The article will go through how to install Firewalk, an overview of its components, how to run a Firewalk scan, and how to understand the scan findings. This post is intended for people who are new to Firewalk and wish to learn how to use it for network security evaluations.
What is the Firewalk tool?
Firewalk is an active network security tool used to determine the accessibility of specific network services and firewall rules. It sends TCP or UDP packets to a target host and then analyzes the responses received. The tool can identify potential security weaknesses in a network, such as open ports and misconfigured firewalls, which can then be secured to prevent unauthorized access.
To fully understand how Firewalk operates, it’s important to understand the following components:
- Packet Generation: Firewalk generates packets sent to the target host to determine which ports are open. The packets contain the source IP address, destination IP address, and source port number.
- Response Analysis: Firewalk analyzes the responses from the target host to determine the accessibility of specific network services and firewall rules. The responses can be used to identify open ports and determine the type of firewall in use.
- Traceroute: Firewalk uses a traceroute to map the path between the source and target host. Traceroute is used to determine the number of hops between the source and target host and the IP address of each hop.
- Port Scanning: Firewalk performs port scanning to determine the status of specific ports on the target host. This can help identify potential security weaknesses, such as open ports that attackers can exploit.
Operation of Firewalk
The operation of Firewalk can be broken down into the following steps:
- Firewalk generates packets and sends them to the target host.
- Firewalk analyzes the responses received from the target host to determine the accessibility of specific network services and firewall rules.
- Firewalk uses a traceroute to map the path between the source and target host.
- Firewalk performs port scanning to determine the status of specific ports on the target host.
- Firewalk displays the scan results, including the target host, open ports, and the type of firewall used.
How to Install Firewalk?
Before you can start using Firewalk on Kali Linux, a few requirements must be met. These include:
- Operating System: Firewalk is compatible with Kali Linux, a Debian-based operating system. It is recommended to have the latest version of Kali Linux installed on your system to ensure compatibility with Firewalk.
- Software: Firewalk is a command-line tool, so it’s important to understand the terminal and how to run commands in it. You will also need to install the necessary dependencies for Firewalk, such as libpcap and libnet. These can be installed using the following command:
sudo apt-get install libpcap-dev libnet-dev
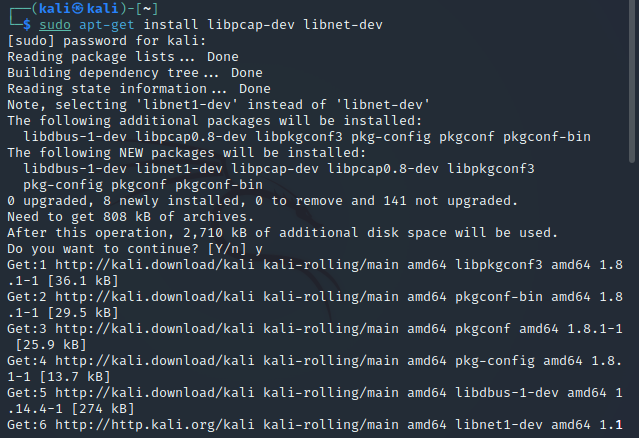
sudo apt-get install libpcap-dev libnet-dev
- Networking Tools: Firewalk requires a basic understanding of networking concepts and tools. Some tools you might need include ping, traceroute, and tcpdump.
- Hardware: To use Firewalk, you will need a computer with a network interface card (NIC) that supports packet capturing. This is necessary to capture network packets and analyze the responses received during a Firewalk scan.
Now, Installing Firewalk on Kali Linux is a straightforward process that can be completed in a few simple steps. Here’s how to do it:
Open the terminal and update the package list using the following command:
sudo apt update
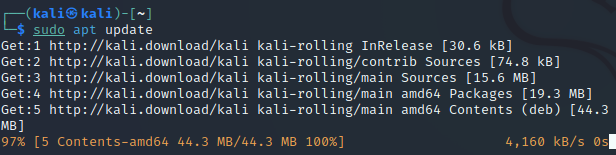
sudo apt update
Install Firewalk using the apt-get command:
sudo apt install firewalk
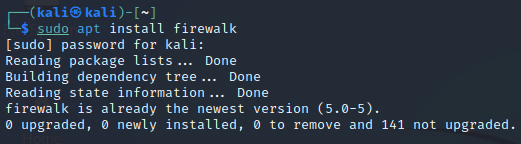
sudo apt install firewalk
Once the installation is complete, you can verify the installation by running the following command:
firewalk
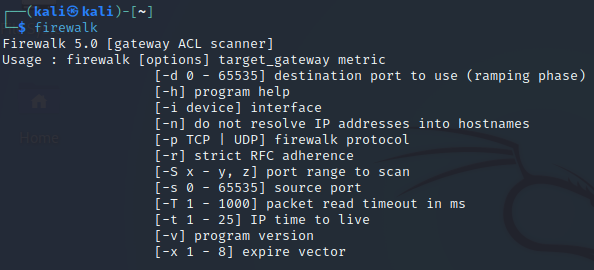
firewalk
This should display the version number of Firewalk that is installed on your system. Now we are ready to use Firewalk in our Kali Linux.
Performing a Firewalk Scan
Performing a Firewalk scan involves specifying the target host, the ports to scan, and any additional options or parameters you want to include. Here’s an example of how to perform a Firewalk scan using the following code:
sudo firewalk -S 1-8081 -i eth0 -n -p TCP 192.168.29.1 172.24.166.183
Let’s break down each part of the code:
- ‘-S 1-8081’: This specifies the range of ports to scan on the target host. In this example, Firewalk will scan ports from 1 to 8081.
- ‘-i eth0’: This specifies the network interface to use for the scan. In this example, the Ethernet interface eth0 will be used.
- ‘-n’: This tells Firewalk not to perform a reverse DNS lookup on the IP addresses of the target host.
- ‘-p TCP’: This specifies the protocol to use for the scan. The Transmission Control Protocol (TCP) will be used in this example.
- ‘192.168.29.1 172.24.166.183’: These are the IP addresses of the target host. In this example, Firewalk will scan the target host at IP address 192.168.1.1 for open ports on the specified range.
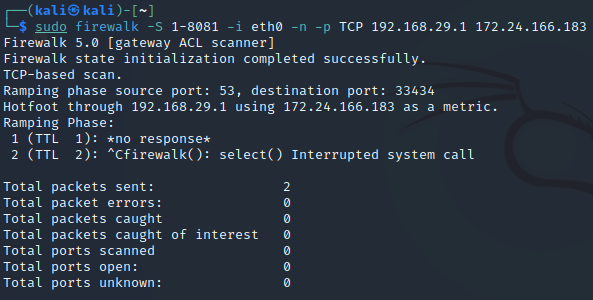
scanned results
Once you have specified the target host and the ports to scan, you can run the Firewalk scan using the code above. Firewalk will then generate packets, analyze responses, perform traceroute, and scan ports to determine the status of specific ports on the target host. The scan results will be displayed in the terminal, providing information about the target host, open ports, and the type of firewall in use.
Conclusion
In conclusion, Firewalk is a vital tool for network security professionals, and its usage is essential for maintaining a secure network environment. By taking the time to understand Firewalk and how it works, you can gain valuable insights into the security of your network and identify potential vulnerabilities that need to be addressed.




