Cyber attacks are extremely dangerous attacks executed on the Internet. Cyber attacks give unauthorized access to hackers/ cyber criminals of the users or the organizations of the computer system. Modern times have recorded a huge increase in cyber attacks conducted every second. Cyber attacks are very dangerous in nature because the data which the cyber criminals aim for attacking is important to the user/ organization and confidential data has been stored on the computer systems for performing certain operations.
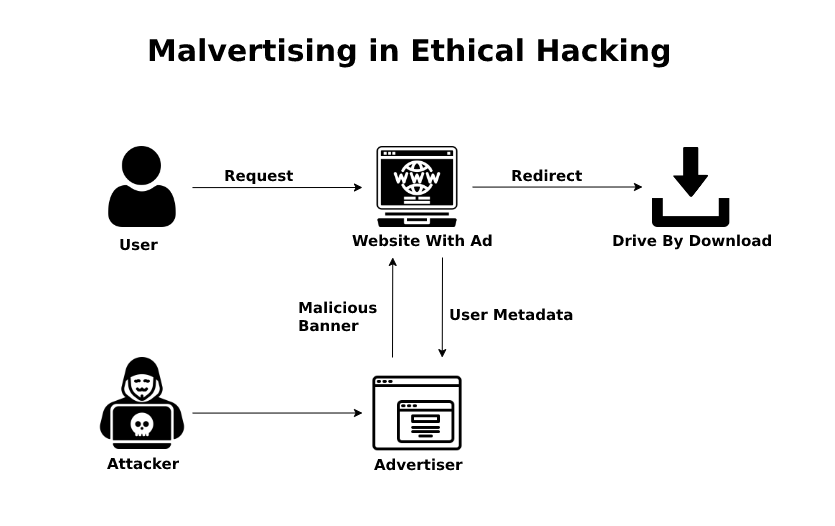
- Malvertising is a new form of attack adopted by cyber attackers that makes use of online advertisements for spreading malicious software into computer systems.
- Malvertising is the synonym for malware advertising. The mechanism of malvertising includes the injection of harmful malware/malicious code through advertisements that users unknowingly click. The click of the user then directs them to dangerous, malicious websites.
- Online advertisements that are authenticated by computer systems become dangerous when malvertising is a part of them.
Working:
- Malvertising attacks can be complex in nature and use many other techniques to execute the attack. Typically, attackers first compromise a third-party server that allows cybercriminals to inject malicious code into display ads or their elements, such as Banner ads, creative images, or video content.
- Once a website visitor clicks on it, the broken code in the ad installs malware (malware) or adware on the user’s computer. Attackers can also redirect users to malicious websites and use deception or social engineering techniques to facilitate attacks.
- Malvertising attacks can also run exploit kits, a form of malware designed to scan a system and exploit vulnerabilities or holes in it.
Example:
- Angler Exploit Kit: This malvertising attack is an example of drive-by downloads. It automatically redirects visitors to malicious websites, and exploit kits can exploit vulnerabilities in popular web extensions such as Adobe Flash, Microsoft Silverlight, and Oracle Java.
- RoughTed: RoughTed used the Amazon cloud, Content Delivery Network, and an ad exchange network to advertise through a changing URL campaign. This campaign was able to get past ad-blockers and many antivirus solutions. The cybercriminals behind RoughTed used this campaign to steal information from victims.
- KS Clean: It is a malvertising campaign targeting malvertising in mobile applications. Once downloaded, the malware triggers in-app notifications, alerting users to security concerns and prompting them to update the app. However, if the user agrees to the upgrade, the installation process does complete and the cybercriminal is granted administrative rights to their mobile device.
Impacts:
- The extremely complex advertisement system falls prey to cyber attackers that aim at targeting the content of the advertising ecosystem network. Malvertising affects all the users who access the malicious code injected web page.
- Ads impacted by malvertising are difficult to distinguish from normal ads, making them very dangerous when executed.
- Malware is injected through the following ways :
- Creative ads: Creative ads attract users to view and click on them, making them the prey to malvertising.
- Advertisement click: It is often observed that advertisement click is the most common way for malvertisement to take place. Users clicking on malicious advertisements get redirected to harmful websites.
- Calling of advertisements: The advertisement call process includes many devices and servers that typically end up being impacted by malicious code and falling prey to malvertising.
- Malvertising is a harmful cybercrime as it not only leads to loss of data but also loss of revenue and liability damages to authenticated users.
Countermeasures:
- Careful Inspection of Security Paths: Delivery paths should be carefully checked for advertisement. Unwanted code should not be a part of the computer system network.
- Well-protected Firewalls: Proper security policies and a wall-protected firewall can help in protecting computer systems from the injection of malicious code into them.
- Restriction of File formats: Restricting the allowed file format for ads also helps to prevent unwanted code from entering the system.
- Strong updated antivirus: Updated antivirus and browser plugins contribute to the protection of malvertising attacks.
- Proper Firewall: Ad blockers can also help in the protection from malvertising attacks as they together block all ads on the web page.
Conclusion:
Cyber attackers are guilty culprits just as any other criminals. The intent of cyber attackers behind exploiting the privacy of users is equally punishable in the eyes of the law. Cyber attackers deserve severe punishment for carrying out cyber attacks. Proper awareness about cyber attacks can help in the prevention of cyber crimes.