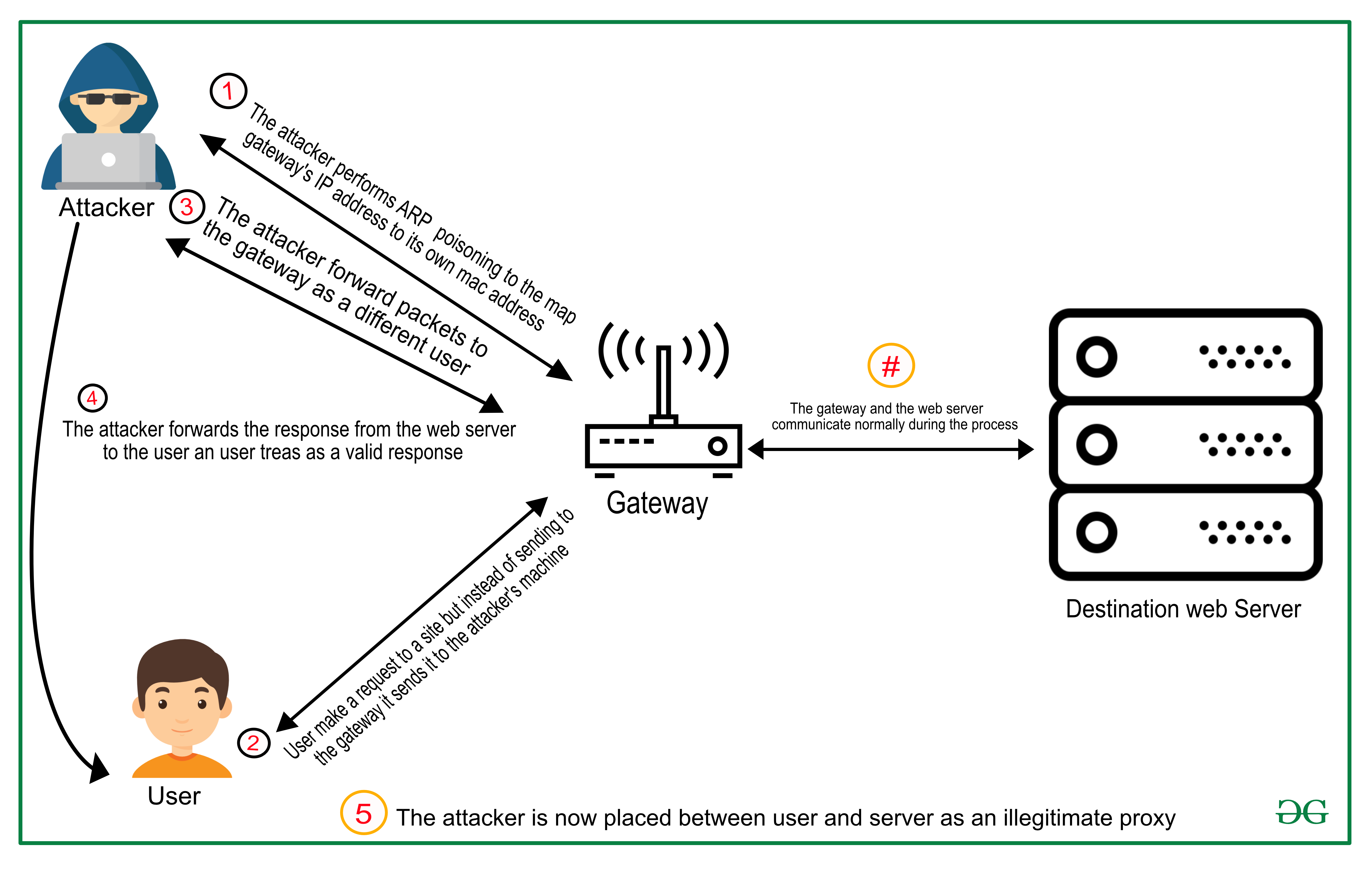
- Man-in-the-middle: This is the most common form of cyber-espionage attack and usually takes place when there is network connectivity between two systems where one system has not been properly secured. The attacker intercepts all traffic between the two systems and changes the communication or takes control over data in transit.
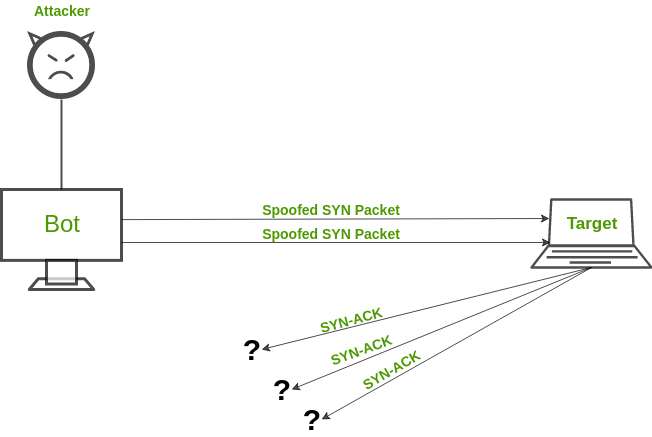
- Denial-of-service attacks: Denial-of-service attacks (DoS) have been around for some time, but what separates them from other types of malware is their potential impact on spectators, as well as their ability to affect multiple systems with a single packet.
A DoS attack against one computer could easily take down an entire network if the user has not properly configured his firewall settings.
Key Points:
- The bigger the attack, the many packets, the slower you can send them.
- If you have a big attack packet, send it with a big block size.
- This means if you are trying to flood someone’s space with junk or DoS messages, try combining your packets into one giant wave of data, and don’t bother limiting the size of each packet because you want enough space to put all your junk in.
- The second type of bandwidth attack is called an “anti-fraud attack” and is defined as a form of malicious activity that takes place after accessing a network while using false credentials and attempting to exploit available networks using this fraudulent identity.
Countermeasures:
- There are a few strategies a network administrator can take to prevent bandwidth attacks in ethical hacking.
- One simple method is to monitor network traffic and audit user access attempts for suspicious behavior, such as attempting to connect to networks that are not part of the employee’s normal work duties.
- Another strategy is to use authentication technology like two-factor authentication in order to ensure that access from unknown sources is blocked before it has the opportunity to exploit systems. Another important strategy is database security.
- A hacker could gain indefinitely into the system if he can place unauthorized programs and commands inside the database that are executed by any user. An access restriction should be installed across the database with strict rules about who can write, delete or even execute data against it.
Conclusion:
Rising threats such as bandwidth attacks in ethical hacking continue to be on the rise, and all emphasis should be placed on defending against them. The FBI recommends all organizations concerned with their data should subscribe to a free, two-way Deep Packet Inspection (DPI) service. DPI systems monitor traffic and examine every packet of information that flows through it. It is significant to ensure that the security of your business network is protected, otherwise, vulnerabilities will cause great damage to your organization’s future success. Experts strongly recommend that companies implement security measures for their network infrastructure, such as software firewalls and intrusion detection services. Security experts also recommend that companies keep up-to-date with emerging technologies by installing updates for products like antivirus software.




