Cybersecurity is the most essential requirement for anybody and everybody connected with the internet. Internet and cybersecurity go hand in hand. Data that is available on the internet needs to be safe and secure for users and organizations to protect their privacy. Cybersecurity governs the best practices which can prevent hackers from unethically entering computer systems to steal information/ data. Unauthorized access to personal data is considered a breach of privacy, which is not acceptable under any law. Cybercrime is one serious crime.
Cyberattacks breach the security of computer networks and steal confidential data. It is very important to maintain proper cybersecurity so that cyberattacks can be prevented. Cybersecurity is the need of the hour. Awareness of cyber crimes and best security practices help in the timely identification of potential risks and their mitigation.
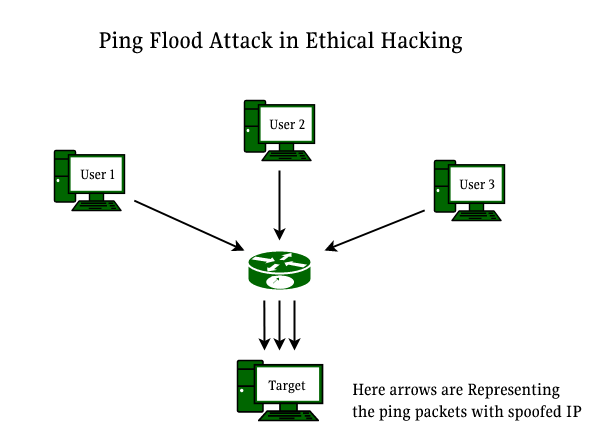
Ping Flood Attack:
- Ping flood attack also commonly called ICMP attack (Internet Control Message Protocol Attack) is a form of DOS attack.
- In a Ping flood attack, the computing device is flooded with tons of Internet Control Message Protocol ping requests.
- ICMP requests are used to check for the health status of networking devices and the connectivity between devices.
- Here, the tons of requests, which flood the computing device, make the target unreachable.
- Ping flood requests flood the target continuously, leaving no time for the target to respond back to the requests.
- The ping requests are ICMP echo requests that are extremely dangerous in nature as they aim at harming computers, causing Denial of Service.
Motive of Ping Flood Attacks:
- Ping flood attack aims at the target IP Address and floods the target with huge volumes of pings and calls.
- The over flooding of requests at the target makes the authenticated legitimate requests lose their purpose and ultimately get lost in the pool of requests.
- Ping flood attacks are dangerous attacks as these are generated by automatic bot servers.
- The target becomes unresponsive as there is a huge flood of requests that are suddenly recorded on the target, making the requests overwhelming.
Preventions from Ping Flood Attack:
Proper awareness about ping flood attacks will help in timely action to prevent damage to computers/servers. Below are the ways of Ping Flood (Internet Control Message Protocol) Attacks:
- Monitor the ICMP pings on the target device.
- If there are sudden peaks in requests or any suspicious activity sensed, report them immediately and take proper actions to detect the root cause.
- Secure your network by having a protected firewall in the computer network.
- A proper firewall ensures that harmful requests are blocked from entering the system and causing any harm to the computer/ server.
- Limit the number of ICMP messages and ping requests.
- Unnecessary pings and message requests shouldn’t be detected, as they may make the server/ computer unresponsive. Take care that ICMP messages/ requests are limited to prevent failure.




