Blue bugging is a hacking technique. To understand it better, we need to know about hacking. Hacking refers to the use of someone’s device, personal documents, etc. without permission. Unauthorized computer access is an example of that. The person who owns access to all these activities is known as a hacker.
Bugging means to warehouse something secretly. Here, Blue bugging means to record or stole someone’s personal ethics without access. In Blue bugging, the hackers have all the access to mobile commands. An important factor of being caught by them is due to lack of awareness.
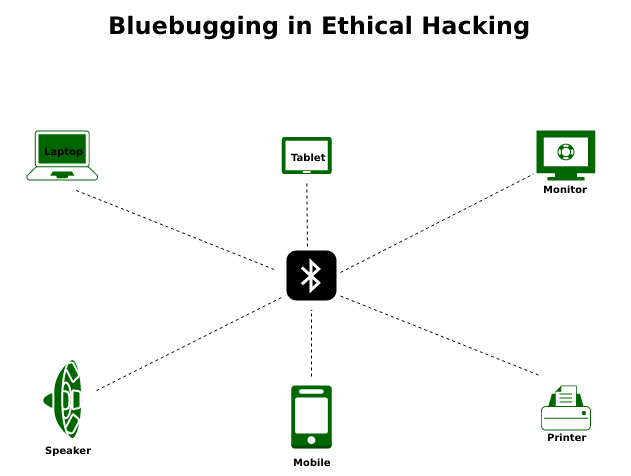
Blue bugging in Wireless Devices:
Blue bugging is a kind of Bluetooth attack. Wireless devices, i.e., Bluetooth-enabled mobile phones, are prone to Blue bugging by hackers. It is due to the discoverable mode in the default configuration. Once the attacker has access to the targeted device, he has full control of it.
For example, the hacker has access to phone calls, messages, and photos, and can send them to anyone without giving any information to the device owner. However, the hacker depends on the Bluetooth capability, as the attack range is limited due to Bluetooth connections (estimated 10 meters).
The most serious condition of this attack is that the target cell’s Bluetooth is on and in detectable mode. In this situation, the hacker first connects to the victim’s device.
Once the connection is established, the hacker will use it to install a backdoor on the victim’s device. Backdoors then exploit multiple security vulnerabilities, including remote code execution, and elevation of local privileges, and allow hackers to gain unauthorized access to the victim’s device. Due to the backdoor, the hacking device in the victim’s cell will continue to be identified as a trusted device. Hackers can also use this technique to enter AT commands on the victim’s phone to control the victim’s Bluetooth headset and perform malicious actions.
Protection from Blue Bugging:
- Turn off your Bluetooth: There is no need to connect your device to Bluetooth all the time, connect it only when you need it. If you’re on your Bluetooth all the time unnecessarily, you need to turn off that in order to protect your device. You can also make your device in non-discoverable mode.
- Update devices: Updating your device from time to time is a good practice for mobile safety. Also in the case of hacking and Blue bugging, it is more necessary. Older devices have Bluetooth discoverable by default. Newer mobile phones and systems have corrected this issue.
- Do not accept pairing requests from unknown contacts: If you are unknown from a connection, never accept their pairing request. They can even attract you by urgent seeming file or unsolicited contact. With your approval, they get access to all over data and can misuse it.
- Be aware of suspicious activities: If you recognize any abnormal activity that seems to be dangerous such as, connecting calls, sending messages even though you are not doing this, or looking like someone else is controlling it, you need to reset the factory settings and uninstall the dangerous and unwanted applications.