TCP-ACK is a third step of the TCP 3-Way Handshake process (SYN, SYN-ACK, ACK). In TCP-ACK, the client acknowledges the response of the Server, and establish a connection to proceed with the data transfer and any other communication processes.
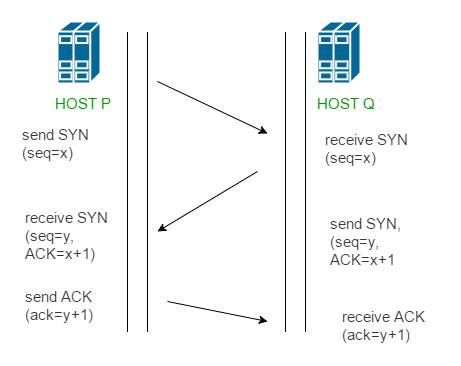
TCP-ACK Scanning:
In this scan, the ACK packets are sent to the target port in order to know that if that port is filtered or unfiltered. In case of filtered port, the response will be either no response or an ICMP destination unreachable reply packet will be shown. In case of unfiltered port, an RST reply packet will be sent to all the open and closed ports.
Procedure:
This can is useful when the firewalls are stateless, i.e., they block all the incoming connections by just blocking the first packet of this TCP 3-Way Handshake process, i.e., SYN packets. But the stateless firewall allows ACK packets because of the stateless firewall allows internal hosts to communicate with the rest of the internet.
This scan doesn’t work for the stateful firewalls. To demonstrate, we will use a simple yet very powerful scanning tool called NMAP.
ACK scan command usage:
nmap -sA -T4 <anydomain address>
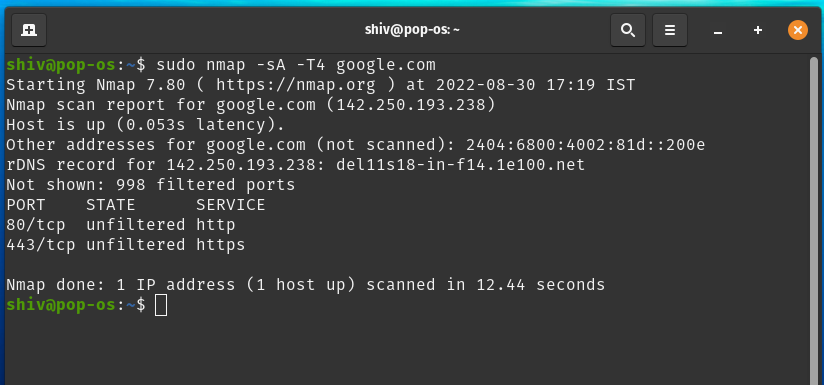
Typical Probe Response looks like with their state:
- TCP RST response – unfiltered
- No response received – filtered
- ICMP unreachable error – filtered
In the above nmap scan result, you can see in the result about states, services, and ports after a successful TCP ACK scan.
| PORT | STATE | SERVICE |
|---|---|---|
| 80/tcp | unfiltered | http |
| 443/tcp | unfiltered | https |
Prevention:
- First things first, always have a firewall setup for filtering these types of scans.
- Always configure the server with best practices.
- Monitor all the scan, that are being performed on the server.




