UDP scanning is a process in which we scan for the UDP services that are being deployed on the target system or are currently in a running state. UDP is a connectionless protocol, hence it is hard to probe as compared to TCP.
Working of UDP scan:
In UDP scan usually, we take advantage of any UDP service clients like dig or tools like Nmap to send UDP datagrams to the target UDP network services like DNS, SNMP, and DHCP and wait for the response. Besides this, we can also send the UDP datagrams to all the ports and wait for the result.
Some popular services that we look for in UDP scan are:
UDP SCAN Using NMAP:
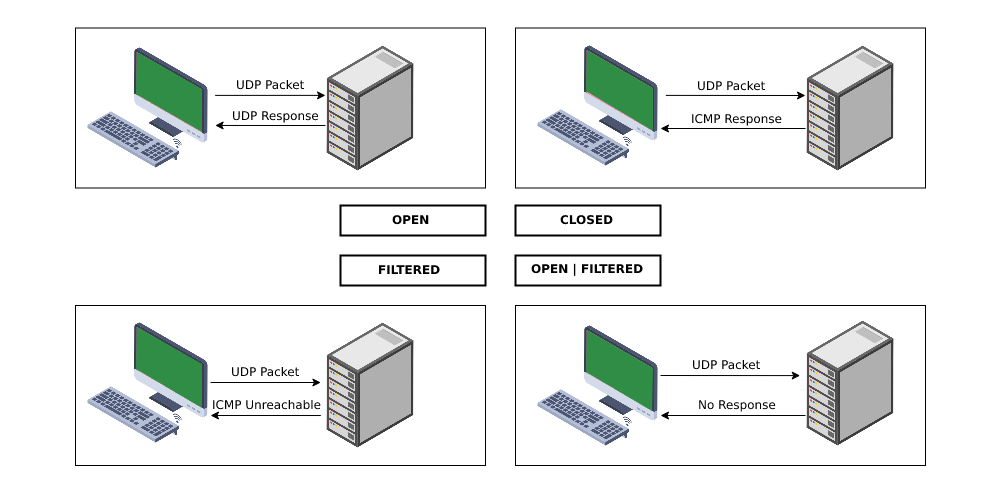
UDP scan works by sending a UDP packet to every targeted port. For most ports, this packet will be empty (no payload), but for a few of the more common ports, a protocol-specific payload will be sent. Based on the response, the port is assigned to one of four states. The result table looks like this in a Nmap UDP scan:
| State | Response |
|---|---|
| open | Any UDP response |
| open | filtered | No response registered |
| closed | ICMP port unreachable error (type 3, code 3) |
| filtered | Other ICMP unreachable errors (type 3, code 1, 2, 9, 10, or 13) |
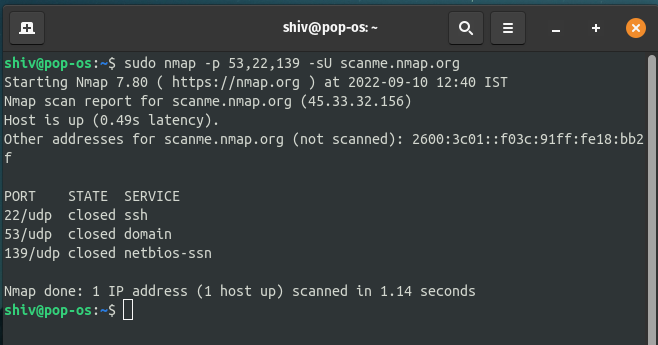
nmap’s UDP scan usage command:
sudo nmap -p <port numbers> -sU <target domain>
Example:
Conclusion:
For UDP scanning, the service sends a generic UDP packet and waits for a response. If there is no response, the port is assumed to be open and a UDP packet specific to the service on that port is sent to detect the service. If an ICMP error packet is returned, the port is considered closed.




