
Pwn20wnd issued a build of the updated unc0ver jailbreak tool with support for Brandon Azad’s oob_timestamp tfp0 exploit on A12(X)-A13 running iOS 13.0-13.3 to internal beta testers earlier this week. While many anticipated a public beta launch shortly after all the positive comments shared by internal beta testers, a bug was later discovered that delayed any sort of public release.
Fortunately for those waiting to use the new unc0ver on their compatible device(s), patience is almost certainly a virtue. In a Tweet shared Friday evening by Pwn20wnd, we learn how the pesky bug that delayed the initial public release of the renewed unc0ver jailbreak tool had been resolved:
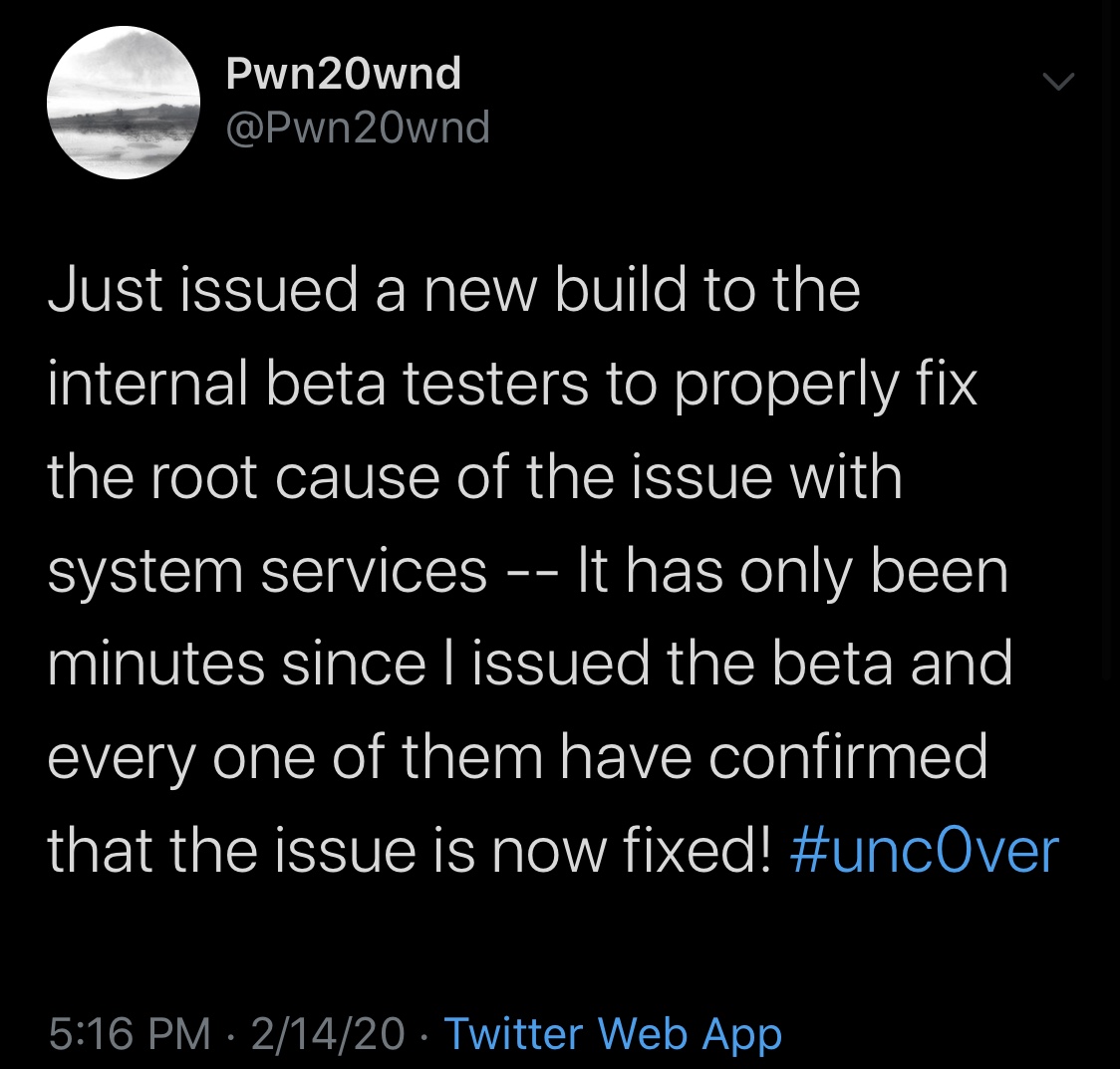
Aligning with Pwn20wnd’s announcement, internal beta testers soon began Tweeting their own testimonials:
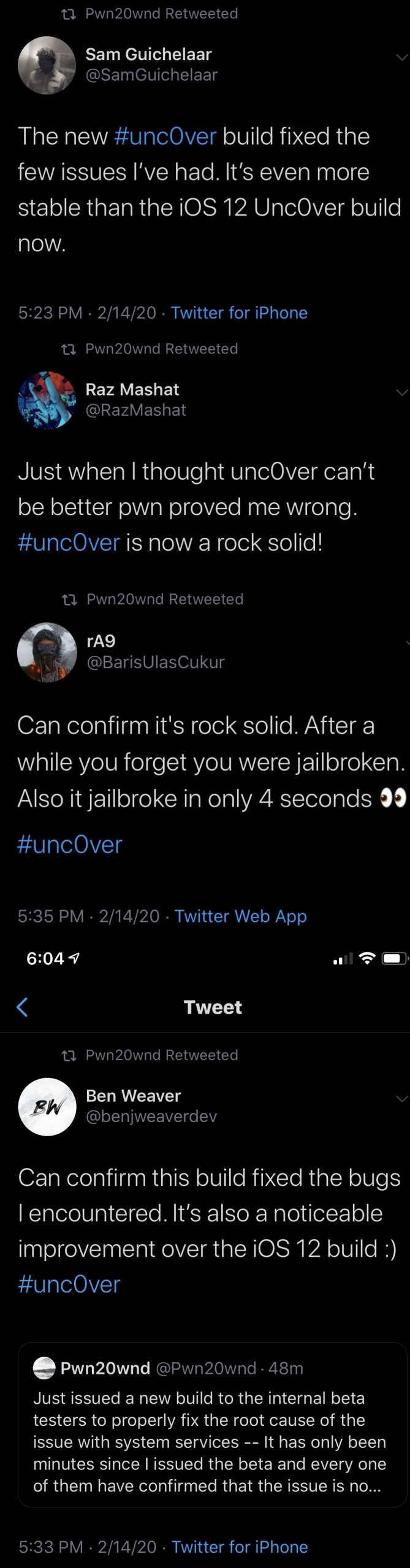
The latest internal unc0ver build at the time of this writing has been described by testers as “rock solid” and “more stable than the iOS 12 unc0ver build.” That said, similar comments were also shared shortly before the initial bug was found, and it remains to be seen if another bug will present itself before an official public release can be finalized.
Pwn20wnd hasn’t announced any sort of ETA for release, but it’s still splendid to see progress as the final kinks are worked out. Even if all the bugs can’t be worked out before a public beta launch, Pwn20wnd’s development history on unc0ver suggests that a series of micro-updates post-release would likely snuff out any remaining issues.
When released, the new unc0ver will not initially support iOS 13 devices that can be jailbroken with checkra1n. Pwn20wnd says that he wants to eventually make these devices compatible, but it isn’t a priority at this time given that there are other options available.
Are you pumped to use unc0ver for A12(X)-A13 on iOS 13.0-13.3? Discuss in the comments.




