Cyber security or security of the web deals with the security mechanism of the cyber world. Cyber security is extremely necessary as it is important that computer networks have strong cyber security mechanisms set up to prevent any form of attack that may lead to compromise of computer network security. Proper awareness about cyber attacks can help in preventing cyber attacks to a large extent.
Here, in this article, we will discuss backdoor attacks in detail including what is a backdoor attack, the aim behind backdoor attacks, the types of backdoor attacks, and the different ways to prevent backdoor attacks.
Aim:
The mechanism of a backdoor attack includes processes that breach the authentication security of the system. The security of the application is exploited by providing remote access to certain resources of the application. The cyber attackers then take advantage of using the remote part to execute malicious code into the system.
In a backdoor attack, the authenticated system of the computer network faces backlash as security is compromised and access to resources is forcefully taken access by cyber attackers.
The attackers are not allowed to access to make changes in the computer system and use it to their benefit for executing malicious code and viruses, including harmful malware. The remote access granted to the attacker unable them to perform security threat operations irrespective of the location from where they try to execute the attack. All the security policies are breached and attackers get administrator access to the system through this attack. A backdoor attack is a form of DDoS attack and serves as a gateway for malware to enter the computer network security.
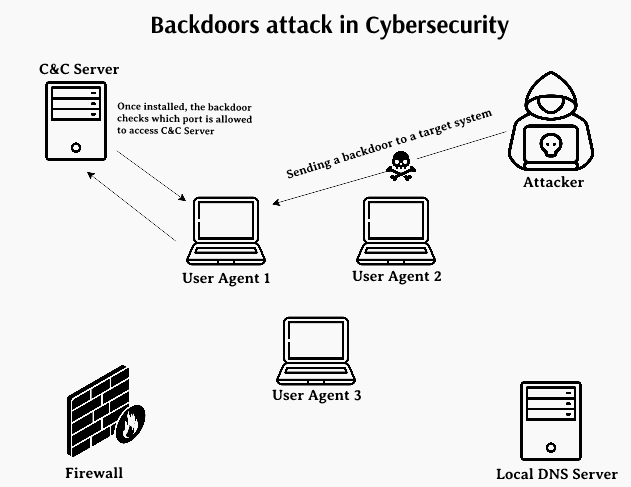
Types of Backdoor Attack:
There are two different types of Backdoor attacks. They are as listed as follows –
1. Administrative Backdoor Attack: Software developers create backdoor pathways seldom in their program so if by chance any failure is recorded into the computer system then the developers will have access to the code and can help to involve the problem. Cyber attackers can take advantage of this backdoor pathway and can get into the system to access it in an unauthorized way and leading to backdoor attacks in computer network architecture.
2. Malicious Backdoor Attack: A malicious Backdoor Attack occurs when the program gets into the system through harmful malware.RAT (Remote Access Trojan) is used by cyber attackers for installing malicious backdoor programs.
Prevention of Backdoor Attack:
Listed are some ways to prevent Backdoor attacks from taking place:
- Continuous Monitoring of Security System: Monitoring the system network helps in checking loopholes that may turn into potential entry points for backdoor attacks.
- Having Strong firewalls in Computer Network: Firewall filters the traffic in a computer network and a strong firewall can prevent attackers from getting into the system.
- Protection of computer networks through Strong Passwords: Having a strong password helps in establishing the strong security of the system. Users should never stick to default passwords and should always have passwords that are difficult to crack.




