In this article, we will discuss how to Install Metasploit Framework on Debian 11/10 /9 Linux system. Metasploit Framework is the world’s most popular open source penetration testing framework for security professionals and researchers. It provides the infrastructure, content, and tools to perform extensive security auditing and penetration testing.
The Metasploit Framework runs the following services.
- PostgreSQL Database server – used by Metasploit to store data from a project.
- Ruby on Rails
- Metasploit service
Metasploit Framework Requirements
The minimum hardware requirements for running Metasploit Framework on Debian 11/10 /9 are:
- CPU – 2 GHz+ processor
- RAM – 4 GB RAM available (8 GB recommended)
- Disk Space – 1 GB available disk space (50 GB recommended)
Install Metasploit Framework on Debian 11/10 /9
Installing Metasploit framework on Debian11/10 /9 has been made easy by provision of Metasploit installer script. You just need to download the installer and run it.
Install curl tools:
sudo apt update
sudo apt install curl wget gnupg2Download Metasploit installer using wget or curl command.
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstallOnce the script is downloaded, make it executable.
chmod +x msfinstallThen execute the installer to install Metasploit Framework on Debian11/10 /9
$ ./msfinstallThe installer script will add Metasploit Framework repository to your repository list and install all tools required. If you have slower internet, the download may take a while.
Switching to root user to update the package
Adding metasploit-framework to your repository list..Warning: apt-key is deprecated. Manage keyring files in trusted.gpg.d instead (see apt-key(8)).
OK
Updating package cache..OK
Checking for and installing update..
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following NEW packages will be installed:
metasploit-framework
0 upgraded, 1 newly installed, 0 to remove and 1 not upgraded.
Need to get 258 MB of archives.
After this operation, 626 MB of additional disk space will be used.
Get:1 http://downloads.metasploit.com/data/releases/metasploit-framework/apt lucid/main amd64 metasploit-framework amd64 6.1.14+20211108112548~1rapid7-1 [258 MB]
Fetched 258 MB in 3s (102 MB/s)
perl: warning: Setting locale failed.
perl: warning: Please check that your locale settings:
LANGUAGE = (unset),
LC_ALL = (unset),
LC_CTYPE = "UTF-8",
LC_TERMINAL = "iTerm2",
LANG = "C.UTF-8"
are supported and installed on your system.
perl: warning: Falling back to a fallback locale ("C.UTF-8").
Selecting previously unselected package metasploit-framework.
(Reading database ... 30060 files and directories currently installed.)
Preparing to unpack .../metasploit-framework_6.1.14+20211108112548~1rapid7-1_amd64.deb ...
Unpacking metasploit-framework (6.1.14+20211108112548~1rapid7-1) ...
Setting up metasploit-framework (6.1.14+20211108112548~1rapid7-1) ...
update-alternatives: using /opt/metasploit-framework/bin/msfbinscan to provide /usr/bin/msfbinscan (msfbinscan) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfconsole to provide /usr/bin/msfconsole (msfconsole) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfd to provide /usr/bin/msfd (msfd) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfdb to provide /usr/bin/msfdb (msfdb) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfelfscan to provide /usr/bin/msfelfscan (msfelfscan) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfmachscan to provide /usr/bin/msfmachscan (msfmachscan) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfpescan to provide /usr/bin/msfpescan (msfpescan) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfrop to provide /usr/bin/msfrop (msfrop) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfrpc to provide /usr/bin/msfrpc (msfrpc) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfrpcd to provide /usr/bin/msfrpcd (msfrpcd) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfupdate to provide /usr/bin/msfupdate (msfupdate) in auto mode
update-alternatives: using /opt/metasploit-framework/bin/msfvenom to provide /usr/bin/msfvenom (msfvenom) in auto mode
Run msfconsole to get startedWhen installation is completed, create and initialize the msf database.
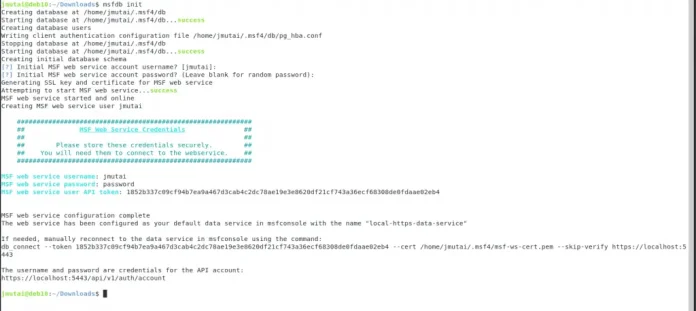
$ msfdb init
Creating database at /home/jmutai/.msf4/db
Starting database at /home/jmutai/.msf4/db...success
Creating database users
Writing client authentication configuration file /home/jmutai/.msf4/db/pg_hba.conf
Stopping database at /home/jmutai/.msf4/db
Starting database at /home/jmutai/.msf4/db...success
Creating initial database schema
[?] Initial MSF web service account username? [jmutai]:
[?] Initial MSF web service account password? (Leave blank for random password):
Generating SSL key and certificate for MSF web service
Attempting to start MSF web service...success
MSF web service started and online
Creating MSF web service user jmutai
############################################################
## MSF Web Service Credentials ##
## ##
## Please store these credentials securely. ##
## You will need them to connect to the webservice. ##
############################################################
MSF web service username: jmutai
MSF web service password: password
MSF web service user API token: 1852b337c09cf94b7ea9a467d3cab4c2dc78ae19e3e8620df21cf743a36ecf68308de0fdaae02eb4
MSF web service configuration complete
The web service has been configured as your default data service in msfconsole with the name "local-https-data-service"
If needed, manually reconnect to the data service in msfconsole using the command:
db_connect --token 1852b337c09cf94b7ea9a467d3cab4c2dc78ae19e3e8620df21cf743a36ecf68308de0fdaae02eb4 --cert /home/jmutai/.msf4/msf-ws-cert.pem --skip-verify https://localhost:5443
The username and password are credentials for the API account:
https://localhost:5443/api/v1/auth/account
This will create an initial database schema, set service account and start services. Output similar to below should be printed.

Use printed credentials to access MSF Web Service & API.
Check your Framework version using:
$ msfconsole --version
Framework Version: 6.3.10-dev-
Launching msfconsole
Now that database is initialized, you can launch msfconsole
$ msfconsole
`:oDFo:`
./ymM0dayMmy/.
-+dHJ5aGFyZGVyIQ==+-
`:sm⏣~~Destroy.No.Data~~s:`
-+h2~~Maintain.No.Persistence~~h+-
`:odNo2~~Above.All.Else.Do.No.Harm~~Ndo:`
./etc/shadow.0days-Data'%20OR%201=1--.No.0MN8'/.
-++SecKCoin++e.AMd` `.-://///+hbove.913.ElsMNh+-
-~/.ssh/id_rsa.Des- `htN01UserWroteMe!-
:dopeAW.No<nano>o :is:TЯiKC.sudo-.A:
:we're.all.alike'` The.PFYroy.No.D7:
:PLACEDRINKHERE!: yxp_cmdshell.Ab0:
:msf>exploit -j. :Ns.BOB&ALICEes7:
:---srwxrwx:-.` `MS146.52.No.Per:
:<script>.Ac816/ sENbove3101.404:
:NT_AUTHORITY.Do `T:/shSYSTEM-.N:
:09.14.2011.raid /STFU|wall.No.Pr:
:hevnsntSurb025N. dNVRGOING2GIVUUP:
:#OUTHOUSE- -s: /corykennedyData:
:$nmap -oS SSo.6178306Ence:
:Awsm.da: /shMTl#beats3o.No.:
:Ring0: `dDestRoyREXKC3ta/M:
:23d: sSETEC.ASTRONOMYist:
/- /yo- .ence.N:(){ :|: & };:
`:Shall.We.Play.A.Game?tron/
```-ooy.if1ghtf0r+ehUser5`
..th3.H1V3.U2VjRFNN.jMh+.`
`MjM~~WE.ARE.se~~MMjMs
+~KANSAS.CITY's~-`
J~HAKCERS~./.`
.esc:wq!:`
+++ATH`
`
=[ metasploit v6.1.14-dev- ]
+ -- --=[ 2178 exploits - 1154 auxiliary - 399 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Search can apply complex filters such as
search cve:2009 type:exploit, see all the filters
with help search
msf6 >Verify database connectivity with the db_status command as shown below.
msf5 > db_status --token 1852b337c09cf94b7ea9a467d3cab4c2dc78ae19e3e8620df21cf743a36ecf68308de0fdaae02eb4 --cert /home/jmutai/.msf4/msf-ws-cert.pem --skip-verify https://localhost:5443
[*] Connected to remote_data_service: (https://localhost:5443). Connection type: http. Connection name: local-https-data-service.Updating Metasploit Framework
To update your Metasploit Framework on Debian 11/10/9. run the command:
$ msfupdate
Switching to root user to update the package
Updating package cache..OK
Checking for and installing update..
Reading package lists... Done
Building dependency tree
Reading state information... Done
metasploit-framework is already the newest version (6.3.10+20230330102641~1rapid7-1).
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.To ameliorate your understanding of Metasploit Framework, visit Wiki page.
- Install and Use Linux Malware Detect on CentOS / Fedora / Ubuntu / Debian
- Vuls – Best Vulnerability Scanner for Linux / FreeBSD / WordPress / Network
- How to Install and Configure OPNSense Firewall
- How to Install Nessus Scanner on Ubuntu