In order to protect systems from cyber attacks, it is important to discover and fix vulnerabilities. Xerosploit is a penetration testing toolkit designed to perform man-in-the-middle attacks to discover vulnerabilities, malicious content, bugs and risks. Penetration testing is an authorized simulated cyber attack on a computer system to evaluate the security of the system. Xerosploit has various different types of modules that help in efficient attacks and features like denial of service attacks, port scanning, etc.
Dependencies for Xerosploit:
There are various types of Dependencies that are used by Xerosploit, Some of them are given below:-
- nmap
- build-essential
- ruby-dev
- libpcap-dev
- libgmp3-dev
- hping3
- tabulate
- terminal tables
Installation of Xerosploit
You can download and install this tool in your ubuntu, kali Linux os with git by typing the following command in the terminal.
git clone https://github.com/LionSec/xerosploit
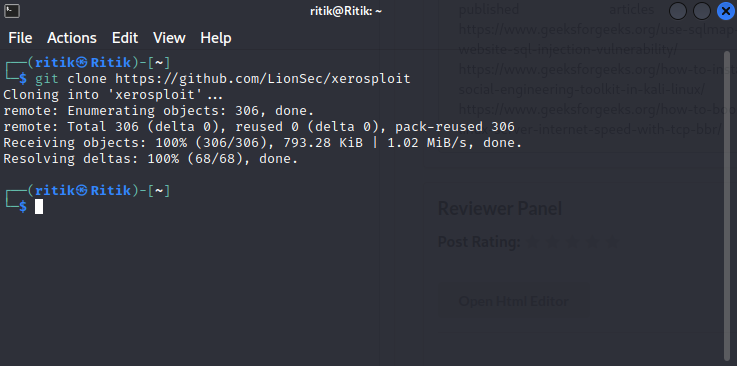
cd xerosploit && sudo python install.py
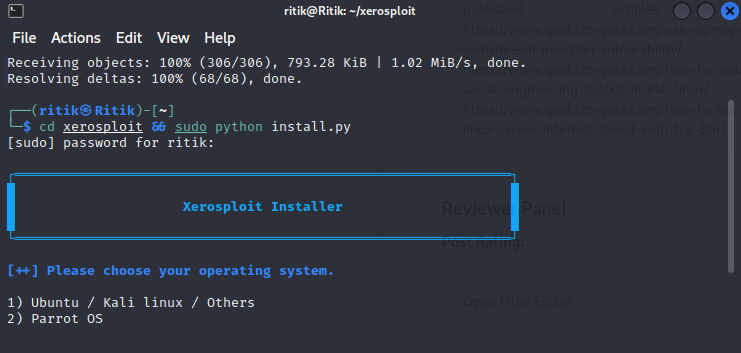
Now you have to choose the option 1 or 2 as per your operating system, make sure you enter your choice in string format because the python script takes input as string if you try to enter integer you will end up getting a error or just nothing. The valid input is shown in the image below.
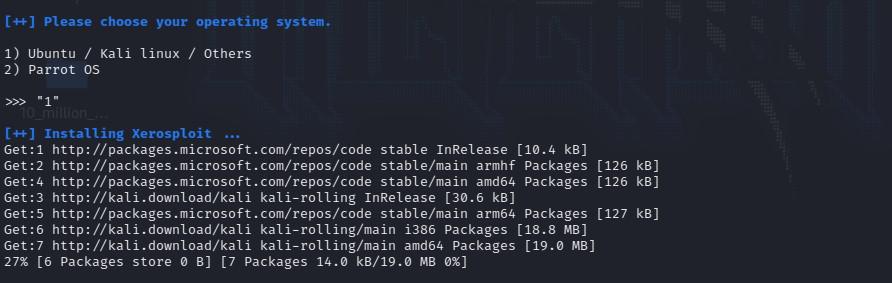
As you can see that I have entered option 1 in quotes (string), after that the installation starts.
sudo xerosploit
Also, you can simply download the file of Xerosploit from the below given link.
https://github.com/LionSec/xerosploit
Features of Xerosploit:
Below are some of the features of Xerosploit but not limited:-
- DOS Attack: In a DOS Attack, an attacker sends a large amount of traffic to a victim’s System and shuts it down. A Dos attack is an online attack that is mostly used to shuts down the target website for its users. This attack overloads the server of a website by sending a lot of traffic. As of result, the Server goes slow and doesn’t respond to the visitor.
- Port Scanning: Port Scanning is a technique that is used to discover online (available) ports and to find out whether there is a weak point in a network by which data can be received or sent. Mostly port scanning is used by security engineers to discover vulnerabilities in the network. It also helps hackers in revealing whether an organization is using security devices like firewalls or not for protection.
- DNS Spoofing: In Spoofing, psychologically manipulating the victim is the main objective of any hacker. Domain Name Server (DNS) spoofing is an attack that uses modified DNS records to redirect online traffic to a fraudulent website. With the help of this attack, security engineers can also find holes in the Server, which helps them to prevent redirecting traffic to a fraudulent website.
- Sniffing: Sniffing is the process of monitoring all the packets passing through the network. Network administrators often use sniffers to monitor and troubleshoot network traffic. Attackers use sniffers to monitor and capture packets to steal sensitive information including passwords and user accounts.
- Network mapping: Network mapping is the study of the physical connectivity of networks, such as the Internet. With the help of Network mapping, security engineers and hacker easily discovers the devices on the network and their connectivity.
- HTML code injection: HTML code injection is an attack in which hackers discover a vulnerability that allows hackers to easily inject HTML code into web pages, and it is visible to other users.
- JavaScript code injection: Just like HTML code injection, it is a security hole that allows hackers to inject JavaScript code into web pages. JavaScript’s code may be hidden or visible to users, and it is stealing information from the user.




