Internet and its usage have evolved over the years. The Internet has become an integral part of daily human activities, and it becomes hard to imagine life without the Internet. The Cyber world has become so fascinating that it is often the soft target of cyberattackers and hackers to steal personal confidential information via the internet as a medium. Unauthorized people/ hackers take the help of cyberattacks as a medium to get access to users’ or organizations’ private confidential data. This has resulted in cyber crimes has grown over the past few years.
Cyberattackers use computer networks as a medium to execute the malicious attempt of getting into computer systems. There are different types of cyberattacks that are observed to be attempted by cyberattackers. Each of the cyberattacks is dangerous as it breaches individual/ organizational privacy in its own unique way. Cyber crimes are punishable by law and cyber attackers are identified as criminals for executing malicious cyber fraud.
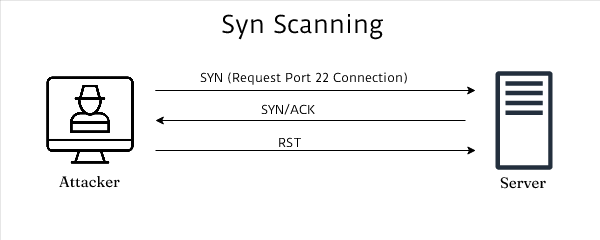
SYN Scanning:
- SYN scanning involves the establishment of a half connection with the destined target.
- SYN scanning does not involve a full connection establishment, and thus it is also referred to as a half-open scanning technique.
SYN Scanning Process:
- SYN scanning attack involves the mechanism where an SYN packet is sent to an open connection.
- There are two conditions that arrive at this mechanism. They are listed below :
First, if the response/result from the computer or server is SYN-ACK, then it directly indicates an open port in the connection. The client then unknowingly sent RST packet, and it makes the server believe that client has not yet asked for the connection establishment and the port remains in the open state.
Second is the case when a server sends an RST packet from a destined port showing that the port is closed and secured. In such cases, the hacker sends a huge volume of SYN packets then the server accepts those packets but no communication or connection establishment between Client and server takes place there.
An SYN Scanning is preferred by attackers because SYN scanning is generally adopted by hackers as it is fast in execution and easy to cause harm to the computer/server using the SYN Scanning process. Another advantage of SYN Scanning that hackers find is the speed with which open ports are detected.
Prevention from SYN Scanning:
To prevent SYN Scanning attacks, users/ organizations with computer systems should ensure the following:
- Proper firewalls are set up in a computer network system which blocks suspicious calls to the user setup.
- Proper security is present by ensuring that there is ‘No open ports’ present in the cyber network setup that can be used by cyberattackers to breach the vulnerability of the system.




