A system that uses two-factor authentication (2FA) requires two methods of verifying your identity before it accepts a login. The most frequent use of 2FA is for logins that require an email/password combination and a code sent via SMS or email. Once you enter the code alongside your email/password combination, the system lets you in. It’s simple, but devastatingly effective, as hackers can’t access a 2FA-protected account even if they have the relevant email and password. So, in the case of a data breach of passwords, an account protected by 2FA would still be safe.
However, like any security system, 2FA has vulnerabilities. Whether via phishing, malware, or code interception, hackers can still gain access to an account protected by 2FA. We’ll show you the most common ways hackers bypass 2FA and what you can do to protect your online accounts.
5
Phishing attacks can intercept 2FA requests
Always be on the lookout for dodgy URLs or email addresses
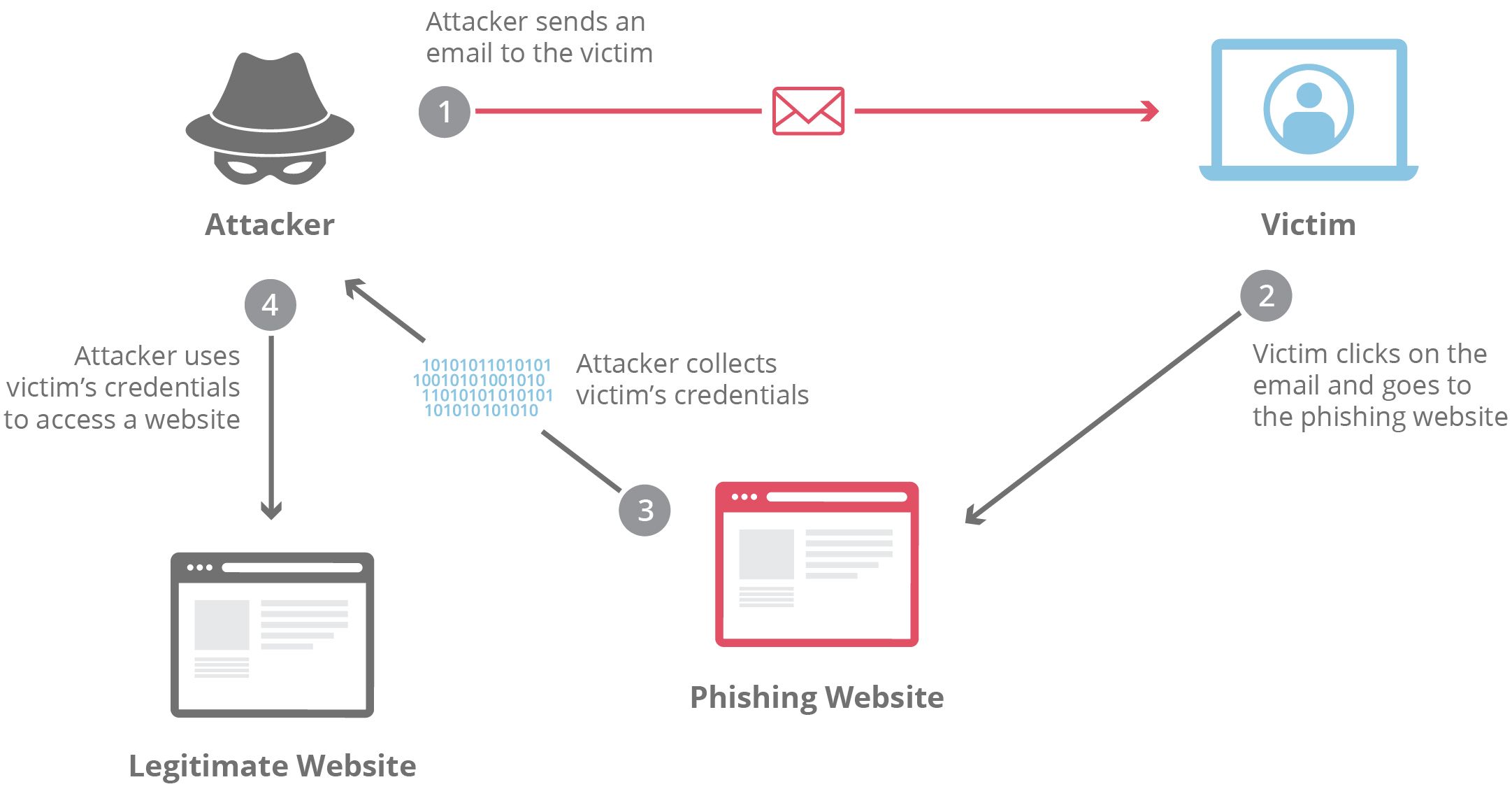
Phishing is one of the most common ways hackers gain access to accounts, as all the hacker needs to do is trick us into believing a fraudulent email address or website is legitimate. While some messaging apps, email services, and browsers can try to detect suspicious links and email addresses, they’re not perfect. Even accounts protected by 2FA can be accessed through phishing links.
If you click on a phishing link that takes you to a login page and enter your email and password, the fraudulent site records these details. The fraudulent site then enters the details into the real site behind the scenes, which will send you an authentication prompt. You then enter your legitimate authentication code into the fraudulent website, which then records it and uses it to access the legitimate website. From here, the hackers can access your details and try to reset your passwords.
A second layer of 2FA protects some websites, so you need to authenticate any attempt to change your password or details. Unfortunately, many don’t, so the hacker can reset your passwords to lock you out, rendering your 2FA method useless.
What to do:
Make sure you’re aware of common signs of phishing attacks, and be vigilant even if your account is protected by 2FA. If you can, set up a second layer of 2FA for changing your password or other personal details.
4
OAuth consent phishing can bypass 2FA entirely
Check what apps you’re allowing access to
Many websites and apps allow you to use another account to log in via a system called OAuth. If you’ve ever used your Google, Apple, or Facebook account to log in to another website, that’s thanks to OAuth. Logging in using this method reduces the number of accounts and passwords you have to juggle, but it opens the door to new security issues. The first is that if malicious actors gain access to the parent account, they have unrestricted access to any linked third-party accounts. The second is that ne’er-do-wells could impersonate this process to bypass 2FA.
OAuth consent phishing starts with a regular phishing attack. Once you click on the phishing link, the fraudulent website or application will ask you to log in with another account. You will then receive a legitimate notification from the respective provider, asking you to confirm the permissions requested by the application.
Once you confirm the permission request, the fraudulent application has access to all the requested data, bypassing 2FA completely.
What to do:
Fraudulent applications used in OAuth consent phishing attacks have a few tell-tale signs. On top of the regular signs of a phishing attack, like grammatical errors and spoof email addresses, fraudulent OAuth consent phishing requests will ask for far more details than a legitimate application would need. If you spot a suspicious number of data requests, don’t accept the OAuth message.
3
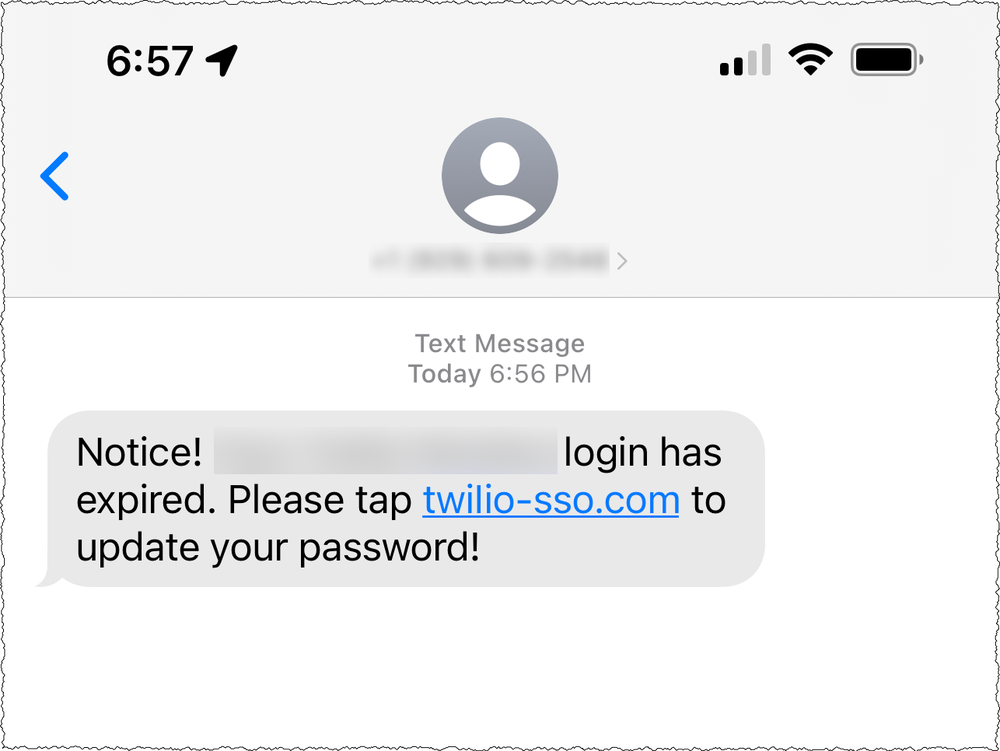
Interception of authentication messages over SMS
SMS is the least secure 2FA method
A short message service center (SMSC) acts as the middleman for SMS communication. When you send a SMS message, it’s first sent to an SMSC, which then forwards it to the recipient. This system ensures that text messages reach their destination even if the recipient is temporarily unable to receive messages. In these scenarios, the SMSC holds the message until the recipient is available again. However, the SMSC is vulnerable to malicious attacks.
SMS messages are unencrypted, which means that anyone with access to the SMSC can read all its stored messages. Not only could a malicious actor read messages containing 2FA codes, but they could also modify them. For example, they could replace the verification code with a phishing link. As you are already expecting an SMS message, you’re more likely to click it than if it were sent out of the blue.
What to do:
SMS is the least secure method of 2FA, so you should always use an authentication app when possible. However, SMS verification is still better than nothing, so keep using it if there’s no other option. But always be on the lookout for suspicious messages, and never click a link in a text message sent from an unknown number.
2
Push-bombing can trick you into accepting a 2FA request
Never accept notifications you weren’t expecting
Some applications use push notifications as a 2FA method. You’ll often see these when you’re asked to approve a login to an app or website from a different device. If a hacker gains access to your email/password combination, they can try to send you an authentication request and hope that you approve it.
Push-bombing can take the form of repeated push notifications asking you to approve access. This method seems ineffective, but it has been used to great effect as victims try to stop the flood of push notifications.
What to do:
Never interact with push notifications you weren’t expecting, or from a flood of identical notifications. Snooze the notifications and wait for it to end. Be careful logging into your account, as the legitimate 2FA request can become lost in a sea of fraudulent requests.
1
Session cookie theft can happen without you knowing
Don’t stay logged into websites that store sensitive information
When you log in to any website, it generates a session cookie, which allows you to stay logged in. If you return to a website and you don’t need to log in again, this is thanks to the session cookie storing your login details. Some websites will log you out after a period of inactivity, but most don’t.
If a hacker steals this session cookie, they can log in to your account, completely bypassing 2FA. This method is especially dangerous, as there are no indicators when a hacker steals a session cookie.
What to do:
Session cookies are invalidated when you log out. Always manually log out of websites that store valuable information to invalidate the cookie.
Stay aware of 2FA’s vulnerabilities
Despite its vulnerabilities, two-factor authentication is still the best way to secure your accounts. However, you must be aware of the ways hackers can bypass 2FA to make it worthwhile. Stay aware of common phishing techniques, and use a 2FA app like Google Authenticator or Authy instead of SMS verification.