TCP Intercept is a mechanism that protects end hosts from TCP SYN-flooding attacks, a type of DoS attack. An SYN-flooding attack occurs when a hacker floods a server with many connection requests. A connection cannot be established because the sender address for these messages is unreachable. The resulting amount of outstanding open connections can eventually overwhelm servers, preventing legitimate users from connecting to websites, accessing email, using FTP services, etc. May reject valid requests. Validation of TCP connection requests. TCP Intercept has been used by people to do things such as turn an entire network into a wireless access point for another network. It can also be used for legitimate purposes, such as creating a firewall for a specific guest Wi-Fi network. TCP intercept works by blocking packets from leaving or entering your computer in specific ways based on rules you create.
Intercept mode:
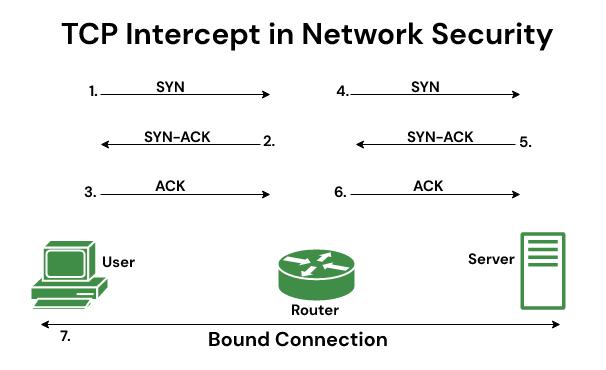
TCP interception software intercepts TCP synchronization (SYN) packets from client to server that match the extended access list. The computer software set up a connection with the client on behalf of the endpoint of the server and, if successful, establishes a connection with the server on behalf of the client and transparently bridges the two halves of the connection. As a result, connection attempts from unreachable servers will never reach the server. The software continues to intercept and forward packets for the duration of the connection. The number of syncs per second and the number of concurrently connected proxies depends on the platform, memory, processor, and other factors. In the event of an illegal request, the software’s active timeout on semi-open connections and its thresholds for TCP connection requests will protect the destination host while still allowing requests.
Configuration:
1. Using NAT:
[no] static (real_ifc, mapped_ifc) <mapped_ip> <real_ip> netmask <mask> tcp <max_conns> <emb_lim> ciscoasa(config)# static (inside,outside) 1.2.3.4 5.6.7.8 netmask 255.255.255.255 tcp 0 10 <max_conns>: The maximum number of simultaneous TCP connections that each <real_ip> hosts will be allowed. <emb_lim>: The maximum number of embryonic connections per host.
2. Using Modular Policy Framework:
policy-map <name>
class <class_map_name>
set connection {[conn-max n] [embryonic-conn-max n]
[per-client-embryonic-max n] [per-client-max n]
[random-sequence-number {enable | disable}]}
ciscoasa(config)# policy-map global_policy
ciscoasa(config-pmap)# class class-default
ciscoasa(config-pmap-c)# set connection embryonic-conn-max 1
<conn-max>: The maximum number of simultaneous TCP
and/or UDP connections that are allowed.
The default is 0, which allows unlimited connections.
<embryonic-conn-max>: The maximum number of simultaneous
embryonic connections allowed. The default is 0,
which allows unlimited connections.
<per-client-embryonic-max>: The maximum number of
simultaneous embryonic connections allowed per client.
The default is 0, which allows unlimited connections.
<per-client-max>: The maximum number of simultaneous c
onnections allowed per client. The default is 0,
which allows unlimited connections.
<random-sequence-number>: Enables or d
isables TCP sequence number randomization.
3. Using Threat-Detection:
In order to enable TCP intercept statistics, use the threat-detection statistics TCP-intercept command.
ciscoasa(config)# threat-detection statistics tcp-intercept
In order to configure custom rates for TCP intercept statistics, use the rate-interval, average-rate, and burst-rate keywords.
ciscoasa(config)# threat-detection statistics tcp-intercept rate-interval 45 burst-rate 400 average-rate 100
The Threat of TCP Intercept:
If you set up a firewall that blocks outbound ports and users aren’t able to get out, they will either try to find another way, which could lead to them being hacked because they gave their credentials away, or they can reboot the computer and allow everything through until you fix the firewall. This feature is meant only for advanced users who know how to handle it properly, and others should not attempt it.
Countermeasures:
- Always test your firewall rules in a lab environment before deploying them to a production environment.
- Make sure you write the rules correctly, so they only block what you want and nothing else. Use a lab network or isolated network to test new rules. This way you won’t affect other users or services.
- Block everything by default, and only open the ports required for services to work on your firewall/router.
- Do not leave blocking rules enabled when they are not needed, such as when using your computer normally or during off-hours when no one is around in the office.
Advantages:
- TCP intercept in Linux/Unix-based systems is generally easier to use than in Windows.
- TCP Intercept allows you to block TCP/UDP ports that you do not need. As an example, you could open all ports 7, 16, and 17 for HTTP but block the entire port range of 80, 9000, and any other port’s range.
There are many options for TCP Intercept in Linux/Unix systems:
iptables , nftables . nfmatch . arpwatch . arping . tcpdump . iptable -L. ipset . iptables -X. ipchains.
Conclusion:
TCP Intercept can be a powerful and useful tool for learning about networking and as a firewall for your network, but it also has the potential to cause problems if not handled properly. Before implementing it on your network, make sure you test the rules in a lab environment first and have them reviewed by someone with experience in this field.




