Application-level hijacking is one of the most popular ways hackers use to steal information. The attacker will modify the traffic and information being sent to a trusted application, then pretend the traffic came from a legitimate user. This type of attack is done on vulnerable web applications that do not use SSL to encrypt data. For this technique to work, attackers must find a vulnerability in a system that gives them control over requests going through the proxy server or man-in-the-middle (MITM) attack.
Proxy Hacking:
Proxy hacking is a method used by attackers to exploit a program’s internal functions by sending control commands to the proxy server. The proxy server is a program that forwards requests made by applications, but only if they’re within a specific scope. These programs have access to all network traffic as well as other computers on the network. This makes it easier for an attacker to gain access and compromise an entire network. An attacker can monitor, edit, or intercept traffic from systems outside the scope of the application. This gives them the ability to capture user credentials, modify data or exploit vulnerabilities on systems such as web servers and database servers.
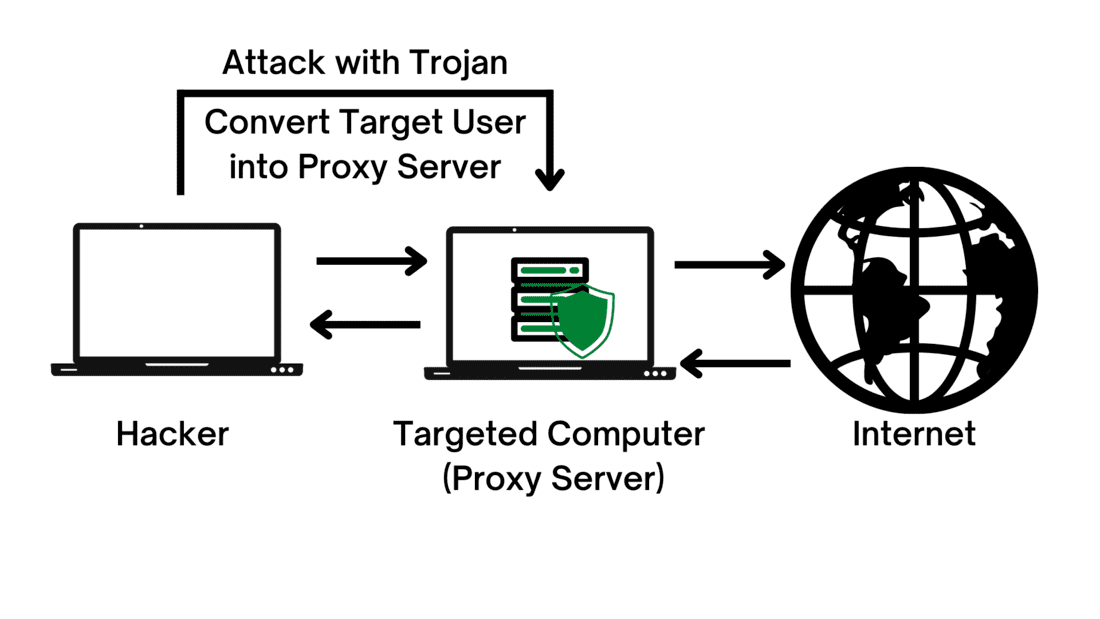
Scenario:
In this type of attack, the attacker uses a proxy server that has been hacked and connected to without the knowledge of the victim’s application. When an attacker is in place on the network and begins to monitor traffic, he can see where certain data is being sent to the website or server. The attacker then exploits this information by sending an HTTP request to modify or change data in some way.
Step 1: The attacker gathers information about the application or site from the target. This is done by using a proxy server to record all data going to and from the target site, including authentication details.
Step 2: Once an attacker gains access to a user’s details, he can then modify various parameters such as the user agent, user-name, password, session cookie ID or other important information that is sent to the server.
Step 3: In this step of the attack, an attacker will pretend to be a legitimate user and request a page on the application. The difference between the user-agent and the actual user-agent will be logged and sent to the attacker’s server.
Step 4: Using the obtained data, the attacker can now send a request through his proxy server. In this step, he’s telling the application that he is a legitimate user with a valid session and requesting information from its database.
Step 5: The attacker receives data as if he were a legitimate user because of the modified data that was sent in step 3. The data is sent to an element on his website or server, where it can be stored for future use or manipulated to obtain other sensitive information.
Conclusion:
In this article, we learned about proxy hacking, an attack method used to exploit an application-level hijack. This can be done on applications that don’t use SSL and are vulnerable to man-in-the-middle attacks. By sending a request through an attacker’s proxy server which can modify data, the attacker is able to get information from the target site and network. The attacker gains access to sensitive data such as user information, passwords, and session cookies which are sent in plain text. Because of this vulnerability, it’s always important for organizations to ensure their servers are always patched up-to-date and using SSL encryption.




