Eric Goldstein
Updated on: December 2, 2024
Fact-checked by Kate Davidson
Malware infection rates are only increasing in 2024, so it’s essential to protect our devices. But, what if your security software is doing more harm than good?
Rogue security software has more than doubled in the last decade. These malicious apps are designed to mimic antivirus programs but are actually a sinister malware scam. Once downloaded, they cause endless frustration and even trick users into making payments.
As cybercriminals innovate, it’s increasingly hard to tell legitimate anti-malware from money-grabbing scams. Learning the difference is crucial to avoid becoming the next victim of rogue security software.
Features of Rogue Security Software
Countless rogue antivirus programs exist, but most include similar features. Certain elements mimic other malware types, such as scareware and rootkits, which indicates that the software isn’t legitimate.
Defining characteristics of rogue security software include:
Mimics Anti-Malware
Most anti-malware performs scans, alerts you of threats, and allows you to resolve these issues. Rogue anti-malware mimics this, except that instead of addressing the problem it demands a payment.
Constant Alerts
Rogue security software encourages the user to act by flooding their desktop with endless messages about supposed threats. In reality, the only malware you have is most likely the app itself.
Requires Extra Payments
Once the software has overwhelmed you with reports of infections, it prompts you to take action. However, instead of instantly deleting the files, it asks for a payment. Handing over the money might stop the alerts temporarily, but the cycle will just start again until another payment is required.
Modifies Actual Security Software
Like most rootkit infections, rogue security software can modify your antivirus. Cybercriminals don’t want you to know that their program is a fraud, so they put a chokehold on other apps that might alert you.
Freezes Entire Computer
This software may freeze your computer. It will either create so many pop-ups that the system is overwhelmed, or crash your desktop entirely until a payment is made.
It can take a while for users to realize they’re victims of rogue security software. Knowing how to distinguish rogue programs from the real thing is essential to staying safe.
How to Spot Rogue Software
You may come into contact with rogue security software in different ways. These signs will help you spot if you’ve fallen victim to a rogue app.
Software You Didn’t Download
If you suddenly start receiving notifications from an app that you didn’t intentionally download, that’s a cause for concern. The best thing you can do in this case is to run a full scan of your computer with a genuine antivirus like Norton.
Changes to Your Browser Homepage
Rogue downloads often make unpermitted changes. Most of these go unnoticed, but some are more obvious. Changes to your browser homepage and auto-search settings are a sign of an infection.
Increase in Pop-ups
Desktop pop-ups are no longer a regular feature of operating systems. If you suddenly see endless alerts and warnings, that’s a definite red flag.
Spelling Mistakes and Typos
Check for typing mistakes before downloading, since errors in app descriptions suggest a scam.
Bad Reviews
Apps with bad reviews that mention the typical features of rogue security should be avoided entirely.
Unfortunately, some of these telltale signs only occur after you’ve contracted the infection. Avoiding malicious downloads altogether is the best defense against rogue antivirus.
Avoid Downloading Rogue Security Software
Rogue antivirus software can be downloaded actively or passively, so it requires more vigilance than other malware. Develop these habits to avoid it.
- Always read antivirus reviews carefully. Look at the negative responses first, as some companies hire people to write positive reviews. If there are any reports that the download is malware, look elsewhere.
- Use well-known security brands with years of industry experience. Internationally trusted companies, such as Norton and
Bitdefender , won’t offer rogue software. - Hackers are known to copy branding from reliable sources, so never download from unofficial vendors. Always visit the official site of a brand when buying or installing its products.
- Smart clicking should already be an everyday security practice, but it’s even more critical for security software. Standard rules apply; don’t open email attachments from unknown senders, click on ads or pop-ups, or use shortened URLs.
- Regularly updating your software will reduce the chances of hackers installing the app via a security hole. These vulnerabilities are identified by software companies and patched when they provide updates.
- Most rogue apps use urgency to prompt users into clicking. They might claim you have a severe infection, say you’ve won a prize, or ask for an immediate update to your accounts. Ignore these scare tactics to reduce the risk of being tricked into a malicious download.
- Find a well-reviewed, high-quality security suite that can help identify rogue software before it’s installed. The top choices will halt installations if they note any threats.
If You Get Infected
Despite using the best cybersecurity procedures, you can still end up with an infection. Malware is continually developing, and hackers are finding new ways to gain access to your computer. If you spot the signs of rogue software, take these steps to remove the infection.
- Start your computer in Safe Mode.
- Open your premium-quality antivirus software — I’m using Norton in this example.
- Run a full scan of your system.
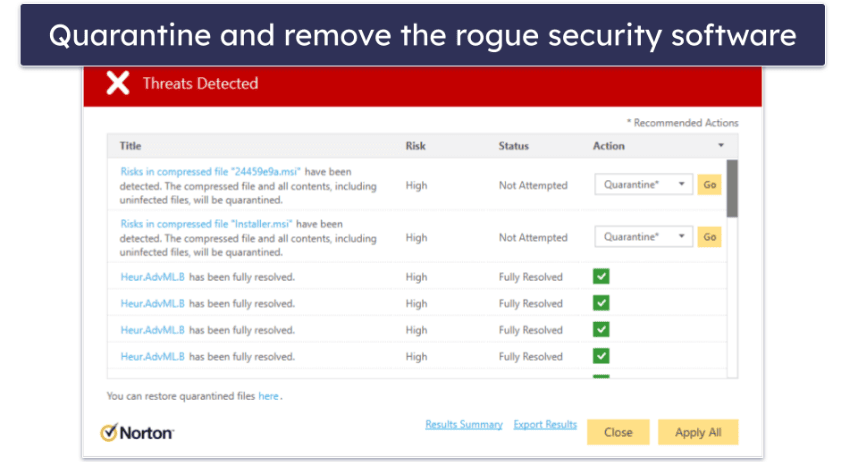
- Once the rogue software is identified, quarantine and delete it.
OR
You could try to delete the infection manually:
- Open your Task Manager/Activity Monitor.
- Search for a list of known rogue antivirus infections.
- Compare the list to the processes running.
- Once you’ve identified it, search for the app name and delete manually.
Protect Yourself from Rogue Security Software Threats
We often trust our security software implicitly, but hackers can exploit this by deploying rogue software, a threat many users aren’t even aware of.
If you’re adequately informed, it’s easy to protect yourself from rogue threats. Follow smart guidelines to reduce the risk of infection, and find a security solution that you can genuinely trust.
Frequently Asked Questions
How does rogue security software infect computers?
Rogue security software typically spreads through phishing emails, compromised websites, or pop-up ads. It can also be bundled with other seemingly legitimate software. Once you’ve clicked or downloaded the malware, it will install itself on your system, often bypassing usual security checks. If you suspect you’ve accidentally downloaded rogue security software, check out our tips on the telltale signs.
How do I protect my computer from rogue security software?
You should always keep your operating system and legitimate antivirus software up-to-date — this will help to block known threats. Remember to only download software from reputable sources (look at reviews if you’re not sure), and avoid clicking on pop-ups or links in unsolicited emails. You can also use web browser settings and extensions that block pop-ups and unsafe sites.
What should I do if I accidentally install rogue security software?
If you suspect that rogue security software has been installed, you should disconnect from the internet to prevent any data transmission to cybercriminals. Then, use a trusted and legitimate antivirus like Norton to scan and remove the rogue software. You should also change important passwords and monitor your accounts for any unusual activity as an extra precaution.