Anonymous emailing is an interesting way to send a secret message that is hidden from the “sender’s” address. This is accomplished by using various methods to prevent the message’s origin, which can be traced back to you by anyone who has access to your computer. In this article, we will examine the different ways in which anonymous emailing works and show you how it can be used. Anonymity can only be achieved when all information about a particular message or group of messages is unidentifiable or redacted from the view of other persons involved with its dissemination. This will prevent the message from being traced back to the user’s computer. Anonymous emailing was first implemented on a large scale in 1994 by the Cypherpunks group, which used the anonymity software called Pretty Good Privacy (PGP) to send anonymous messages around the world. Cypherpunk is basically a term used to describe computer programmers who advocate for the widespread use of strong cryptography. The primary objective of this group was to ensure that personal privacy is protected, and that information cannot be intercepted or decrypted without authorized access. The following are methods involved with anonymous emailing:
- Anonymous remailers: It goes by many other names like mixmaster, remailer, or pseudonymous remailer. A remailer (short for the remote mailbox) is a computer system that allows messages to be relayed numerous times before reaching their final destination. The remailer could be located in a different physical location than the original sender, and therefore, can make tracing back to the original sender extremely difficult. This provides extra security.
- Internet Relay Chat (IRC): IRC is used as an anonymous remailer where emails are sent by users who do not wish to post their email address on public Internet services such as Yahoo! Groups or Usenet newsgroups. It stores messages sent by users in a channel and relays them from user to user until the final recipient reads them. The messages are then deleted from the server so that the actual users cannot be traced back.
- PGP (Pretty Good Privacy) and GnuPG (GNU Privacy Guard), use RSA encryption to encode email messages that cannot be decoded without a secret key. This will prevent anyone from breaking into the email message and tracing it back to the original sender.
- Tor onion routing network: Tor is free software for enabling online anonymity and obstructing web censorship. It also helps users reach websites that are forbidden in their areas, such as Facebook or YouTube.
Method of Sending Anonymous Emails:
Making anonymous emails and sending them through different methods is an admirable task for many computer users. The types of emails and their purpose vary from individual to individual. But the method of making anonymous emails is just the same for everyone, which is discussed in detail next.
First, a user has to open a web browser on an Internet-enabled computer and navigate to one of the anonymous email service providers online. Webpage (also known as Anonymous WWW), JAP (Java Anonymous Proxy), CryptoMutt, etc. After navigating to the provider’s website, the user can either create an account or log in to the existing one. The following steps should be followed in order to send or receive anonymous email from any anonymous emailing service provider:
- The user must install and configure their own email client (e.g. Outlook, Thunderbird, Eudora).
- They must choose their desired identity such as “Anonymous” or “anonymous.”
- After verifying and logging into their new Anonymous ID/E-mail, they can start sending anonymous emails without having to give any information about themselves besides their username/email address.
- They are allowed to send an unlimited number of messages using this method.
- They can create their own private anonymous web server to host or store the messages received with their anonymous ID.
Example:
Here is a tutorial example to send anonymous emails. Follow the given steps for sending anonymous emails.
- Step 1: Open your VPN and set up a virtual network (You can use any VPN proxy over your virtual network).
- Step 2: Open anonymousemail.me on your browser.
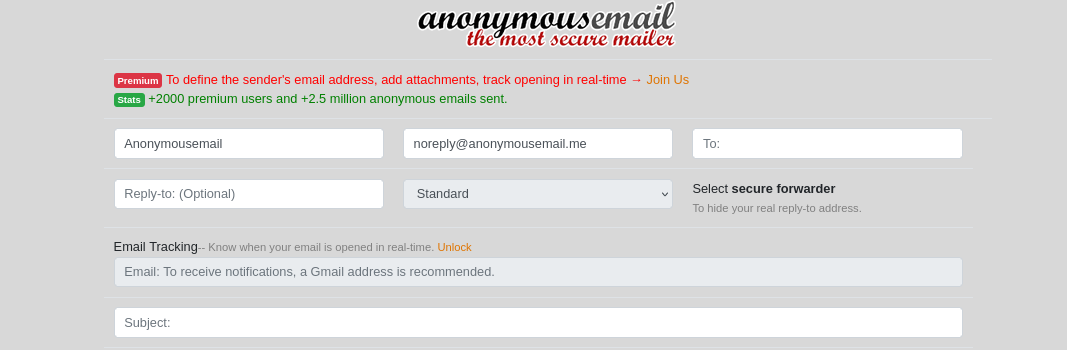
- Step 3: Enter the details on the website such as the receiver’s email and reply type, etc.
- Step 4: Enter the Subject and the main content in the below section of the website.
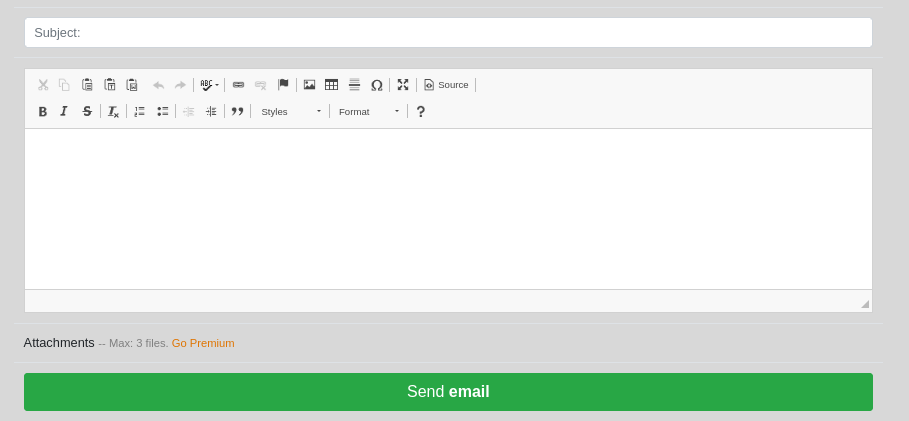
- Step 5: Now tap on the “Send Email” Button to send the email content to your victim.
Disadvantages:
- This is because several governments and centralized organizations do not allow anonymity in any way.
- This has become a social problem. On the other hand, many people have managed to give this method a different meaning which portrayed it in a different light. It has since become a social issue as well. Some cases that have caused issues for users include spamming, pornography spamming, hacking information posted online, and even credit card theft.
Conclusion:
The main reasons for anonymous emailing are confidentiality and integrity. These two terms make anonymous email a useful tool that helps in managing the overall email communication on the Internet. It is also used for other purposes, like participating in the elections without revealing your ID. Your identity remains hidden from everyone due to the encryption process involved with it. Furthermore, security analysts suggest that a person should communicate anonymously if they need to protect their sensitive data from third parties like hackers. It is also used to protect users’ identities when they are communicating with suspicious persons or companies online. Many people use this method to keep their private information secured on the Internet, thereby preventing any possible lawsuits or copyright infringement issues in the future.
Note: This tutorial is only for educational purpose.




