A Trojan virus, or Trojan malware, is actually malicious code or software that looks legitimate to the victim but can take full control over the victim’s computer. It is designed to steal, manipulate, disrupt, damage, or do some other destructive action on your data, network, and computer system. It seems like legitimate application software and deceives you into loading and executing the malware on your device. Once it is installed, it can start performing the activities it was designed for.
Signs of Trojan Infection :
- Devices become slower than usual – Since software infected with Trojans runs in the background, it consumes a lot of precious computational power and memory.
- Internet stops working – Sometimes hackers use the infected computers as Evil bots or zombies to take down servers. This will consume a lot of network resources due to which the speed of the internet slows down, or it stops working temporarily.
- Blue Screen of death or unfamiliar pop-ups and add-ons – If you try to run a software injected with trojan you might encounter an app causing a compatibility problem, the Blue Screen of Death is likely to happen at that time, or every time you launch the program. Sometimes trojans install programs that cause pop-up windows to appear on the screen.
- Weird icons and Unfamiliar applications – Trojans install software on your computer that can be used to get the credentials or any important data or use your computer like an Evil bot to attack others. These programs will not appear on the Desktop, Start menu, or Apps folder, but they continuously run in the background.
Safe Mode for Detecting Trojans:
A safe mode is a troubleshooting option for windows that starts the computer in a limited state. Only the basic files and the drivers necessary to run Windows are started. Therefore, if there are any trojans they can easily be spotted.
Steps to enter the Safe mode in Windows
- Search for “System Configuration” or just type “MSCONFIG” and click on run as administrator.
- In the System Configuration dialogue box, click on the “Boot” tab and then tick the Safe mode >> Network.
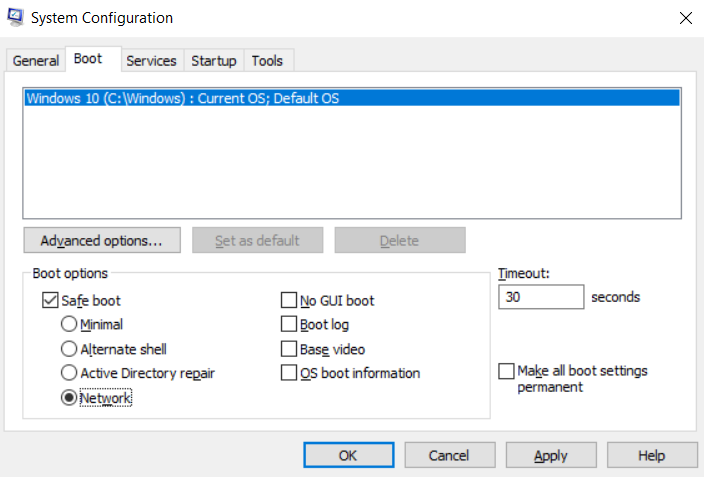
Windows System Configuration
- Click on apply and then ok to restart the Windows in safe mode.
- Now open the System Configuration box again and click on the “Startup” tab. Check for any suspicious files in the list. If you find something unusual remove it.
We must choose the “Safe Mode with Networking” option since that will allow us to download and update the tools if needed we need to fight off the trojan malware.
Deleting Temporary Files in Temp Folder:
The Temporary files are created by Windows or programs on your computer to hold data while a permanent file is being written or updated. The data will be transferred to a permanent file or written to the disk when the task gets complete, or when the program is closed.
Even after removing the trojans in the Windows Safe mode, their residuals might still be in the TEMP folder, which may cause a trojan to infect the device again. To access the TEMP folder type %temp% in the search bar and press enter. To get rid of the malicious files delete all the temporary files immediately.
Checking the Task Manager:
Check for the unwanted processes and programs on your PC and stop them immediately. Open the Task Manager and click on the “Processes” tab. Check for any unwanted processes and programs without verified publishers running actively. Click on it and end the process.
Using Anti-Virus Software:
Antivirus software is the best, easiest, and most reliable way to keep your device safe from all types of cybersecurity threats. Antiviruses are able to quickly detect and safely remove these threats from your devices. It will scan all the files on your computer as well as the files you download from the internet. It will also scan your file system periodically to detect and remove any malicious software on the computer. Some of the commonly used and reliable antivirus software available in the market are McAfee, Norton 360, TotalAV, Bitdefender etc.




