Cyber attacks are considered to be the most malicious attacks on user privacy in the cyber world. Cyber attacks give cyber criminals the power to unethically conduct activities that lead to the stealing of personal and professional information from the user/ organization systems. Knowledge about cyber attacks is thus very essential.
Malicious File Execution Attack:
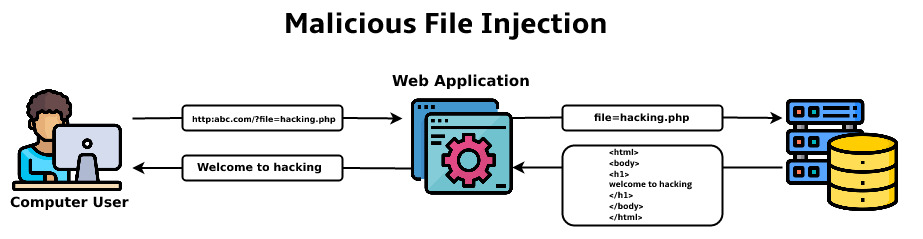
- Malicious file execution attacks are the attacks associated with users uploading harmful malicious code on the internet-facing website and the execution of the malicious code causing harm to the computer network system.
- Malicious file execution attacks are based on the principle that websites and web applications become more dangerous because they have granted access to users to upload files on them.
- Accepting files from the user makes the websites vulnerable to the execution of malicious files within them.
- Malicious file execution attacks usually take place when the websites are not properly validated.
- Examples of malicious file execution attacks include codes that allow local files from a computer system to be included.
- The improper validation makes the website malfunction when the user enters or uploads some kind of malicious file.
- Malicious files which are uploaded as a part of the negligence of website construction and validation as soon as they are executed, compromise the security of the system.
Risks and Impacts:
- A malicious file execution attack is risky in nature as the entire security of a computer system is at risk if such an attack takes place.
- The unethical data uploaded as a part of Malicious file execution attacks is very harmful as it aims to breach user privacy.
- Illegal content uploaded on websites is extremely dangerous which is done through this attack.
- Website contents may be manipulated or deleted depending on the motive of cyber attackers.
- Cyber attackers get access to the user/ organizational system and get access to sensitive information which they then modify, and delete according to their motive.
- For example consider a case of unethical content being uploaded on a website, which gives corrupts the security of the website and gives cyber attackers access to the website.
Prevention:
Listed below are some preventive measures which can be adopted to prevent malicious file execution attacks:
- Taking regular backups: Backups are a great source of maintaining the safety of files. When backups are taken regularly and timely, not only the data but the paths are also verified.
- Proper naming convention: Proper naming convention will ensure that overwriting of files does not take place by any chance and proper paths of file storage remain intact without modification.
- Proper virus scan of uploaded files: All the files that are to be uploaded should be properly checked for viruses so that no malicious file gets uploaded.
- Authenticating users: Users should be authenticated before uploading files, this way only verified users will be able to upload content on the websites.
- Allow proper extensions: Only Files with the desired extensions should be allowed for upload for ensuring the security of the computer network.
Conclusion:
Security from cyber attacks thus becomes important to have proper awareness and understanding of the cyber world and the various attacks which are executed by the cyber attackers in this cyber world. Malicious file execution cyber attack is very risky for both users and website owners should be aware of this attack and the preventive ways to deal with this form of cyber attack.




