With the ease of communication through networks, people become obsessed to share data over networks rather than physical forms and this attracted malicious attackers who want to steal users’ private and confidential data for various unethical purposes. These issues highlighted the need to make secure networks and for that, one needs to understand the network at the micro level. Hence, researchers launched Wireshark which is a network protocol analyzer for understanding communication, data transfer, troubleshooting, etc. IAX2 or Inter-Asterisk exchange 2 is an important protocol used by Asterisk which is a PBX server. Its main purpose was to provide VoIP connections either between servers or between clients and servers. One of the fabulous features of this protocol is that it can transfer any type of data with the help of UDP (User Datagram Protocol).
IAX2 Stream Analysis in Wireshark:
It is a window in Wireshark which is used to analyze the data stream of packets using the IAX2 protocol. It shows the statistics of captured packets through different fields like a forwarded stream and a reversed stream. For the ease of users, Wireshark provides graphs for detailed analysis. Data like VoIP calls between two devices, video streams, web content, etc. can be easily analyzed. This window is given under Telephony, see the below image:
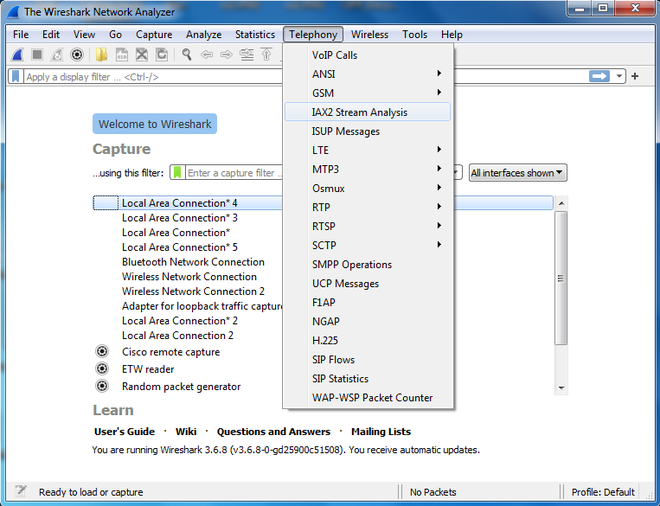
On clicking IAX2 Stream Analysis, a new window opens with various information fields which are as follows:
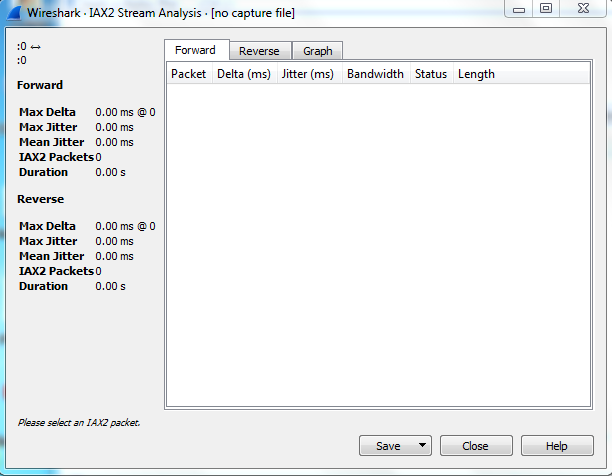
- Max Delta: The high value of Max delta is an indication of voice gaps if the captured data packets are of audio data transferred using VoIP.
- Max Jitter: It is used to describe the latency difference when packets travel from one end device to another device. Its value is must be below 30 ms.
- Mean Jitter: It is an indication of the average jitter value for captured data packets.
- IAX2 packets: This field is used to show the count of captured IAX2 packets.
- Duration: This field shows the time of captured IAX2 data packets.
- Bandwidth: It shows the bandwidth required for transferring IAX2 data packets.
- Status: This field shows the status of IAX2 data packets on hold, resent, received, etc.
- Length: It tells about the length of each data packet which mainly depends on the type of data sent like audio, video, plain text, etc.
All the above information about IAX2 packets can be saved for later use.
Captured Traffic:
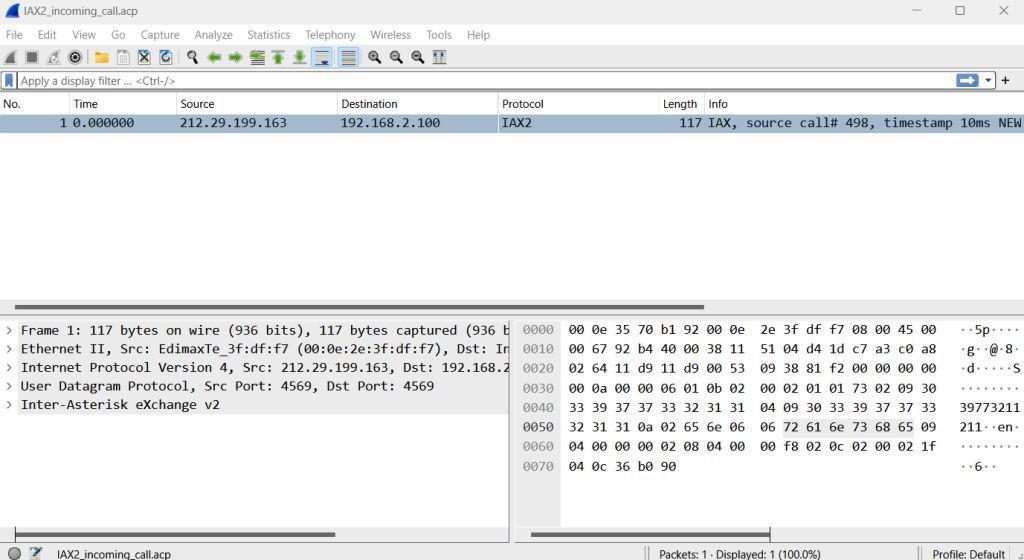
The above image shows the captured data packet of IAX2 protocol, source, and destination IP address can be easily found along with Length and other important information which can be seen under the Info tab. In the below windows source and destination port is also given.
Conclusion:
It can be concluded that the IAX2 protocol can be used to make voice calls, and it behaves like VoIP calls. Wireshark can sniff data packets of voice messages or calls that can be analyzed for different information like who is the sender and receiver, which ports are used for calls, timestamps, etc.




