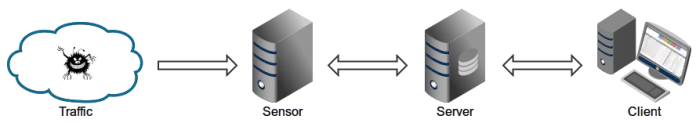Nowadays, due to sophisticated systems, attacks are frequent and intense. It is therefore a huge task for system and network engineers to detect malicious traffic in a network to ensure the security of the network and prevent cyber attacks.
Malicious network traffic refers to any network traffic that is intended to harm a network, system, or user. This can include various types of attacks, such as denial-of-service (DoS) attacks, malware, phishing, and more. The effects of such traffic can vary depending on the type of attack and the target system. The few common effects of malicious network traffic are slowdowns and outages, data theft or destruction, compromised systems, financial losses e.t.c
There are several tools that can be used to detect malicious traffic. These include; Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM), Network Traffic Analysis (NTA) tools, Endpoint Detection and Response (EDR), Vulnerability Scanners, Malware Analysis Tools e.t.c
Today, we will learn how to detect Malicious traffic in your Network using Maltrail.
What is Maltrail?
Maltrail is an open-source network security tool that helps in detecting and block malicious traffic. It is designed to monitor network traffic and detect malicious activities by using various techniques such as traffic anomaly detection, DNS-based blacklists, and YARA rules.
Maltrail can be deployed in various network environments such as small businesses, enterprises, and data centres. It can be used to monitor both inbound and outbound traffic and can be configured to send alerts when suspicious activity is detected.
Maltrail uses a combination of signature-based and behaviour-based techniques to detect threats. It analyzes the network traffic and compares it to a set of predefined rules and patterns to identify malicious activity. It can detect various types of threats such as malware, phishing, and botnet activity.
Maltrail has the Traffic -> Sensor <-> Server <-> Client architecture. The Sensor is a standalone component running on the monitoring node such as a Linux host which monitors the passing traffic for blacklisted items/trails. The server’s main task is to store the event details and provide back-end support for the reporting web application. The server and sensor can both be configured to run on the same machine.
Below is a diagram showing the Maltrail architecture:

The key features of Maltraill are:
- Anomaly detection: Maltrail uses anomaly detection techniques to identify suspicious network traffic patterns that may indicate the presence of malware, botnets, or other types of malicious activity.
- DNS-based blacklists: Maltrail uses DNS-based blacklists to block traffic from known malicious IP addresses and domains.
- YARA rules: Maltrail uses YARA rules to identify and block traffic that matches specific patterns of malicious behaviour.
- Web interface: It also provides a web interface for monitoring network traffic and provides detailed information on detected threat
- Network protocols: Maltrail supports a wide range of network protocols, including TCP, UDP, ICMP, and DNS.
- Customizable alerts: Maltrail allows security teams to customize alerts based on specific criteria, such as severity level, source IP address, or destination IP address.
- Compatibility: Material is compatible with various network environments, including small businesses, enterprises, and data centres.
Setup Pre-requisites
Before we derive into the installation, you need to have the below requirements met:
- Python 2.6, 2.7 or 3.x installed. You also need the pcapy-ng package installed
- At least 1GB of RAM to run in single-process mode or more if run in multiprocessing mode
To install Python and pcapy-ng, use the commands:
##Ubuntu/Debian
sudo apt update
sudo apt install git python3 python3-dev python3-pip python-is-python3 libpcap-dev build-essential procps schedtool
sudo pip3 install pcapy-ng
##Rhel 8/CentOS 8/Rocky Linux 8/Alma Linux 8
sudo yum install epel-release -y
sudo dnf config-manager --set-enabled powertools
sudo yum install gcc gcc-c++ git libpcap-devel python3-devel python3-pip procps schedtool
sudo pip3 install pcapy-ng
## SUSE/openSUSE
sudo zypper install gcc gcc-c++ git libpcap-devel python3-devel python3-pip procps schedtool
sudo pip3 install pcapy-ng
Install and Configure Maltrail
Once the above prerequisites have been met, you are set to install Maltrail. Begin by cloning the GitHub repo as shown:
cd /opt && sudo git clone --depth 1 https://github.com/stamparm/maltrail.gitSte the permissions and navigate into the directory:
sudo chmod -R 775 /opt/maltrail
cd /opt/maltrailOnce in the directory, there is a config file known as maltrail.conf. This contains configurations for the server and sensor. Open this file for editing with the command:
vim maltrail.confThis file has two main blocks. The server block and the sensor block. The server block has the below default config:
# [Server]
# Listen address of (reporting) HTTP server
HTTP_ADDRESS 0.0.0.0
# Listen port of (reporting) HTTP server
HTTP_PORT 8338
# Use SSL/TLS
USE_SSL false
# User entries (username:sha256(password):UID:filter_netmask(s))
# Note(s): sha256(password) can be generated on Linux with: echo -n 'password' | sha256sum | cut -d " " -f 1
# UID >= 1000 have only rights to display results (Note: this moment only functionality implemented at the client side)
# filter_netmask(s) is/are used to filter results
USERS
admin:9ab3cd9d67bf49d01f6a2e33d0bd9bc804ddbe6ce1ff5d219c42624851db5dbc:0: # changeme!
# local:9ab3cd9d67bf49d01f6a2e33d0bd9bc804ddbe6ce1ff5d219c42624851db5dbc:1000:192.168.0.0/16 # changeme!
# Mask custom trail names for non-admin users (UID >= 1000)
ENABLE_MASK_CUSTOM true
# Should server do the trail updates too (to support UPDATE_SERVER directive in [Sensor] parameters)
USE_SERVER_UPDATE_TRAILS false
...
In the above block, we have:
- HTTP_ADDRESS contains the web server’s listening address. 0.0.0.0 allows it to listen to all addresses.
- HTTP_PORT contains the web server’s listening port. The default one is 8338
- USE_SSL is set to true then SSL/TLS will be used for accessing the web server
- USERS contains the user’s configuration settings. Each user entry consists of the username:sha256(password):UID:filter_netmask(s)
- FAIL2BAN_REGEX contains the regular expression
The sensor block has:
# [Sensor]
# Number of processes
PROCESS_COUNT 1
# Disable setting of CPU affinity (with schedtool) on Linux machines (e.g. because of load issues with other processes)
DISABLE_CPU_AFFINITY false
# Use feeds (too) in trail updates
USE_FEED_UPDATES true
# Disable (retrieval from) specified feeds (Note: respective .py files inside /trails/feeds; turris and ciarmy/cinsscore seem to be too "noisy" lately; policeman is old and produces lots of false positives)
DISABLED_FEEDS turris, ciarmy, policeman, myip, alienvault
# Ignore IPs that appear on lower than IP_MINIMUM_FEEDS number of feeds (Note: static IP trails are always included)
IP_MINIMUM_FEEDS 3
# Disable trails based on the following regular expression run against the corresponding info
#DISABLED_TRAILS_INFO_REGEX known attacker|tor exit node
# Update trails after every given period (seconds)
UPDATE_PERIOD 86400
# Location of directory with custom trails (*.txt) files
CUSTOM_TRAILS_DIR ./trails/custom
# (Max.) size of multiprocessing network capture ring buffer (in bytes or percentage of total physical memory) used by sensor (e.g. 512MB)
CAPTURE_BUFFER 10%
# Interface used for monitoring (e.g. eth0, eth1)
MONITOR_INTERFACE any
# Network capture filter (e.g. ip)
# Note(s): more info about filters can be found at: https://danielmiessler.com/study/tcpdump/
#CAPTURE_FILTER ip or ip6
CAPTURE_FILTER udp or icmp or (tcp and (tcp[tcpflags] == tcp-syn or port 80 or port 1080 or port 3128 or port 8000 or port 8080 or port 8118))
# Sensor name to appear in produced logs
SENSOR_NAME $HOSTNAME
....
This block contains:
- USE_MULTIPROCESSING is set to true then all CPU cores will be used
- SENSOR_NAME contains the name that should be appearing inside the events
- MONITOR_INTERFACE should contain the name of the capturing interface
- USE_FEED_UPDATES can be used to turn off the trail updates from feeds altogether (and just use the provided static ones).
- USE_HEURISTICS turns on heuristic mechanisms
- CUSTOM_TRAILS_DIR can be used by the user to provide the location of the directory containing the custom trails (*.txt) files.
- CAPTURE_FILTER should contain the network capture (tcpdump) filter to skip the uninteresting packets and ease the capturing process
- UPDATE_PERIOD contains the number of seconds between each automatic trails update
- SYSLOG_SERVER and/or LOGSTASH_SERVER can be used to send sensor events
If you want to start and test the Sensor and server used the commands:
sudo python3 sensor.py
sudo python3 server.pyTo stop them, execute:
sudo pkill -f sensor.py
sudo pkill -f server.pyCreate Systemd Services for Maltrail
We need to create a system service to automatically start these services on system boot. First, create a service file for the Sensor by copying the available config:
sudo cp maltrail-sensor.service /etc/systemd/system/
sudo cp maltrail-server.service /etc/systemd/system/Reload the system daemon:
sudo systemctl daemon-reloadStart and enable the services:
sudo systemctl enable --now maltrail-sensor
sudo systemctl enable --now maltrail-serverCheck the status of the sensor service:
$ systemctl status maltrail-sensor
● maltrail-sensor.service - Maltrail. Sensor of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/maltrail-sensor.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2023-03-22 06:51:28 EDT; 7s ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 4286 (python3)
Tasks: 1 (limit: 23198)
Memory: 13.9M
CGroup: /system.slice/maltrail-sensor.service
└─4286 /usr/bin/python3 sensor.pyCheck the status of the server service:
$ systemctl status maltrail-server
● maltrail-server.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/maltrail-server.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2023-03-22 06:53:40 EDT; 6s ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 4407 (python3)
Tasks: 1 (limit: 23198)
Memory: 13.0M
CGroup: /system.slice/maltrail-server.service
└─4407 /usr/bin/python3 server.pyAllow the service through the firewall:
##For UFW
sudo ufw allow 8338
##For firewalld
sudo firewall-cmd --add-port=8338/tcp --permanent
sudo firewall-cmd --reloadTo be sure that everything is up, run the command:
ping -c 1 136.161.101.53
cat /var/log/maltrail/$(date +"%Y-%m-%d").logSample Output:

You can also test the capturing of DNS traffic using the commands:
nslookup morphed.ru
cat /var/log/maltrail/$(date +"%Y-%m-%d").logSample Output:

Access the Maltrail Web Portal
You can then access the Web UI using the URL http://IP_Address:8338

On this page, log in using the default creds (admin:changeme!).
- Username: admin
- Password: changeme!
Once authenticated, you will see the below dashboard.

From my dashboard, you can see two threats, these are the threats we tested earlier. Now from my system, I will try to access one of the malicious sites say j0mla.sytes.net. This is the output from the browser:

Back on my Maltrail web UI, I will see the threats increase.

You can view detailed information about your network traffic. For example, view the events:

Verdict
That marks the end of this guide on how to detect Malicious traffic in your Network using Maltrail. We can all agree that Maltrail is a useful tool for detecting and blocking malicious traffic in a network environment. However, like all security tools, it should be used in combination with other security measures to provide a comprehensive security solution.
Related content:
- Scan for Docker Image and Git vulnerabilities using Trivy
- Install Nessus Vulnerability Scanner on Debian
- Scan Docker Container Images for Vulnerabilities with Trivy
- Faraday – Penetration Testing IDE & Vulnerability Management Platform