In this article, we will learn about DNS Enumeration and the process of DNS enumeration with a practical approach.
Domain Name System(DNS) is nothing but a program that converts or translates a website name into an IP address and vice versa.
Example: A user enters www.geeksforgeeks.org in a browser, now the DNS will intercept this request and will fetch the corresponding IP address and connect the user to that fetched IP address.
DNS Enumeration is a technique used for Reconnaissance for better understanding of surface area of the Target systems(i.e. IP addresses).
- The process of DNS Enumeration returns various important information about the target like DNS record types, host names, IP addresses and much more depending upon the configuration of that target system.
- To perform DNS enumeration there are various open source tools, scripts available like Nmap, DNS recon etc.
Importance and Impacts:
Importance:
- It helps in discovering the various services and hosts that are running on the domain.
- It makes the target surface larger as we enumerate further.
- Furthermore, it exposes the critical information about the target.
Impact:
- The attacker can read about the system data and also can modify it.
- It can also lead to various other potential DNS attacks.
- It gives the Threat actor very critical details about the system that the attack can leverage to other attacks.
Steps of DNS Enumeration:
There are various tools to do DNS Enumeration, you are free to explore them by doing a simple web search about DNS Enumeration tools, but here we are going to use Nmap as an example:-
Nmap:
It is a tool used to discover host and services that are currently running of a computer network. Nmap provides an extensive Script by the name dns-nsec-enum.
Command Usage:
nmap -sSU -p 53 --script dns-nsec-enum - -script-args dns-nsec-enum.domains=example.com <target>
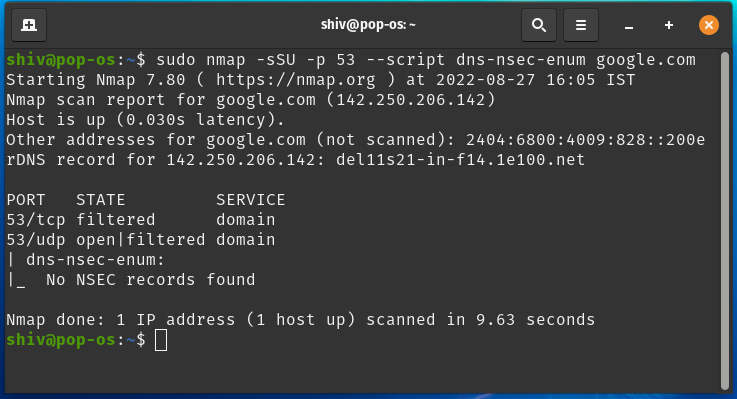
Output:
In the above result, we didn’t find any NSEC records, but you can try different other scripts like dns-brute. nse, dns-cache-snoop. nse, and dns-check-zone. nse for more DNS Enumeration.
Prevention:
- By restricting Zone Transfer by untrusted hosts.
- By auditing regularly the DNS record to avoid the availability of unused DNS record.
- Never that your private host remain private and doesn’t use public IP address.
Conclusion:
- DNS enumeration is very powerful for target mapping.
- You can simply do DNS Enumeration by your Linux or Windows terminal.
- DNS Enumeration exposes many attack surfaces.
- It is not possible to hide yourself from DNS Enumeration 100%.




