Most people are familiar with Windows systems joined to a domain controller and using Active Directory for authentication. However, in this guide, this is not the case. It is possible to use the FreeIPA Realm with a few adjustments to act as an authentication on Windows systems.
What is Active Directory?
Active Directory is a special-purpose database with services that allow users to connect to network resources tied to it. This database stores important information about your environment such as the user and computers permitted to make connections. Active Directory being a Microsoft product, it is often used within a Windows environment.
What is FreeIPA?
FreeIPA is a free and open-source integrated security information management solution sponsored by RedHat. It combines the MIT Kerberos, Dogtag (Certificate System), NTP, DNS, and 389 Directory Server. The main aim is to provide similar functionality to the Active Directory. It can be used to provide centralized authentication, authorization, and account information. It achieves these functionalities by storing user, group, host, and any other data required to manage the security of networked computers. What makes this tool niftier is its simple and easy-to-use web interface as well as a command line for administration.
FreeIPA is not a re-implementation of Microsoft Active Directory and can work independently. The main difference between the two is that; FreeIPA is focused on Linux and other standards-compliant systems while Active Directory is a Windows tool.
FreeIPA can be integrated to work with Active Directory by establishing trust between the two services. But in this guide, we will configure Windows System to use the FreeIPA Realm for user authentication without Active Directory.
To achieve this, follow the below steps to the latter.
Setup Requirements
In this guide, I will have two systems with static IP addresses and hostnames configured:
| TASK | HOSTNAME | IP_ADDRESS |
| FreeIPA server(Rhel-based) | freeipa.geeksforgeeks.org | 192.168.205.2 |
| Windows client | win-server.geeksforgeeks.org | 192.168.205.152 |
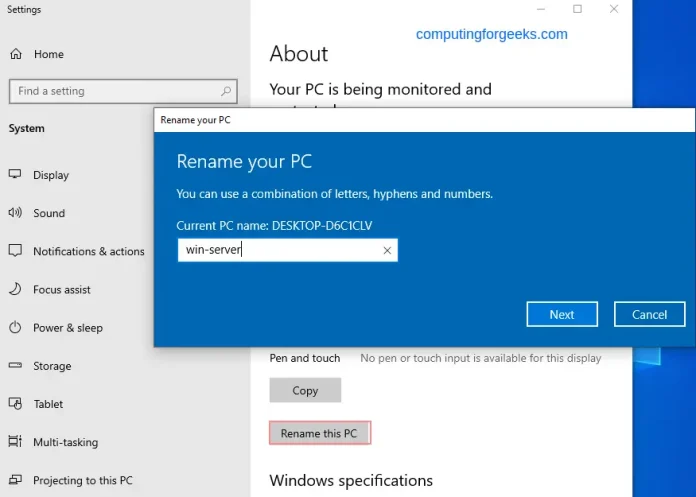
Set the hostname on Windows as shown:

The Linux the hostname can be set as as shown:
sudo hostnamectl set-hostname freeipa.neveropen.techAdd this to /etc/hosts:
$ sudo vim /etc/hosts
192.168.205.2 freeipa.neveropen.techSwitch to the root user:
sudo su -Step 1 – Configure Chrony NTP synchronization
NTP time synchronization is important between the server and client for timestamps of tickets generated by Kerberos(FreeIPA). On Linux, configure the NTP time using the Chrony tool:
yum -y install chronyStart and enable the service:
systemctl enable --now chronydConfigure NTP:
timedatectl set-timezone Africa/Nairobi --adjust-system-clock
timedatectl set-ntp yesConfirm the set time:
$ timedatectl
Local time: Thu 2022-07-14 13:16:11 EAT
Universal time: Thu 2022-07-14 11:16:11 UTC
RTC time: Thu 2022-07-14 11:16:11
Time zone: Africa/Nairobi (EAT, +0300)
System clock synchronized: yes
NTP service: active
RTC in local TZ: noOn the Windows client, configure the TimeZone as shown.

Now you have the time between the two systems synchronized.
Step 2 – Install and Configure FreeIPA Server
We will begin by configuring SELinux. Set it to permissive mode:
sudo setenforce 0
sudo sed -i 's/^SELINUX=.*/SELINUX=permissive/g' /etc/selinux/configEnable and install the required packages using the commands:
sudo yum module enable idm:DL1 -y
sudo yum distro-sync
sudo yum module install idm:DL1/{dns,adtrust}Proceed to the interactive FreeIPA with DNS configuration.
ipa-server-install --setup-dns --allow-zone-overlapProceed with the installation as illustrated below:
==============================================================================
This program will set up the IPA Server.
Version 4.9.8
...........
Server host name [freeipa.geeksforgeeks.org]: Press Enter
....
Please confirm the domain name [geeksforgeeks.org]: Press Enter
Please provide a realm name [COMPUTINGFORGEEKS.COM]: Press Enter
.......
Directory Manager password: Press Enter
Password (confirm):
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password: Enter admin password here
Password (confirm):
Do you want to configure DNS forwarders? [yes]: yes
Following DNS servers are configured in /etc/resolv.conf: 8.8.8.8
Do you want to configure these servers as DNS forwarders? [yes]: yes
All detected DNS servers were added. You can enter additional addresses now:
Enter an IP address for a DNS forwarder, or press Enter to skip: Press Enter
DNS forwarders: 8.8.8.8
Checking DNS forwarders, please wait ...
Do you want to search for missing reverse zones? [yes]: yes
Do you want to create reverse zone for IP 192.168.205.2 [yes]: yes
Please specify the reverse zone name [205.168.192.in-addr.arpa.]:
NetBIOS domain name [COMPUTINGFORGEE]:
Do you want to configure chrony with NTP server or pool address? [no]: no
.....
The IPA Master Server will be configured with:
Hostname: freeipa.geeksforgeeks.org
IP address(es): 192.168.205.2
Domain name: geeksforgeeks.org
Realm name: COMPUTINGFORGEEKS.COM
The CA will be configured with:
Subject DN: CN=Certificate Authority,O=COMPUTINGFORGEEKS.COM
Subject base: O=COMPUTINGFORGEEKS.COM
Chaining: self-signed
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 8.8.8.8
Forward policy: only
Reverse zone(s): 205.168.192.in-addr.arpa.
Continue to configure the system with these values? [no]: yes
When everything is complete, you will see this:

Allow the required services through the firewall:
sudo firewall-cmd --permanent --add-service={ntp,dns,freeipa-4,freeipa-ldap,freeipa-ldaps}
sudo firewall-cmd --reloadNow you can access the FreeIPA web console using the URL https://domain_name

Login using the created admin credentials and access the dashboard below.

Step 3 – Join a Windows client to IPA domain
On the web console, navigate to the hosts tab and click add

Provide the hostname and IP address of the Windows client as shown.

The client has been added but has not yet been enrolled.

Get back to the FreeIPA command line and add the client. First, generate the ticket using the command:
# kinit admin
Password for [email protected]: Get the supported encryption types:
# ipa-getkeytab --permitted-enctypes
Supported encryption types:
AES-256 CTS mode with 96-bit SHA-1 HMAC
AES-256 CTS mode with 192-bit SHA-384 HMAC
Camellia-256 CTS mode with CMAC
AES-128 CTS mode with 96-bit SHA-1 HMAC
AES-128 CTS mode with 128-bit SHA-256 HMAC
Camellia-128 CTS mode with CMACAdd the principal using the command with the below syntax. Remember, you need to enable the encryption types:
# ipa-getkeytab -s freeipa.geeksforgeeks.org -p host/win-server.geeksforgeeks.org@COMPUTINGFORGEEKS.COM -e aes256-cts,aes128-cts,aes256-sha2,aes128-sha2,camellia256-cts-cmac,camellia128-cts-cmac -k /etc/krb5.keytab -P
New Principal Password:
Verify Principal Password:
Keytab successfully retrieved and stored in: /etc/krb5.keytabIn the above command:
- -s specifies the FreeIPA server
- -e specifies the encryptions
- -p specifies the new principal to be added
- -P sets the password(do not forget since it will be used when setting up the client later)
Verify if the key has been added:
# klist -k
Keytab name: FILE:/etc/krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
2 host/[email protected]
2 host/[email protected]
2 host/[email protected]
2 host/[email protected]
2 host/[email protected]
2 host/[email protected]
1 host/[email protected]
1 host/[email protected]Now back on the web interface, the client should be enrolled.

Step 4 – Create FreeIPA Users
To be able to use FreeIPA for authentication on Windows, you need to create a user on IPA. On the FreeIPA, navigate to the Users tab and add a user as shown:

The added user will appear as shown.

Step 5 – Configure the Windows Client
First, we will set the DNS so that it can be able to resolve the name of the IPA server. Navigate the Network settings

Edit the network properties and set the FreeIPA server as the DNS server.

Open the command prompt as the administrator. Confirm that the FreeIPA server resolves.

Run the commands below to configure the system to use FreeIPA:
ksetup /setdomain [REALM NAME]
ksetup /addkdc [REALM NAME] [kdc DNS name]
ksetup /addkpasswd [REALM NAME] [kdc DNS name]
ksetup /setcomputerpassword [MACHINE_PASSWORD] #(the one used above)
ksetup /mapuser * *Replace the values appropriately. For example:

Now launch the gpedit.msc by pressing Windows key + R.

Navigate to Windows Settings > Security Settings > Local Policies > Security Options > Network Security: Configure encryption types allowed for Kerberos

Now enable all the encryptions apart from the first two DES options.

Apply, click OK and restart the system.
Step 6 – Log in to Windows using the FreeIPA users
When the system reboots, login using the FreeIPA user as shown.

You will be asked to change the password for the IPA user

Proceed to sign in.

Verify sign-in as shown.

Closing Thoughts
We have triumphantly walked through how to join Windows System to FreeIPA Realm without Active Directory. I hope this was important to you.
Related posts:
- Install Active Directory Domain Services in Windows Server
- Install and Configure OpenLDAP Server on CentOS 8
- Run Keycloak Server in Docker Containers with Let’s Encrypt SSL