Packet capturing is the process of recording all communication between a computer and other devices. The packets are then analyzed to determine what was said, how it was said when it was said, and where it came from. Packet capture can be used in many ways. One common use is for network forensics. Network forensics involves collecting data from a network device or system to analyze what happened during an incident or investigation. The captured packets are then stored as a file on your hard drive or sent to an email address.
Capturing Packets:
To begin capturing, click on the “Start” button in the top left corner of Wireshark and select “Capture Packets” from the drop-down menu. After you are done capturing packets sent or received in particular communication, you can find the packets list through any of the following methods:
- Through the saved capture option and followed by Ctrl+F or,
- Select Edit Menu in the Menu bar and then select Find Packets sub-menu.
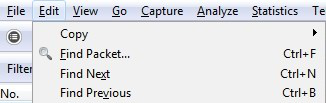
Hereafter you will find an interface having a list of all captured packets of the recent communication. However, we have one more method that can help you locate a particular packet if you know the packet’s numbering, i.e., serial no of the packet. This step is given below:
- Select the Go menu in the menu bar and then after entering the packet number click the Go to packet option. This will directly take you to the desired packet. You can see in the image below the toolbar has all the necessary menus we are discussing.
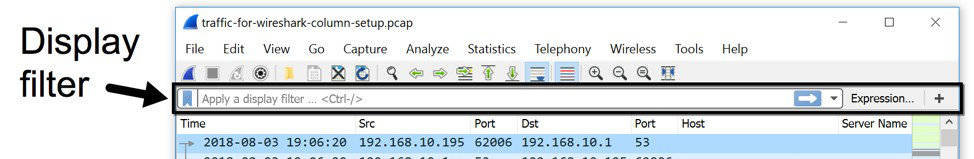
Besides these, once you have your packet list interface with a filter bar above the list as shown in the image above you can search for a particular type of packet i.e., it can be a specific protocol packet such as HTTP, TCP, DNS, etc. or it can belong to a particular port. You have numerous filter options, and we shall explore them one by one. You will realize that through the Analysis menu in the menu bar where you can see the syntax of various searching methods by clicking on the display filter option which shows you different filter syntax. We just need to enter our particular credentials as per the filter order and apply them, and we are good to go.
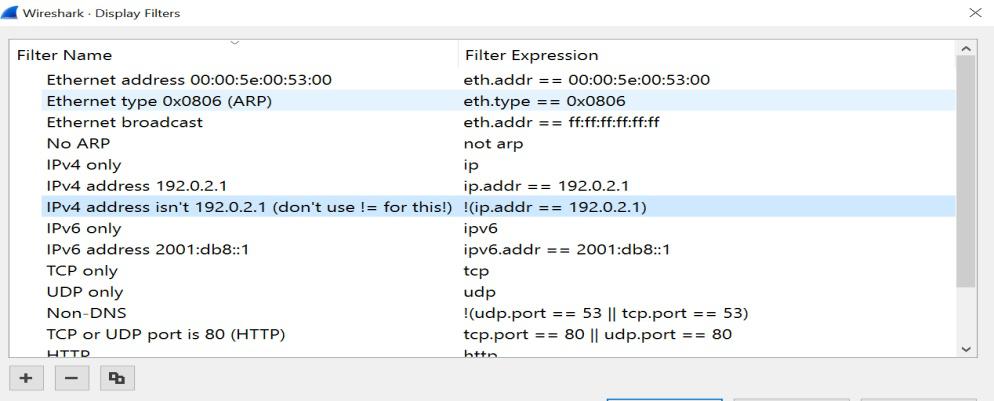
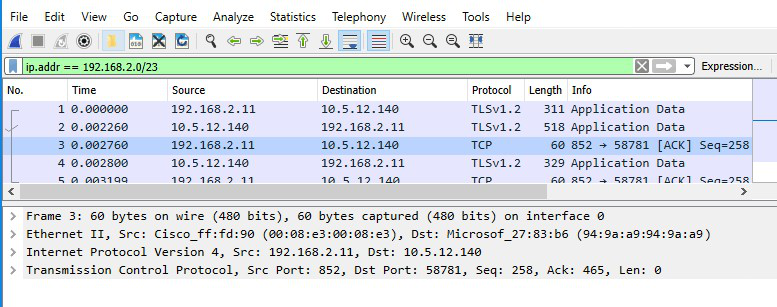
Further, you can search your specific packet through IP address or Ethernet address, or Ethernet types. Some applied filters and the resultant interfaces have been displayed below. You can also select a particular packet whose source and destination match your desired packet and then right-click on it → “apply as filter “→” and selected”. This will directly list all the types of packets having a similar combination of source and destination. You can also add extra filter options by including them after putting “&&” after a pre-entered filter entry.
For, e.g., : ip.addr==”your IP” && dns
This entry will list all packets with similar IP and protocol type DNS, thus helping you minimize your search space. Let’s see below our next filter where we want to access all packets with a particular IP address entered the filter bar and the resultant interface containing packets with matching IP addresses.
Conclusion:
There are numerous ways of sorting and searching a particular packet of a particular type from a pool of packets. These options really help Network protocol analyzers in saving their time and making them execute tasks with ease. Amongst these, the analysis sub-menu has all the necessary syntax after looking at which even a novice can apply complex filters and get the desired captured packets. As we conclude, we should note that all the features of Wireshark, and even the ones we haven’t are easy to learn and beginner-friendly and are one of the biggest reasons for making it the most widely used tool for network protocol analysis today.




