Phlashing is a type of Denial of Service (DoS) Attack, also known as a Permanent Denial of Service Attack (PDoS) which is very severe because there is no way to undo this attack’s consequences as it damages/corrupts the system to such an extreme level that there is no other way except to replace or reinstall the Hardware and this may also result in permanent data loss. It was first demonstrated by HP’s Head of System Security when they noticed a flaw/vulnerability, that ultimately lead to the crashing of the system.
- Phlashing is a term used in ethical hacking. It is also known as “social engineering.” It is a type of hacking that uses the phone book to gain access to the network of a targeted system or network administrator. Phlashing has become a popular method for hackers to gain access to networks, as it is easy and takes less time than other methods.
- Phlashing allows you to gain access to a network by sending malicious code or requests from another device connected to the same network. You can also gain access by installing malware on another device connected to the network and sending malicious code from that device. Phlashes can be done wirelessly via Bluetooth, Near Field Communication (NFC), Wi-Fi, or USB connectivity.
- A wireless phlash can connect directly with the target device without requiring direct interaction with the user’s input devices like keyboards and mice.
- A remote phlash connects with a user’s device over their internet connection and sends malicious code through their web browser or email application.
- The third type of phlashing connects with systems and networks that are connected via Terminal Server applications such as Remote Desktop Connection (RDC). This type of phlashing uses Terminal Server application tools like those found in Microsoft Windows operating systems for connecting with multiple remote systems at once.
- Remote Desktop Connection enables multiple users at one location, such as at an employer’s office, to connect with one computer system at another location, such as at an employee’s desk.
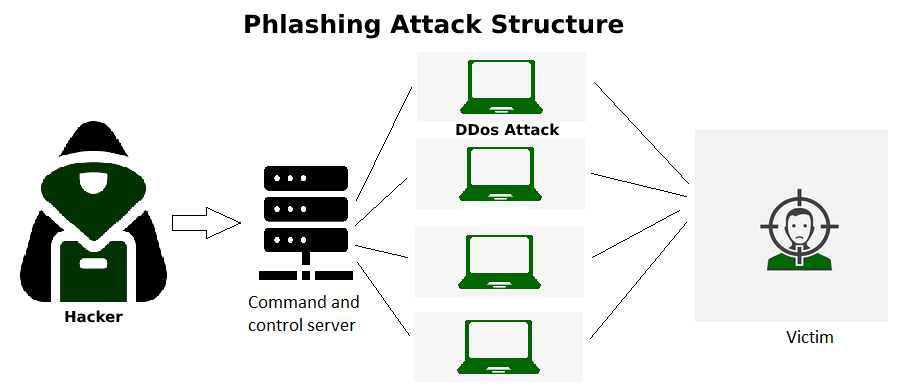
Working:
Basically, it exploits the vulnerabilities/weakness in the organization’s network operations and then by attempting to flood the server/computer with many requests also known as Ping Flooding Attack, that it can’t handle, gets overloaded and hence denies access to actual users or even crashing of computer/server or website getting down. When you want to hack a computer, there are many steps that you need to follow. First, you will have to install the hacking software on your computer. Then, you will need to connect your laptop with the target machine using some kind of cable or wireless connection. After this step is done, the next thing that needs to be done is to download and install a rootkit on your target system so that it can hide from antivirus programs installed in it. The last step before gaining access to any network is phlashing which means making modifications in the firmware so that new features and functions can be added to the device’s
For more information: Denial of Service Attack
BrickerBot:
BrickerBot is a tool that can be used to automate the process of hacking into websites. It allows you to perform actions on a website and then retrieve the results. The main purpose of BrickerBot is to help ethical hackers understand how websites work, by allowing them to test their knowledge through practical exercises. BrickerBot uses Python as its scripting language and has been written in such a way that it can be easily extended for different purposes. The script is divided into two parts: an agent (the part which performs the action) and the server.
Countermeasures to Phlashing:
- Ensure the security of the network to prevent unauthorized login.
- All the firmware and hardware are regularly updated.
- Vulnerabilities and Bugs are immediately resolved at high priority.
- Enabling Firewall and antivirus software to prevent unauthorized outgoing traffic.
- Monitoring and identifying unusual activity.
- Proper actions are taken on intrusion.
- Limiting the rate of requests.
- Only a selected number of people have access to the organization’s firmware.




