If you use an Android phone, you use a Google account. Unless you use a ‘deGoogled’ tablet or smartphone, or install a custom ROM without Google’s services. A Google account is the gateway to accessing apps on the Play Store, along with Google’s other services, such as Drive, Maps, and Photos. Since these services store sensitive data, it’s vital to protect your account from hackers.
The internet is a dangerous place, and compromised accounts aren’t rare. Still, there are steps you can take to ensure your account remains safe. I’ve followed these steps for over a decade, and they’re effective. They’re also simple, so anyone can follow them to safeguard their data.
6
Use a strong password coupled with a password manager
Change your passwords frequently, too
A strong password is the first step to ensure your account is difficult to hack. If hackers employ a brute force attack to gain access to your account, a long and complex password takes effort to crack. So, use a password with several different characters. For instance, use a mix of uppercase and lowercase letters, numbers, and symbols. Don’t use easily guessable details, such as your name, date of birth, or pet’s name.
Along with a complex password, use a unique one for all your accounts. This way, you won’t compromise all your accounts if one account is hacked. If it’s difficult to set and remember a long, unique password for each of your accounts, use a password manager. Don’t use Google’s password manager to store your Google account password, as you can’t access it if your account is compromised.
5
Enable two-factor authentication
An additional layer is always helpful
A long password isn’t sufficient to keep potential attackers at bay. Adding an extra layer of security creates friction when someone is trying to force their way into your account. Two-factor authentication (2FA) is one such deterrent. Enabling 2FA for your Google account requires an extra step to authenticate new login attempts. There are several types of 2FA on Google.
You can opt for a one-time password to be sent to your phone number, a time-sensitive code from an authenticator app of your choice, or a hardware key that is inserted into the device. Google also lets you approve or deny a sign-in attempt on an Android phone, if you have one. You can activate this via your Google account’s Security page. You can pick the most convenient method based on your preference.
If you have a lot of sensitive data or run a YouTube channel, pick up a physical 2FA key for added security.
4
Remove unknown connected devices
Delete phones you don’t use anymore
Google maintains a log of the devices you sign in to with your Google account. You can use this log to identify devices you no longer use and sign out of your account on those. This is a handy feature if you frequently switch devices or use computers in public spaces, such as libraries or hotels. If you sell an old phone or computer to someone, you can prevent them from accessing your Google account using this method.
Head to the Security section of your Google account and navigate to the Your Devices section. Review the list of devices and spot the ones you don’t use. If you see an older device or one you don’t recognize, select it and choose Sign out. Repeat this process every few weeks or months to ensure there aren’t devices on the list that don’t belong to you.
3
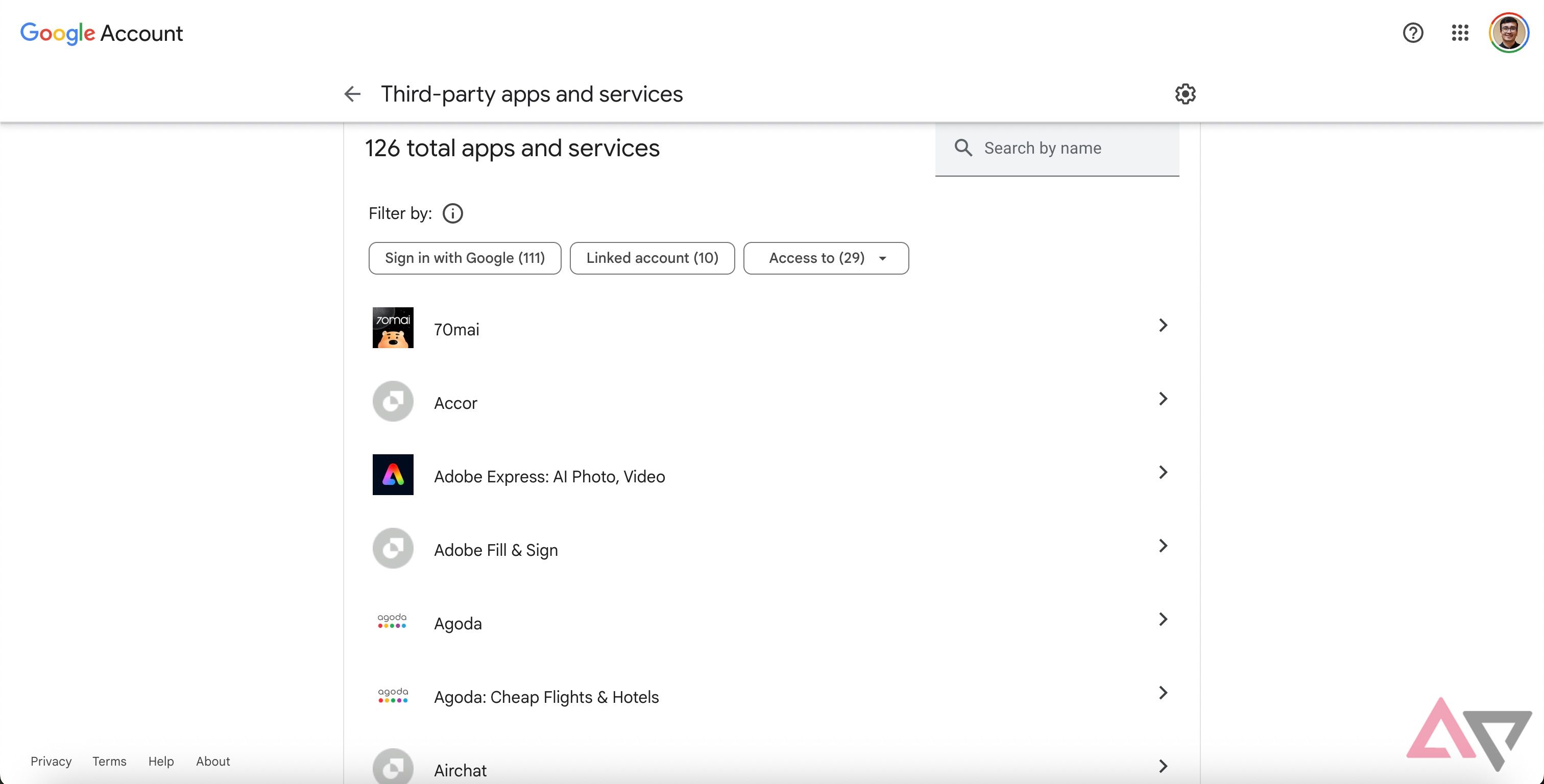
Revoke permissions for unused third-party apps
Sign out of unimportant services
Similar to deleting devices you don’t recognize, Google lets you revoke access to apps or services you linked to your Google account in the past. Some of the apps you used earlier may be defunct or may have turned into malware. It’s also possible that an app’s security may be compromised, which could lead to your account’s credentials being hacked.
Either way, revoke access to apps you no longer use actively. To do this, go to the Security section of your Google account and select Your connections to third-party apps and services. Review the list to find apps you no longer use. Select them, and then click Delete all connections.
2
Use a VPN when accessing public networks
Prevent network attacks
If you have a remote job, you may work from cafés or airports. As a result, it’s common to use free public Wi-Fi networks. This can be dangerous, as other users on the network could hack your computer and gain access to your Google account. To avoid such possibilities, use a VPN when you access an open network.
A VPN encrypts your data and creates a secure tunnel for internet traffic. This makes your information unreadable to hackers who might intercept your data. It also prevents snooping and masks your IP address, preventing attackers from tracking your location. The next time you access a public Wi-Fi network, fire up a VPN before logging in to your accounts.
1
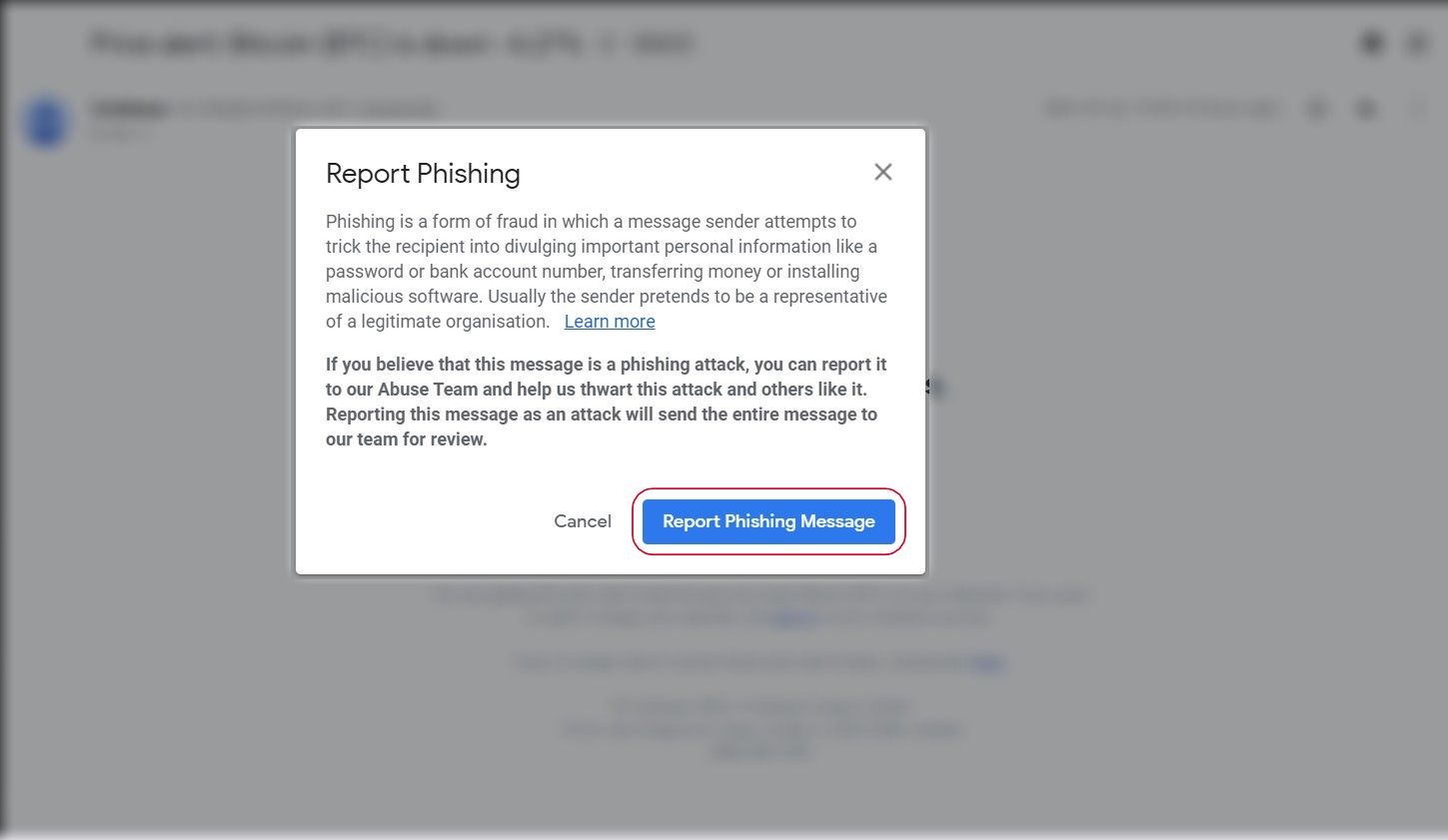
Don’t click links from unknown senders
Don’t fall prey to phishing
Apart from keeping your accounts safe, be aware of your actions on the internet. Doing things like visiting unknown websites or clicking links sent to you by unknown senders can compromise your Google account. If you receive a link to log in to your Google account claiming that it’s Google or another business, verify the domain from which the email was sent. If it’s an unknown domain, refrain from clicking the link. While you’re at it, report the sender so that Google flags the email ID for phishing.
When you sign in to your Google account, visit the official website using the address bar in your browser and then enter your credentials. This way, you can ensure you’re not visiting a URL that could be used for phishing. When using a smartphone, I use the corresponding app, if available, instead of visiting the service’s website in a browser.
Protect your account and data.
Several users rely on Google’s services to store their data. Whether it’s photos, videos, emails, or work files, safeguarding them from attackers is extremely important, as your data may contain files you don’t want the public to access. Move important files to your local storage or a network attached storage (NAS) device. If you use cloud storage for convenience, follow the mentioned steps to keep your account safe from potential attacks.