A banking Trojan is a piece of malware that is used primarily to steal banking credentials by remotely installing malicious software on a victim’s computer system. Banking Trojans are tailored to specific types of computers and may use the Windows registry for installation. On the infected computer, an icon will appear on the taskbar, causing a distraction from the user’s original task in order to trick them into providing login credentials for their bank account.
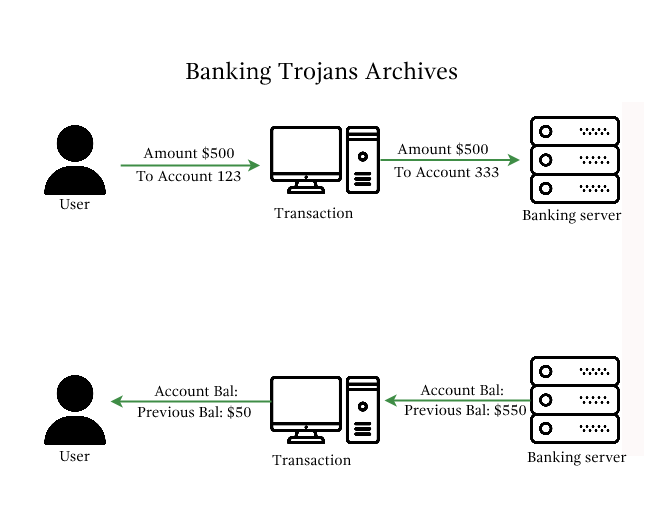
Trojans that affect financial institutions are often referred to as “malware” or “virus-type-of-malware”. This article aims to familiarize readers with these terms and describe how they trade off risk against reward when stealing personal information or threatening targeted users.
Due to its nature as a banking Trojan, Citadel is typically used by cyber criminals to download other types of malware onto the host computer to avoid being detected by an antivirus program. Certain forms of Citadel are able to infect a host computer through vulnerabilities with Adobe Flash Player.
Key Points:
- Banking Trojans are spread via emails or drive-by downloads on the Web. They are also attached to pirated software or can be included in corrupted USB drives that may have been passed around within a network.
- When banking Trojans attack networks and personal computers, they can severely damage their integrity and steal important data like customers’ sensitive information. According to a report by the security company Kaspersky, the total number of attacks made by banking Trojans has been growing since 2002. In 2015, there were more than 4 million attacks worldwide.
- When a computer is infected with a banking Trojan, the user does not know that their PC is compromised. A banking Trojan will usually be undetected until it steals information from the host computer or sends spam emails from it. Some forms of this malware can even disable antivirus programs and other security tools on the host computer in order to avoid detection.
- Banking Trojans are dangerous because they are able to infiltrate networks and may steal data from computers that are used to process credit card transactions. The United States has imposed strict requirements on payment processors to screen out fraudulent payments and prevent money laundering.
- Banking Trojans are often used for the purpose of theft and identity theft. They can also be used to steal banking information, monitor the host computer, and delete data on the host computer. Some forms of banking Malevolent programs can be configured to communicate directly with the attacker’s C&C server through a command-and-control structure.
- When a banking Trojan is installed, it will typically attempt to find certain files on the victim’s computer which are necessary in order for it to begin stealing sensitive data.
Countermeasures of banking Trojan:
- Widely, the most common method that banking Trojans used to install themselves is through malicious emails. Ordinary emails can be used as an infection vector for a variety of reasons, phishing is one common example.
- The phishing method in itself is not a threat and does not constitute a security issue per se, but it does provide an opportunity for malicious software to be installed on user systems, primarily computers belonging to individuals who have some limited access rights.
- Phishing emails are cleverly designed so that they look like they are coming from reputable companies or people, most often banks.




