A DNS Rebinding attack takes advantage of the fact that typically when an attacker exploits a vulnerability (such as Cross-Site Scripting—XSS) in order to compromise a domain, the domain’s name server is also hijacked. This can change the hostname for which an individual is resolving. In other words, via DNS Rebinding Attack, a specially crafted website can be accessed by sending requests to name servers of compromised domains rather than requesting addresses of actual websites. In addition, all traffic sent to those different IP addresses will now be relayed back to our web server even if it is not a malicious URL such as *.youtubefilter.com or anything else commonly used during phishing scams and other types of online attacks.
Mechanism of DNS Rebinding Attack:
DNS Rebinding attacks are vectors where the attacker has no control over the nameserver and all requests to resolve a hostname (or IP Address, which is still a valid hostname) are redirected to an alternate name server that is controlled and operated by the attacker. For example, if we have a website at www.example.com, and we want to access a private internal domain mail server or other services which are only reachable via this specific private IP address, then a DNS Rebinding Attack can be used to fake one of these addresses.
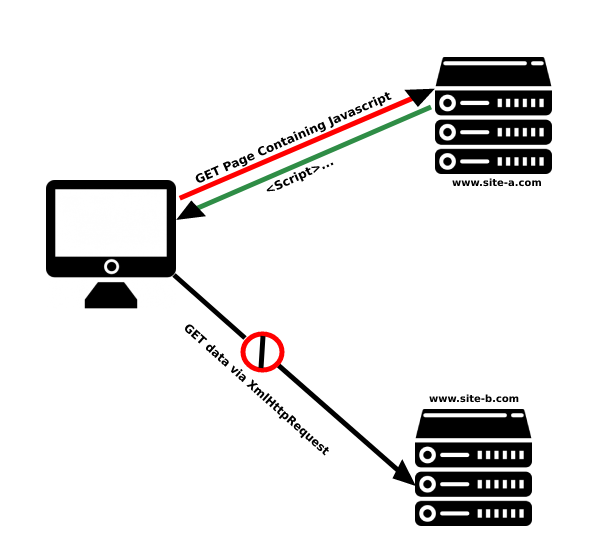
Network Pentesting via DNS Rebinding Attack:
360 NOC has observed several cases where the attacker hijacks DNS and sends requests to request IP addresses that belong to legitimate domains. In some cases, end users are tricked into creating a phishing website using one of these websites (for example, a private email server). Since all traffic sent to the hijacked URL is now being sent back to the original server, it gets completely confused and forces the user to install a phishing page as a result.
Data Leakage Issues:
DNS Rebinding Attack allows an attacker access to sensitive information such as credentials or confidential emails.
Example of DNS Rebinding:
In this example, Alice has set up her computer to use the Internet Service Provider (ISP) of John and Jane’s ISP instead of Google. When you type in “google.com” in either browser window, it sends a request through Alice’s computer and onto John and Jane’s ISP. When the request is sent, it is redirected to the DNS server of the ISP, which in turn sends the request to Google. A hacker will have configured their computer to use the DNS server and associated IP address of John and Jane’s ISP for the website when you type in any form of an address, such as “google.com.” DNS rebinding is a pretty simple attack that basically runs in a browser window like any other form of web browsing. It basically acts as a proxy attack that redirects traffic from one intended destination to another. The process goes like this:
- The attacker names something they want you to click on in the address bar (DNS lookup).
- They enter an IP address they can easily access (ISP DNS server).
- They press enter, and the destination appears on your browser page.
- You think you are going to Google – you type in the address bar, for example, “www.google.com” or “facebook.com.”
- As soon as you hit enter, your DNS servers have changed and forwarded the request to John and Jane’s ISP (IP address). Your browser thinks it’s going to Google, but really it’s going to John and Jane’s ISP – this is called “DNS Rebinding” with a little help from an attacker.
- You are now basically on John and Jane’s ISP.
- Your browser is then redirected to www.google.com or www.facebook.com, etc., without you knowing that the IP address has been changed by the attacker
- You don’t know you’re actually in John and Jane’s ISP – it looks like you are still at Google/Facebook, etc., because your DNS server has been changed by the attacker
- When you log into Facebook or Google, your username and password sent via HTTP request are logged by an attacker. The attacker now stores your password.
- Hackers can now take over your information and do whatever they want with it, including selling it or using it in other criminal activities like identity theft.
- If you are fortunate enough to get alerts from a security program (I like Kaspersky’s), you may survive the attack if you’ve taken precautions against DNS rebinding attacks (such as setting your DNS to Google’s IP address)
- When the hackers send a request for specific information, Your computer may redirect the request to another computer.
- It’s a different IP address and domain name altogether, but it’s using the same IP address and domain name as before (from your ISP). This is called DNS Rebinding attacks.
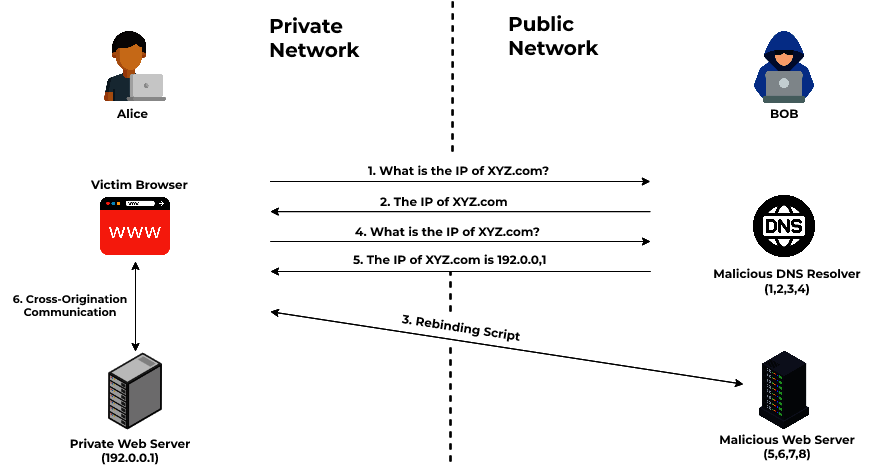
Conclusion:
A DNS Rebinding attack takes advantage of the fact that typically when an attacker exploits a vulnerability (such as Cross-Site Scripting XSS) in order to compromise a domain, the domain’s name server is also hijacked. This can change the hostname for which an individual is resolving. In other words, via DNS Rebinding Attack, a specially crafted website can be accessed by sending requests to name servers of compromised domains rather than requesting addresses of actual websites. In addition, all traffic sent to those different IP addresses will now be relayed back to our web server even if it is not a malicious URL such as *.youtubefilter.




