Wireshark is a popular network tool that lets people see the traffic on the wire.In order to capture all of your data, you will need to open up your computer or laptop and plug it into a wired or wireless LAN (local area network) so Wireshark can get an image of that traffic.
Resolved Addresses:
Resolved addresses are IP and MAC Addresses that Wireshark has put on the packet, so it knows which computer to send the packet to many network administrators can look at the data sent over a network, but they may need Wireshark to see if there are any errors or abnormalities in their network environments. This is because, if there is something wrong with how data is being transmitted over the wires, a lot of computers could be affected. One computer could even crash because of these problems. However, this only happens when critical data is being improperly transmitted, and not everything can be sent critical all the time. Sometimes, a computer may receive data from another computer that is not supposed to be sent to the user. The reason behind this is that the user was not following proper e-mail etiquette and skipped past a junk email, or it was actually placed into an inappropriate folder by mistake. There are programs that can help you filter out these types of things, so you do not have any major issues later on down the line. With all kinds of issues, there are always ways to fix them. The one thing you will have to do with every packet captured by Wireshark is looking for its “A” address, which tells you where the packet originated from. Resolved Addresses in Wireshark.
- One-to-One Layer (LAN Only): If you only have one layer of IP addresses, and you’re using a subnet mask of 255.255.255.0, this means every packet will have 255 on the last octet or “A” address. This is because all of your data lives in one subnet or Network ID.
- One-to-Many Layer (LAN and ISP Router): If you have a LAN and ISP router, your data will be on both subnets. You would also need to take into consideration the “C” addresses, which are the IPs that connect your LAN to the Internet.
Steps to Open a Resolved Address Window:
Step 1: Select the packet you would like to view.
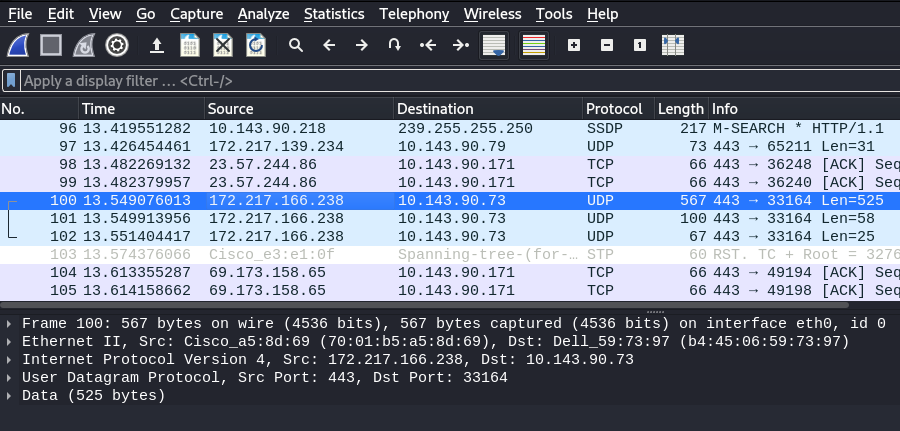
Step 2: Right-click and choose “Packet Details”.
Step 3: Expand the Ipv4 section.
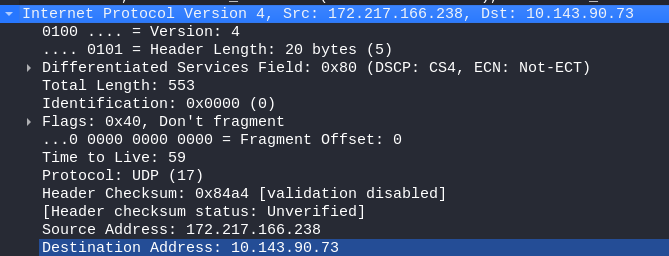
Step 4: Click on “Resolved” under Destination Address. (A new window will open.) * Inside this new window, double-click on the IP address that is listed under “Network IP.” This will open a new window listing all the different addresses that belong to this single IP address.* Double-click on one of them (such as 192.168). This will open a new window with more information about this IP address, such as which router it belongs to or what country it is in.
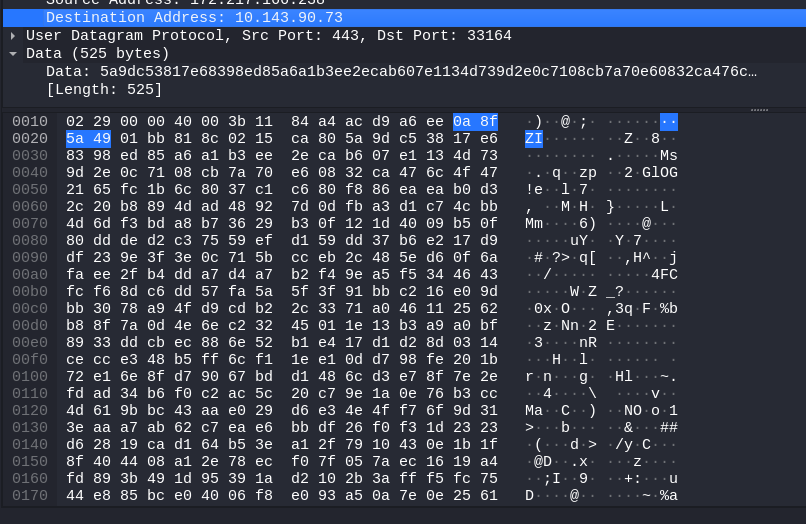
Step 5: Notice that the column for “Covered by” has a length of 0.
Step 6: Click on one of the other longer IP addresses. This will not have any information about it, since it is not a Resolvable address.
Step 7: Right-click and choose “View as Table.” This will open a new window and will list all the Resolved IPs in that window, including these three that are missing the “Covered by:” column.
Step 8: For each one of them, right-click and choose “Add to Columns” or “Resolve.” This will add information about this specific Ipv6 address to a new column called Covered By in your table.
Step 9: Copy and paste the whole table into a text file.
Step 10: Open a new window by right-clicking on the table and choosing “Packet Details,” then “Add Columns From File.” Add this text file to the bottom of your packet details window.
Step 11: If you want to export all data in your packet, right-click on a row of packets you would like to export, choose “Export Packet Data” and use that information. You could also simply copy and paste/cut and paste the entire IPv6 information into an email or document.
Key points:
- You can tell what address belongs to what computer or device by looking at the “A” address.
- As stated above, you can see the resolved addresses for each packet by clicking on the “Dump” button on the toolbar.
- If you want your network traffic to be sent in a preferred way, you will need to configure your router’s traffic shaper, which is also known as a “Layer 3 switch”.
- This is more advanced than most people will need, but it is very beneficial for networking because it will help your network run faster and smoother.
- One application of a traffic shaper is to help prevent ping flood attacks. A ping flood attack is when someone finds a hole in your network defenses and starts sending pings to your computers very rapidly.
- This can be dangerous because a lot of people will become flooded by this attack and their computers could crash and be unusable for an extended period of time.




