Cyber attacks are harmful attacks on the computer networking system which aim at exploiting user confidential information. Awareness and proper knowledge of cyber attacks can prevent cyber attackers from causing any harm to the computer networking systems.
DLL Hijacking:
- DLL Injection attacks aim to target active applications for injecting dynamic malicious code into the computer system through dynamic library.
- The aim of cyber attackers are achieved through pathway of attacks that load DLL into the secured, trusted applications.
- DLL Hijacking attack is carried out by attackers only for Microsoft Operating System.
Types of DLL Hijacking Attacks:
There are three different types of DLL Hijacking Attack. They are as follows:
- DLL Search Order Attack: Here, the order of search follows a definite pattern for DLL in Windows Operating System.
- DLL Side Loading Attack: Here, the affected target by DLL Attack is WinSxS directory.
- Phantom DLL Hijacking Attack: Here, old DLL are used as advantage for getting into the system. DLL names are used in Search and this helps in executing the new harmful code on computer systems.
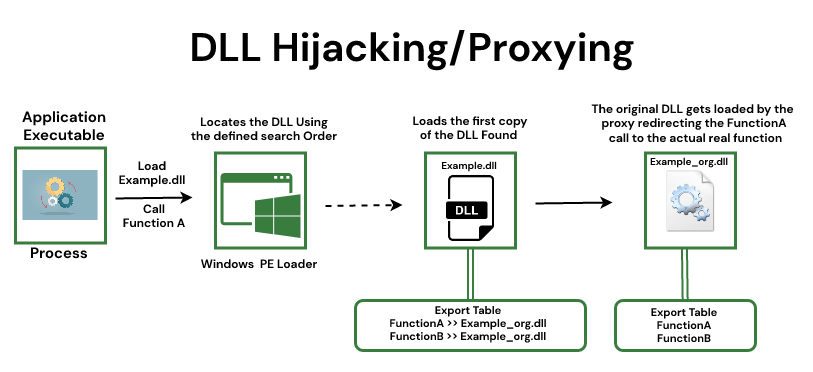
Steps to Find Missing DLL:
- The mechanism of DLL Hijacking involves hijacking the Dynamic Load Libraries by injecting harmful malicious code into the application.
- In this form of hijacking, the user unknowingly loads the malicious file into the computer system when the application loads.
- The infected malicious file in Dynamic Load Libraries (DLL) attack is placed within the perimeters of the application.
- Computer users who are unaware of this fact load the infected DLL file from the directly when the application is loaded. Hereby injecting or loading malicious code into the computer system.
- The infected malicious file is thus directly injected into the computer system, affecting the computer system security policies.
Escalating Privileges on DLL Attack:
- Cyber criminals gain unauthorized access to view, access, manipulate, steal and even delete user/ organization sensitive information.
- The unethical privileges are used by cyber criminals for tampering sensitive confidential information, which is fatal for users and organizations.
Prevention:
DLL Hijacking attacks can be prevented by taking care of the following preventive measures:
- Using third party advance tools: Special advanced tools are designed to prevent cyber attackers to inject harmful code to the system through DLL.
- Update Anti-virus regularly: Having a good quality antivirus and updating the antivirus regularly can help in preventing the hijackers from entering into the computer network system.
- Scan for harmful system vulnerabilities: Regularly monitoring the system vulnerabilities and having a strong defense mechanism can help in preventing vulnerabilities from falling a prey to cyber attackers.
- Enabling MFA Technique: Enabling of Multi-Factor Authentication (MFA) techniques better the security experience and help in reduction of DLL attacks by strengthening the security of the computer networking system.
- Phishing mails should be taken seriously: It is extremely dangerous to open phishing mails that can contribute to Dynamic Load Libraries (DLL) attack. Users must be very careful and should not be opening mails from unknown/ unauthorized senders.




