Honeypots are computer applications that collect information from hackers and other criminals. They can be used from a physical or a virtual location, and come in many forms. Honeypots use a wide range of techniques to trap malicious activity and are primarily used in the information security industry. Hackers use honeypots to learn about vulnerabilities in their targets, as well as to understand how to exploit those vulnerabilities. Honeypots collect information about attacks, intrusions, and data stealing methods.
Installation Process:
Honeypots are useful tools when investigating hacker activity or conducting moles hunts for criminals attempting unauthorized access attempts against organizations’ computer systems. They’re easy enough to implement on Linux with demo applications below:
- We can install a honeypot on a Linux machine as well. Here we have shown using Pentox, which can be easily installed on Ubuntu.
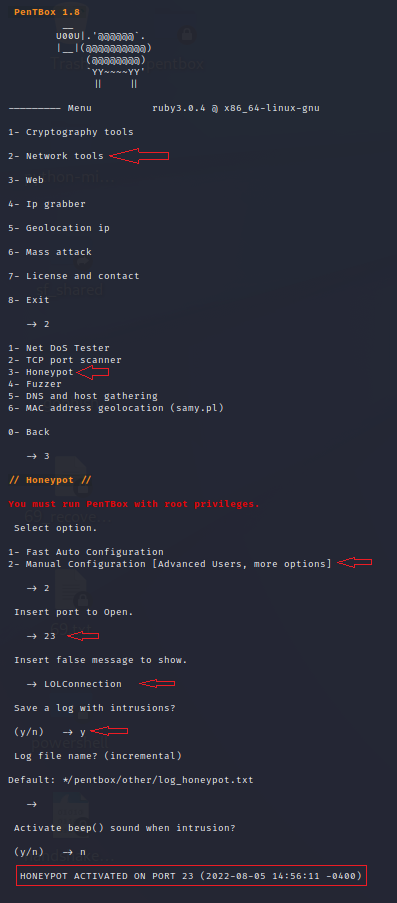
- Once it is installed, let us start using the paintbox. Select the network tools and honeypot from the menu to install the honeypot. Go with the manual configuration to install it according to your preferences for a honeypot.
- Now you can open the fake port as you wish and insert a fake message. You can also provide the ability to save the record and the record’s name. You can see the honeypot is enabled on the required port, and you can manually enable honeypots for other ports in a similar manner.
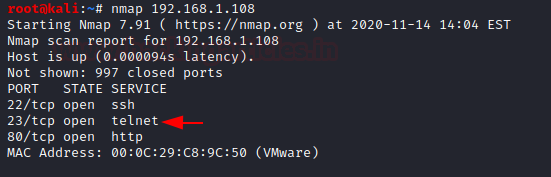
- Turn on the attacker’s machine and scan the host machine using Nmap. The results of the open ports and services are displayed below.
- Here, the attacker machine tries connecting with the host machine using telnet.
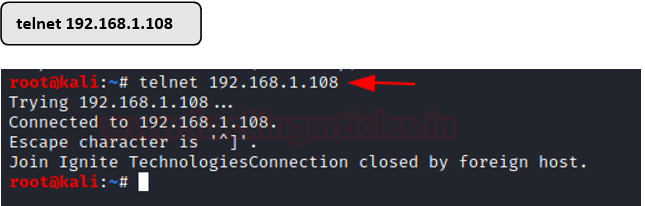
- For every attempt of intrusion that is made, it gets alerted, and a log is created where the attacker’s IP and port are recorded.
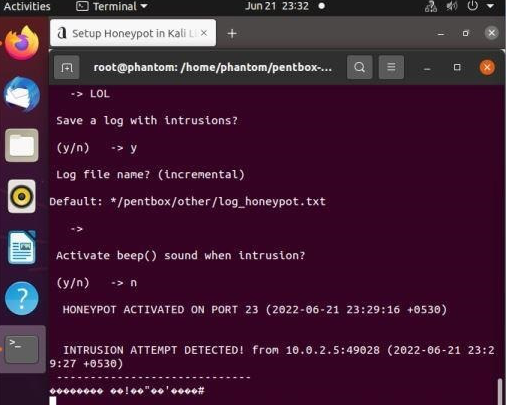
Conclusion:
This tool has a lot of other features that allow you to pull powerful tricks on people if you want. Always be careful about what you do on your cloud server. Consider security before doing anything. This will help you in the long run if you need to scale, store more sensitive data, and more.
Note: This article is only for educational purpose.




