In a client-server architecture, there can be one or more servers in the way, forwarding your request to the destination server in the most efficient way possible. These are known as Proxy servers.
When there is an unwanted proxy in the network that intercepts and modifies the requests/responses, then this proxy is called a Man in the middle. This rogue proxy is often misunderstood as a legitimate access point in communication by the clients. In this article, we will discuss the steps to create a fake access point using the Wi Hotspot tool to redirect the flow of packets to go through our computer in order to become the man in the middle. Once it happened, we can analyze those packets and run many dangerous and effective attacks. We can also spy on all the users, steal their passwords or redirect them to different websites.
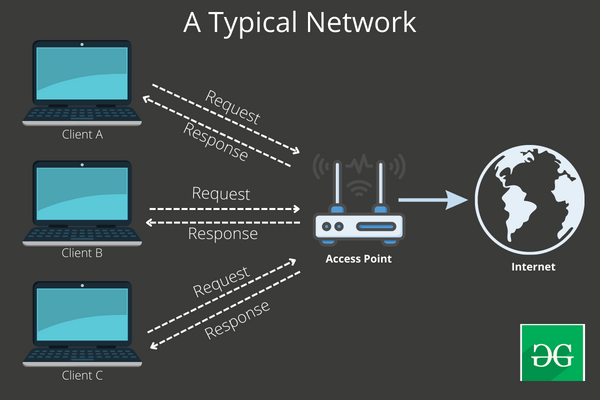
As seen from the above diagram, the only device that has access to the internet is the access point, and whenever a client wants to access something from the internet, they send the request to the access point. The access point on behalf of the client gets the response from the internet and sends it back to the client. Now, if the attacker replaces this access point with its own rouge access point or computer that actually has access to the internet then by default the attacker will be the man in the middle and obviously, all the requests can be monitored, intercepted, or dropped in transit using tools like Wireshark, Bettercap and Burp Suite.
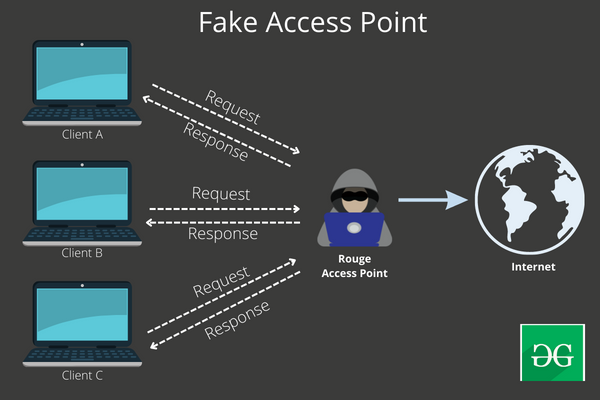
Fake Access Point
Attack Requirements :
- An interface that has an internet connection. It could either be connected to the internet via Wi-Fi or Ethernet or a virtual interface like VMWare.
- A wireless 2.4/5 GHz adapter that supports Monitor mode and SoftAP mode (software enabled access point). This can be used to broadcast a Wi-Fi signal like a router.
Fake Access Point Using Wi Hotspot Tool :
Now for the demonstration purpose, we are Kali-Linux(Debian 5.10.13-1kali1) as a virtual interface in VMWare with network setting enabled as NAT Network it will provide the Kali machine with internet access as long as the host machine right here(Windows11) has internet access. We can create a fake access point using the program called Wi Hotspot.
First, we need to install the required dependencies and then start cloning the program from its GitHub repository into our Kali machine. Follow the steps below to install the tool :
- Installing Dependencies On Ubuntu or any Debian-based distros :
sudo apt install -y libgtk-3-dev build-essential gcc g++ pkg-config make hostapd libqrencode-dev libpng-dev
- Installing Dependencies On Fedora/CentOS/Red Hat Enterprise Linux/Rocky Linux/Oracle Linux :
sudo dnf install -y gtk3-devel gcc gcc-c++ kernel-devel pkg-config make hostapd qrencode-devel libpng-devel
- Now to start cloning the program, fire this on your terminal :
git clone https://github.com/ lakinduakash/linux-wifi-hotspot
- Now move to the Linux-wifi-hotspot directory and fire the below commands one by one :
make sudo make install
Now just type “wihotspot” on the terminal to start using the GUI-based tool.
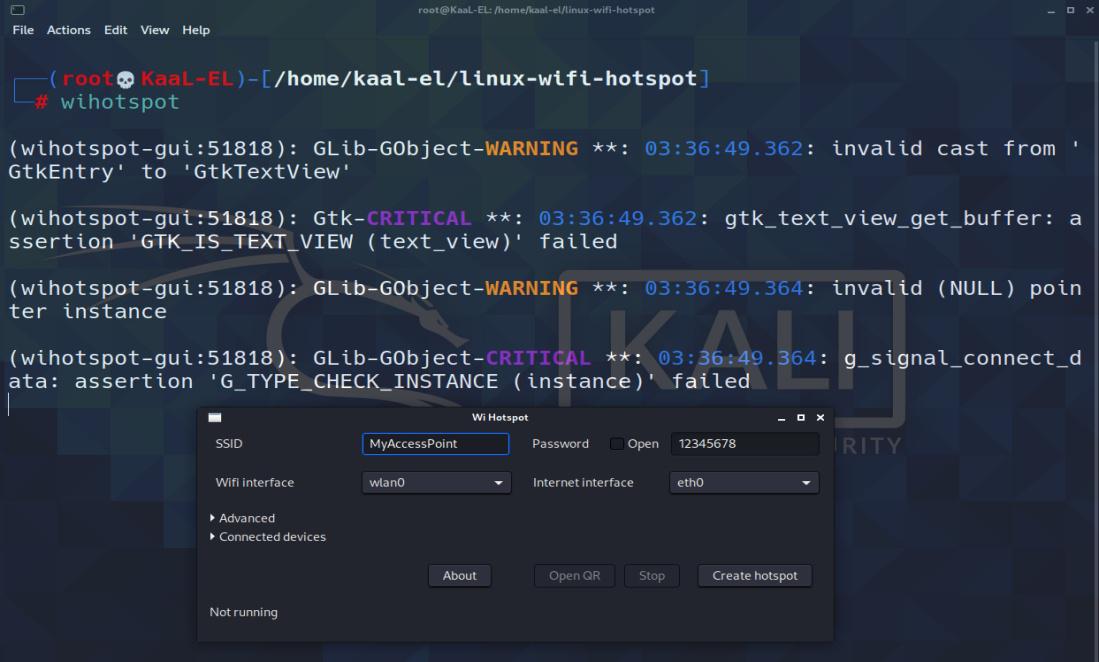
Steps to Create a Fake access point :
- First, set the SSID or name of the network that the clients will see when they look for Wi-Fi networks around them.
- Tick the Open checkbox so that the access point is open so that we can attract more people and spy on their traffic.
- Leave the Wi-Fi interface option as wlan0. This is the interface that will be broadcasting the signal.
- Leave the Internet interface option as eth0. This is the interface that will provide the fake access point with internet access.
- Now click on Create hotspot. It starts running, and it will give the process ID that it’s running through, just in case it freezes, and you need to kill it through the terminal.
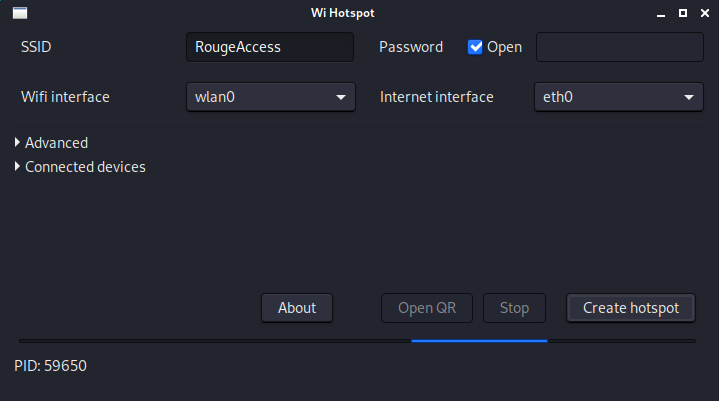
Now we have a fake access point that looks like a real Wi-Fi network with internet access that is broadcasting within our range, and the name of this wireless access point is RougeAccess. Now you can test it from your phone or from another laptop or any other computer within range.
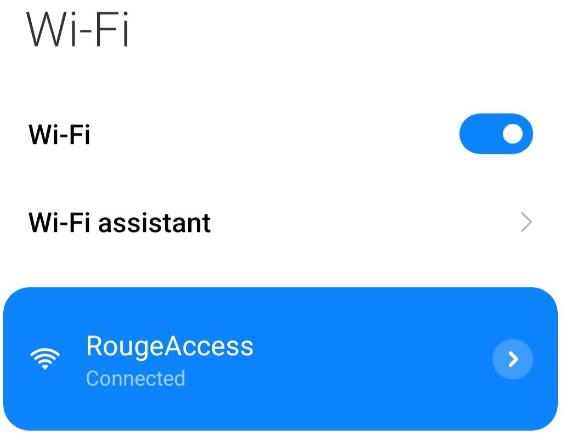
Now, if we want to access any websites or enter any passwords and usernames, everything goes to the access point. And the access point is the hacker machine. Now we can use Wireshark to sniff packets and analyze them or use Bettercap exactly for the same purpose.
Note: This article is only for educational purpose.




