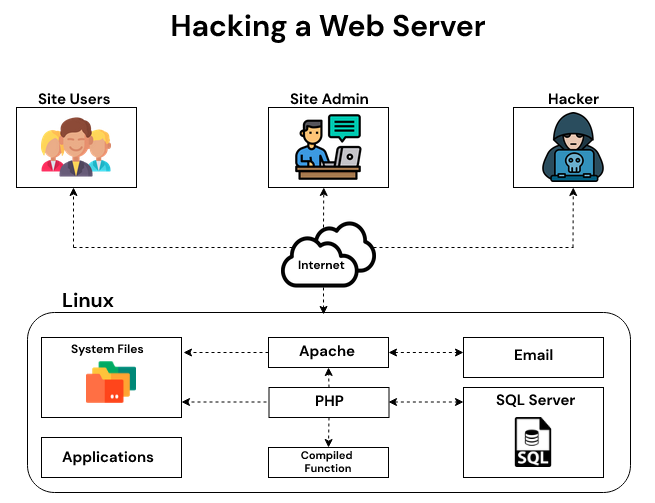
There are a lot of different ways you can hack a web server, but the easiest way is to use something called an SQL Injection, which involves executing operating system commands on the web server. If you know how to do this, then your next step would be to run commands like “flush cache” and “delete all files” in order to delete data that was stored on the server. Afterward, you might want to access other websites on the same network, so they can see what data was deleted. This is where Simple Port Scan comes in handy. A simple port scan is like looking through a house window at night to see if anyone is at home. On a Windows server, this type of scan will show you open ports and running services.
Web Server Hacking:
Once you know what ports are open, you can use some more operating system commands, like tracert and ping – to get information about the network. If you want to go even further, you can use the netcat utility to actually connect to web servers on the network and capture any data that are sent from them (like usernames and passwords). This is a very powerful technique because it gives you instant access to all of their internal network resources.
Finally, you should always use a convert channel to get onto networks without being noticed. This involves using a public protocol to transmit data that is normally used for something else. For example, think of IRC (Internet Relay Chat). It’s used by computer enthusiasts to talk about technology and other geeky stuff. However, it was actually created over twenty years ago as an alternative way of transmitting data on the internet. The biggest advantage is that IRC doesn’t require a username or password, and it runs over TCP port 6667 by default. This makes it an excellent way of getting internal data from networks because they don’t have time to figure out what you are doing by capturing your packets.
Steps to Hack:
- Access the web server.
- Use anonymous FTP to access this network for further information gathering and port scanning.
- Pay attention to file sizes, open ports, and running processes on the system.
- Run a few simple commands on the web server like “flush cache” and “delete all files” to highlight what data is being stored by the server behind these programs. This may help you get more sensitive information that you can use in an application-specific exploit.
- Connect to other websites on the same network as Facebook and Twitter, so they can see what data was deleted.
- Use a convert channel to access the server.
- Access internal network resources and data to gather further information.
- Use Metasploit to gain remote access to these resources (see also, Metasploit Ethical Hacking Edition e-book download).
Key Points:
- Using an SQL Injection to hack a web server is quick and easy, making it an excellent tool for a beginner.
- Analogously, accessing internal network resources in “hacking” through a public connection on the internet like IRC is simple and fast.
- SQL Injection can be used to gain access to other networks on the same subnet through a convert channel.
This is called using a “Simple Port Scan”. This can help you gather information about network resources that might be useful for further exploitation.
Countermeasures:
- If your server is running a firewall, you can easily deny port 80 and 6667 access to the outside world by temporarily disabling them in the configuration.
- If you are using Metasploit to get remote access, you should select a different tool (such as Burp or Nmap) to help disable your web server and then test it repeatedly until you successfully retrieve data.
- Your best protection against SQL Injection is to create a new database on your web server that has only tables that are physically stored on the server.
Conclusion:
If you are running your own web server, it’s a good idea to keep the software up to date. This includes keeping up with Java, PHP, and Python since they all have flaws that can cause security issues. Also, make sure your operating system is upgraded, so it has the latest patches from Microsoft. This can help prevent any inbound or outbound vulnerabilities that an attacker could use to gain access or disrupt service on your web server. Finally, you should talk with a professional about how to create a new database on your web server and then create real-time monitoring for any unexpected activity.
Note: This article is only written for educational purposes.




