
If you’ve been following the jailbreak community as of late, then you’ve undoubtedly caught wind of Pwn20wnd’s plethora of recent announcements regarding the potential synergy between the unc0ver jailbreak tool and Brandon Azad’s yet-to-be-released tfp0 exploit.
Azad’s exploit was initially revealed to work on the iPhone 11 running iOS 13.3, and according to Pwn20wnd, it should also be viable on A12(X) devices and with all firmware versions between iOS 13.0-13.3. At the same time, Pwn20wnd cited three notable hurdles that would need to be dealt with if tweak injection was to work in the PAC-less implementation on iOS 13 via unc0ver.
The aforementioned exploit has yet to be officially released, but Pwn20wnd is already getting his ducks in a row. Early Friday morning, Pwn20wnd declared in a Tweet that at least one of those three substantial hurdles had been fixed and that it was the biggest issue of them all:
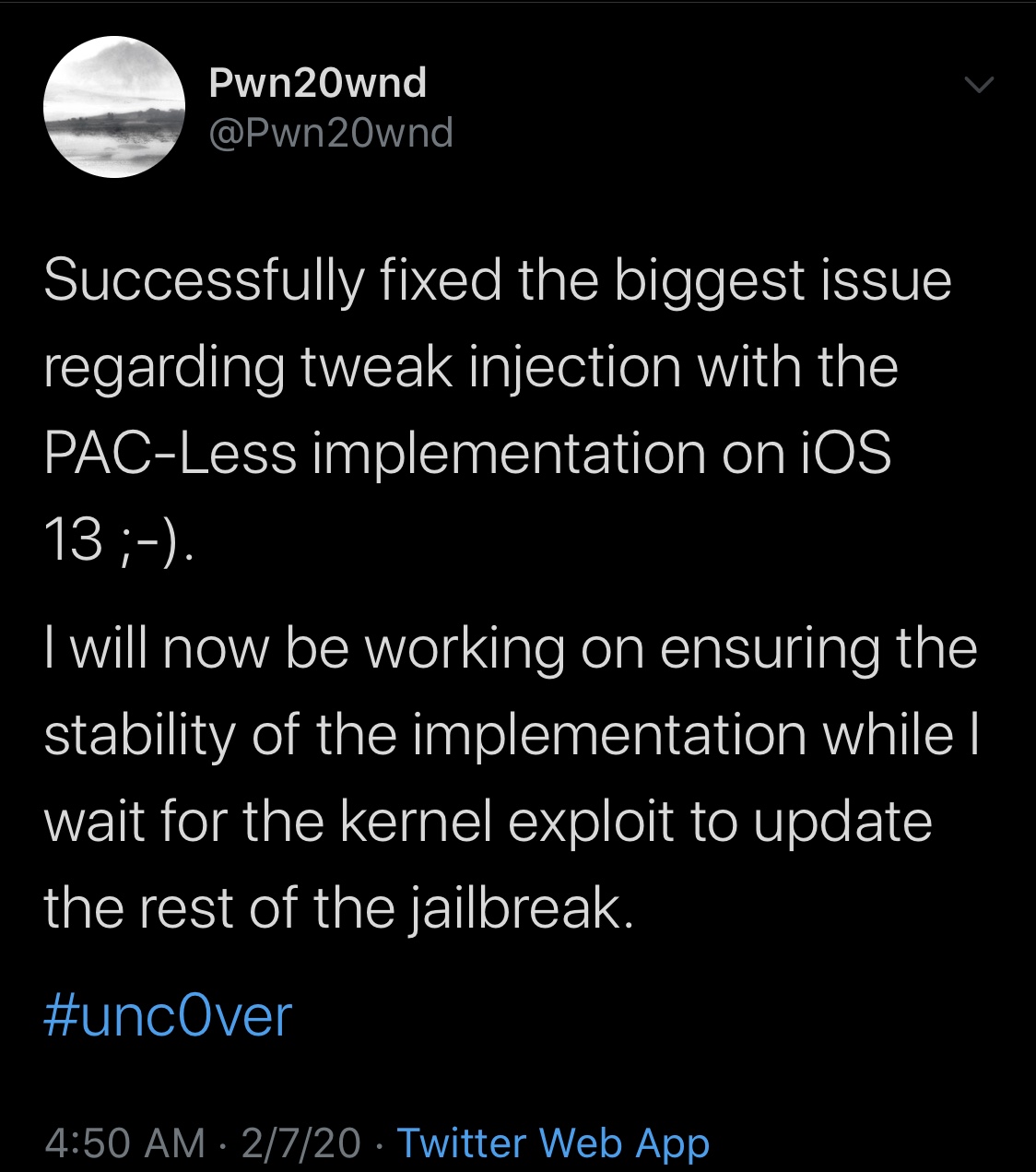
Albeit great news, we’re not out of the tunnel yet. Pwn20wnd’s hands are tied until Azad’s exploit is officially released, and this means that further development on unc0ver will have to wait until then. For now, Pwn20wnd can only focus on stabilizing the work he’s managed to accomplish thus far.
As they say, patience is a virtue. Then again, those anticipating a jailbreak on A12(X)-A13 can prepare their handsets by ensuring that they’re running iOS 13.3 before Apple closes the signing window. iOS 13.3 is still being signed at the time of this writing, which means that downgrading from iOS 13.3.1 is still possible; likewise, those using an older version of iOS 13 can upgrade to iOS 13.3 as long as the latter is being signed.
If you’re happily jailbroken on iOS 12 already, then you’re advised to stay where you are.
Are you excited about the progress Pwn20wnd has indicated so far? Discuss in the comments.




