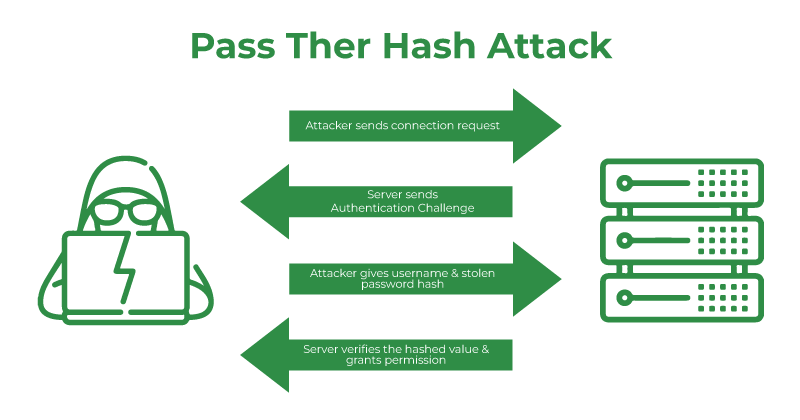
The Pass-the-Hash technique is published or established by Paul Ashton in 1997 and later it is modified or updated as a Samba SMB client in which it can accept the user password hashes instead of plain text passwords.
The Pass-the-Hash Attack is the technique in which a hacker or an attacker captures the password in a hash function. After that, it passes through authentication and probably has an access to the other networks. The attacker does not need to decrypt the hash for obtaining the plain text password. The attacker obtains the hashes by dragging the system active memory and different techniques.
Pass-the-Hash occurs in different operating systems such as Linux and Unix but it is more common in the windows operating system. In Pass-the-Hash Attack allows the attacker to authenticate in a remote server. This technique is performed against any server.
Once the password is created in the windows server it will save in any active directory of the system or in a Security Accounts Manager.
Prevention from Pass-the-Hash Attack:
For preventing the Pass-the-Hash attack there are three types:
1. PMS (Password Management Solutions): The PMS is an advanced tool in the operating system which allows the user to reset their passwords if they forget or they have some insecurity that someone knows their passwords so they can change this tool. The PSM saved all the passwords in the database of PSM and securely saved the password in encrypted form. Once the password is generated after that it will be saved in the centralized vault and encrypted in one master password.
2. Least Privileged Security Model: Removing unnecessary rights of the admin or user will reduce the threat of Pass-the-Hash or any other attacks. The Least Privileged Security Model gives the admin limited rights so that it will reduce the chances of attacks or threats.
3. Separation of Privileges: Separating all the different types of Privileges such as privileged and nonprivileged accounts reduces the chances of threats because of the least usage and scope of administrator accounts and the risks of compromises or opportunities for the upcoming movements.