Cluckabunga, the all-in-one system customization app for kfd exploit-vulnerable devices running iOS & iPadOS 16.0-16.6 beta 1 and the successor to the Cowabunga app of similar nature for the MacDirtyCow exploit for older iterations of iOS & iPadOS, received an update Monday morning that may have gone unnoticed amid all the noise regarding Apple’s iOS & iPadOS 17 software updates.
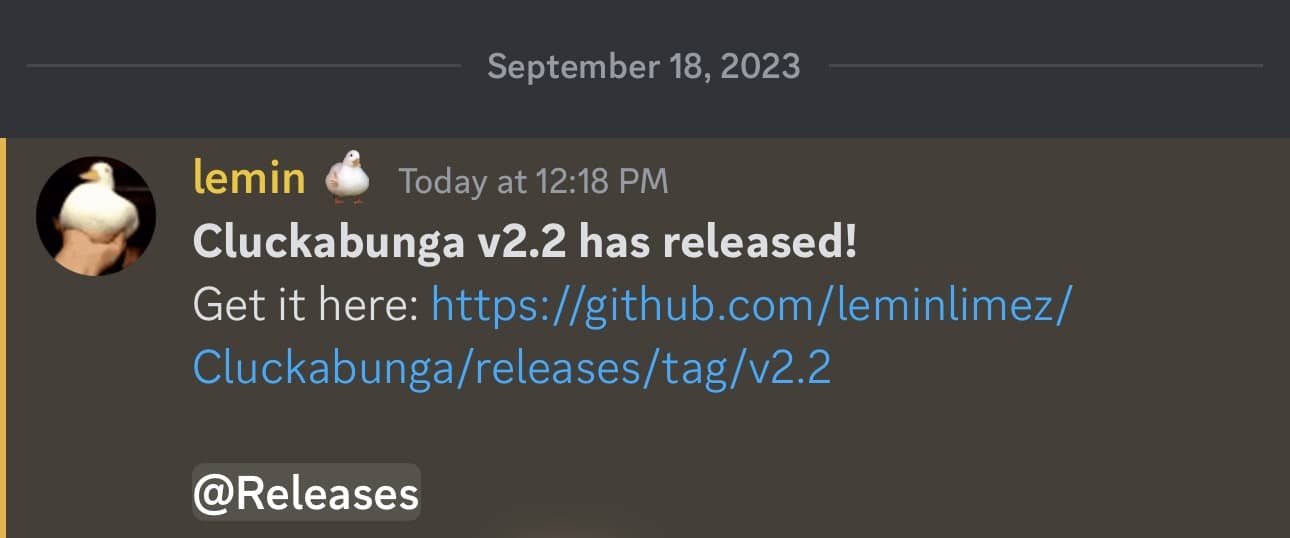
The announcement, shown below was made in the Cowabunga Discord server Monday afternoon by project lead developer leminlimez, and it shared a link to the GitHub website where users could acquire the .ipa file to sideload the latest version of the Cluckabunga app on supported handsets.
The latest version of Cluckabunga, dubbed version 2.2, appears to add the following changes to the app:
– Add support for a Status Bar changer
– Add the ability to reset the passcode keys from within the app
As it would seem, today’s update adds new features that allow a user to customize their Status Bar, but more than that, anyone who has already customized their Lock Screen’s passcode keys, or who plans do so, can now use the reset feature in the app to reset their changes and revert back to their default appearance – a handy feature.
If you’re an existing Cluckabunga app user, then you can merely download and sideload the latest version over your existing installation to upgrade and have the latest features at your disposal. Anyone who isn’t already using Cluckabunga, and who would like to give it a try on their kfd exploit-vulnerable device, can acquire the latest version from the project’s GitHub page.
Are you using the latest version of Cluckabunga yet? Let us know why or why not in the comments section down below.




