Questions: How to install Vault Server on Ubuntu 18.04 / Debian 9?, How to Install Vault Server on CentOS 7?, How to Install Hashicorp Vault on Fedora?. Hashicorp Vault is a free and open source tool designed for securely storing and accessing secrets. A secret can be a password, API key, certificate, and more. The job of Vault Server is to provide a unified interface to any stored secret while providing tight access control and recording a detailed audit log.
Vault features a web user interface which you can use to interact with Vault. From UI you can easily create, update, read and delete secrets, authenticate, unseal, and more.
Features of Vault
Below are the key features of Vault.
- Secure Secret Storage: By default Vault encrypts the secrets before writing them to persistent storage.
- Support for Dynamic Secrets: Vault can generate secrets on-demand and revoke them after the lease is up.
- Leasing and Renewal: All secrets in Vault have a lease associated with it. The secret is automatically revoked at the end of the lease. Renewal is possible via built-in renew APIs.
- Secrets Revocation: Vault can revoke not only single secrets, but a tree of secrets, for example all secrets read by a specific user, or all secrets of a particular type.
Install Vault on Ubuntu / Debian / CentOS / Fedora
Vault is written in Go and binary packages are available for major Unix and Linux distributions. The precompiled Vault binaries are available at https://releases.hashicorp.com/vault/
VAULT_VERSION="1.3.1"
curl -sO https://releases.hashicorp.com/vault/${VAULT_VERSION}/vault_${VAULT_VERSION}_linux_amd64.zip
Extract downloaded archive.
unzip vault_${VAULT_VERSION}_linux_amd64.zip
sudo mv vault /usr/local/bin/A check on version should match downloaded one.
$ vault --version Vault v1.3.1
Enable command autocompletion.
vault -autocomplete-install complete -C /usr/local/bin/vault vault
Configure Vault systemd service
After installing vault, let’s configure systemd service to manage its service. Start by creating a unique, non-privileged system user to run Vault.
Create Vault data directories.
sudo mkdir /etc/vault sudo mkdir -p /var/lib/vault/data
Then create user named vault.
sudo useradd --system --home /etc/vault --shell /bin/false vault
sudo chown -R vault:vault /etc/vault /var/lib/vault/
Create a Vault service file at /etc/systemd/system/vault.service.
cat <<EOF | sudo tee /etc/systemd/system/vault.service
[Unit]
Description="HashiCorp Vault - A tool for managing secrets"
Documentation=https://www.vaultproject.io/docs/
Requires=network-online.target
After=network-online.target
ConditionFileNotEmpty=/etc/vault/config.hcl
[Service]
User=vault
Group=vault
ProtectSystem=full
ProtectHome=read-only
PrivateTmp=yes
PrivateDevices=yes
SecureBits=keep-caps
AmbientCapabilities=CAP_IPC_LOCK
NoNewPrivileges=yes
ExecStart=/usr/local/bin/vault server -config=/etc/vault/config.hcl
ExecReload=/bin/kill --signal HUP
KillMode=process
KillSignal=SIGINT
Restart=on-failure
RestartSec=5
TimeoutStopSec=30
StartLimitBurst=3
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOFCreate Vault /etc/vault/config.hcl file.
touch /etc/vault/config.hcl
Add basic configuration settings for Vault to /etc/vault/config.hcl file.
cat <<EOF | sudo tee /etc/vault/config.hcl
disable_cache = true
disable_mlock = true
ui = true
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
storage "file" {
path = "/var/lib/vault/data"
}
api_addr = "http://0.0.0.0:8200"
max_lease_ttl = "10h"
default_lease_ttl = "10h"
cluster_name = "vault"
raw_storage_endpoint = true
disable_sealwrap = true
disable_printable_check = true
EOF
You can also use Consul Storage backend, but first you’ll need to install Consul, check:
How to setup Consul Cluster on Ubuntu
Configuration for Consul backend looks similar to below.
storage "consul" {
address = "127.0.0.1:8500"
path = "vault"
}Read more on consul storage configuration
Start and enable vault service to start on system boot.
sudo systemctl daemon-reload
sudo systemctl enable --now vault
Check service status, it should show running.
$ systemctl status vault
● vault.service - "HashiCorp Vault - A tool for managing secrets"
Loaded: loaded (/etc/systemd/system/vault.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2019-03-04 10:17:19 CET; 4s ago
Docs: https://www.vaultproject.io/docs/
Main PID: 12727 (vault)
Tasks: 7 (limit: 2299)
CGroup: /system.slice/vault.service
└─12727 /usr/local/bin/vault server -config=/etc/vault/vault.hcl
Mar 04 10:17:19 vault.local vault[12727]: Api Address: http://0.0.0.0:8200
Mar 04 10:17:19 vault.local vault[12727]: Cgo: disabled
Mar 04 10:17:19 vault.local vault[12727]: Cluster Address: https://0.0.0.0:8201
Mar 04 10:17:19 vault.local vault[12727]: Listener 1: tcp (addr: "0.0.0.0:8200", cluster address: "0.0.0.0:8201", max_request_duration: "
Mar 04 10:17:19 vault.local vault[12727]: Log Level: info
Mar 04 10:17:19 vault.local vault[12727]: Mlock: supported: true, enabled: false
Mar 04 10:17:19 vault.local vault[12727]: Storage: file
Mar 04 10:17:19 vault.local vault[12727]: Version: Vault v1.0.3
Mar 04 10:17:19 vault.local vault[12727]: Version Sha: 85909e3373aa743c34a6a0ab59131f61fd9e8e43
Mar 04 10:17:19 vault.local vault[12727]: ==> Vault server started! Log data will stream in below:
Initialize Vault Server
Export VAULT_ADDR environment variable before you initialize Vault server.
export VAULT_ADDR=http://127.0.0.1:8200
echo "export VAULT_ADDR=http://127.0.0.1:8200" >> ~/.bashrc
Replace 127.0.0.1 with Vault Server IP address.
Start initialization with the default options by running the command below:
sudo rm -rf /var/lib/vault/data/*
vault operator init > /etc/vault/init.file
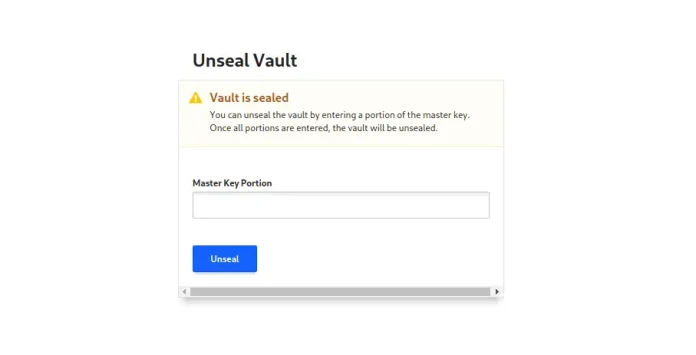
Access Vault UI in http://serverip:8200/ui

Paste your “Unseal Keys” one by one to Unseal vault. You can get the keys on /etc/vault/init.file.
$ cat /etc/vault/init.file
Unseal Key 1: bNxZRU3azPZtzXjeS0pfGHLoif3Scs64fFk9j/FFtUN7
Unseal Key 2: kChe6UJ5+BnkU6UjSzalvjIuh01dLX8v/OMabz+uPtly
Unseal Key 3: MIRYhY1zQXZyod05tWtbgAnc14qBXM7hPHrqyEVQ7tCi
Unseal Key 4: KBVhzztVDUJRqNi2LDYfRFHThQe/iDbNdEaOFkAztMDN
Unseal Key 5: GJplvpcPVu6IQeJ3lqa5xvPfXTDA3ftgcZJT6xhrAUUL
Initial Root Token: s.RcW0LuNIyCoTLWxrDPtUDkCw
Vault initialized with 5 key shares and a key threshold of 3. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 3 of these keys to unseal it
before it can start servicing requests.
Vault does not store the generated master key. Without at least 3 key to
reconstruct the master key, Vault will remain permanently sealed!
It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.
Once you “Unseal” Vault, use Initial Root Token to Sign in to Vault.

You should see Vault web dashboard in the next page.

You can also view Vault status from CLI.
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.0.3
Cluster Name vault
Cluster ID 92ed9909-8088-a797-d5be-768d8c09ce27
HA Enabled false
Test HTTP API endpoint using curl to check initialization status.
$ curl http://127.0.0.1:8200/v1/sys/init
{"initialized":true}
Configure Vault Roles And Policies
Export your Vault root token:
export VAULT_TOKEN="s.RcW0LuNIyCoTLWxrDPtUDkCw"
Replace “s.BOKlKvEAxyn5OS0LvfhzvBur” with your Initial Root Token stored in the /etc/vault/init.file file.
Then enable the approle auth method which allows machines or apps to authenticate with Vault-defined roles
$ vault auth enable approle
Success! Enabled approle auth method at: approle/
Same command can be used for other Authentication methods, e.g
# vault auth enable kubernetes
Success! Enabled kubernetes auth method at: kubernetes/
# vault auth enable userpass
Success! Enabled userpass auth method at: userpass/
# vault auth enable ldap
Success! Enabled ldap auth method at: ldap/
List all Authentication methods using the command:
$ vault auth list
Path Type Accessor Description
---- ---- -------- -----------
approle/ approle auth_approle_a113b1e0 n/a
kubernetes/ kubernetes auth_kubernetes_e324b8e2 n/a
ldap/ ldap auth_ldap_d2f6edde n/a
token/ token auth_token_1aa8b643 token based credentials
userpass/ userpass auth_userpass_6178aae8 n/a
Other Authentication Methods can also be enabled from the Web interface.

ACL Policies can be managed from the Web Console “Policies” section.

Write and get Secrets
Now that we have installed and configured our vault server, let’s write and retrieve secrets in Vault. We use vault kv to write secrets.
Get secret engine path:
$ vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_4cf73c3d per-token private secret storage
identity/ identity identity_248343db identity store
secret/ kv kv_30258a59 key/value secret storage
sys/ system system_cbeaa203 system endpoints used for control, policy and debugging
Write a secret to your kv secret engine.
$ vault kv put secret/databases/db1 username=DBAdmin
Success! Data written to: secret/databases/db1
$ vault kv put secret/databases/db1 password=StrongPassword
Success! Data written to: secret/databases/db1
You can even use single line command to write multiple data.
$ vault kv put secret/databases/db1 username=DBAdmin password=StrongPassword
Success! Data written to: secret/databases/db1
To get a secret, use vault get command.
$ vault kv get secret/databases/db1
====== Data ======
Key Value
--- -----
password StrongPassword
username DBAdmin
Get data in json format:
$ vault kv get -format=json secret/databases/db1
{
"request_id": "f99170b5-ac38-84ce-8668-1f280b0981c1",
"lease_id": "",
"lease_duration": 36000,
"renewable": false,
"data": {
"password": "StrongPassword",
"username": "DBAdmin"
},
"warnings": null
}
To print only the value of a given field, use:
$ vault kv get -field=username secret/databases/db1
DBAdmin
To delete a Secret, use:
$ vault kv delete secret/databases/db1
Success! Data deleted (if it existed) at: secret/databases/db1
$ vault kv get secret/databases/db1
No value found at secret/databases/db1
Learn more on Vault Documentation and Step by Step Learning tutorials.
Related Articles:
How to Install Vagrant and Virtualbox on Fedora
Install Latest Vagrant on Ubuntu / Debian & Kali Linux
How to Install Terraform on Ubuntu / CentOS